At minimum 1,200 Redis databases servers worldwide have been corralled into a botnet using an “elusive and severe menace” dubbed HeadCrab since early September 2021.
“This sophisticated threat actor makes use of a state-of-the-artwork, custom-produced malware that is undetectable by agentless and traditional anti-virus alternatives to compromise a substantial range of Redis servers,” Aqua security researcher Asaf Eitani claimed in a Wednesday report.
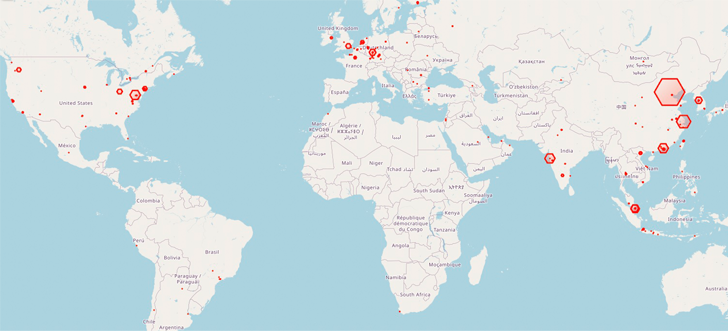
A sizeable focus of bacterial infections has been recorded in China, Malaysia, India, Germany, the U.K., and the U.S. to date. The origins of the risk actor are presently mysterious.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The conclusions appear two months just after the cloud security agency get rid of gentle on a Go-based malware codenamed Redigo that has been located compromising Redis servers.
The attack is designed to target Redis servers that are uncovered to the internet, followed by issuing a SLAVEOF command from a further Redis server that is previously under the adversary’s control.
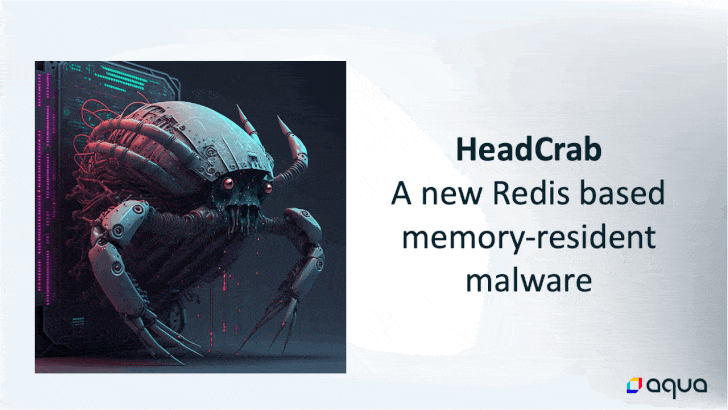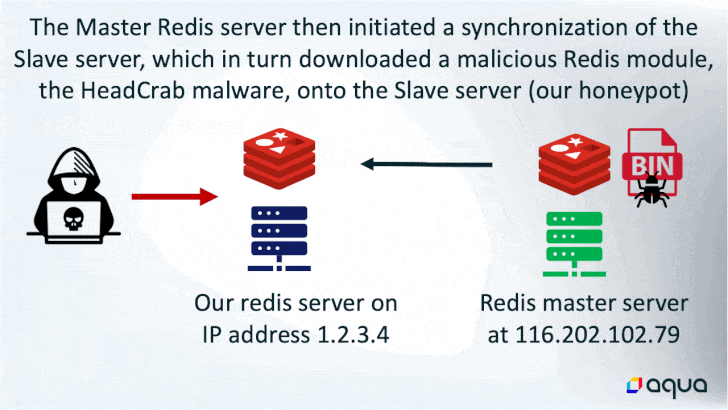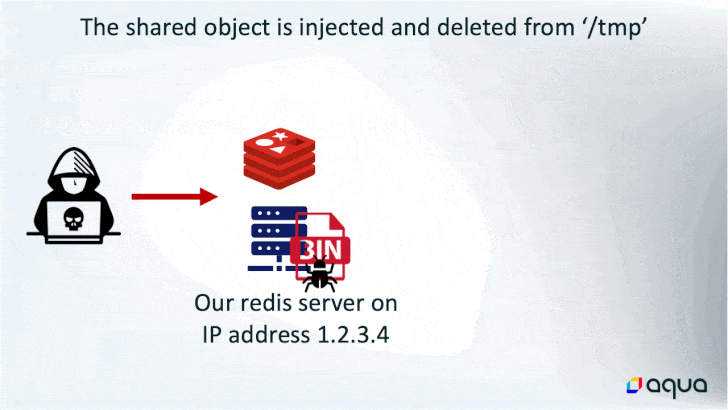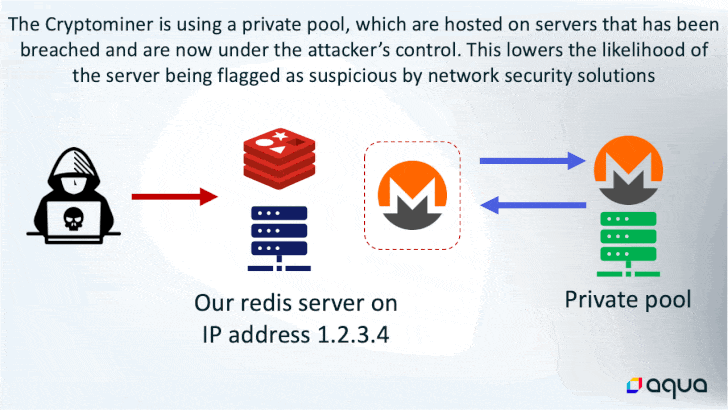
In performing so, the rogue “grasp” server initiates a synchronization of the recently hacked server to obtain the destructive payload, which incorporates the sophisticated HeadCrab malware.
“The attacker appears to be to primarily concentrate on Redis servers and has a deep understanding and abilities in Redis modules and APIs as demonstrated by the malware,” Eitani observed.
Even though the top stop goal of using the memory-resident malware is to hijack the method methods for cryptocurrency mining, it also features of several other options that permits the threat actor to execute shell instructions, load fileless kernel modules, and exfiltrate information to a remote server.
What is actually a lot more, a follow-on investigation of the Redigo malware has exposed it to be weaponizing the identical grasp-slave procedure for proliferation, and not the Lua sandbox escape flaw (CVE-2022-0543) as earlier disclosed.
Users are encouraged to chorus from exposing Redis servers immediately to the internet, disable the “SLAVEOF” aspect in their environments if not in use, and configure the servers to only accept connections from trustworthy hosts.
Eitani claimed “HeadCrab will persist in utilizing slicing-edge approaches to penetrate servers, possibly by exploiting misconfigurations or vulnerabilities.”
Discovered this write-up interesting? Comply with us on Twitter and LinkedIn to read extra exceptional written content we put up.
Some parts of this write-up are sourced from:
thehackernews.com


 Researchers Uncover New Bugs in Popular ImageMagick Image Processing Utility
Researchers Uncover New Bugs in Popular ImageMagick Image Processing Utility