The NuGet repository is the concentrate on of a new “innovative and very-destructive attack” aiming to infect .NET developer techniques with cryptocurrency stealer malware.
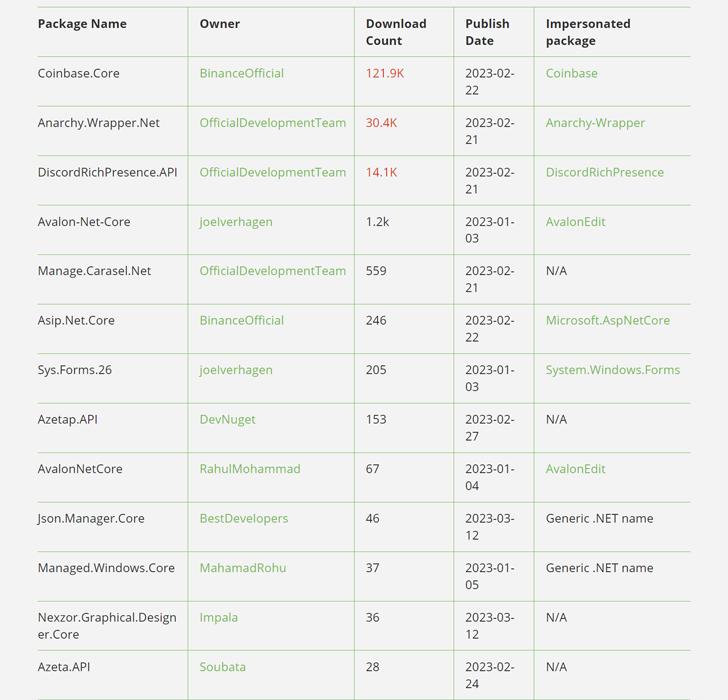
The 13 rogue offers, which were downloaded additional than 160,000 situations more than the previous thirty day period, have since been taken down.
“The packages contained a PowerShell script that would execute upon set up and cause a download of a ‘second stage’ payload, which could be remotely executed,” JFrog scientists Natan Nehorai and Brian Moussalli said.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Whilst NuGet packages have been in the past identified to consist of vulnerabilities and be abused to propagate phishing one-way links, the advancement marks the first-ever discovery of packages with destructive code.
A few of the most downloaded packages – Coinbase.Core, Anarchy.Wrapper.Net, and DiscordRichPresence.API – on your own accounted for 166,000 downloads, while it’s also possible that the danger actors artificially inflated the down load counts employing bots to make them look a lot more authentic.
The use of Coinbase and Discord underscores the ongoing reliance on typosquatting approaches, in which phony deals are assigned names that are identical to respectable deals, in order to trick builders into downloading them.
The malware included in just the software package packages functions as a dropper script and is developed to quickly run a PowerShell code that retrieves a comply with-on binary from a tricky-coded server.
As an additional obfuscation system, some offers did not embed a destructive payload directly, instead fetching it by means of another booby-trapped package deal as a dependency.
Even a lot more troublingly, the connection to the command-and-management (C2) server takes place about HTTP (as opposed to HTTPS), rendering it susceptible to an adversary-in-the-middle (AiTM) attack.
The 2nd-stage malware is what JFrog describes as a “fully personalized executable payload” that can be dynamically switched at will given that it’s retrieved from the C2 server.
WEBINARDiscover the Hidden Risks of 3rd-Party SaaS Applications
Are you mindful of the pitfalls affiliated with 3rd-party application access to your company’s SaaS apps? Sign up for our webinar to study about the kinds of permissions getting granted and how to lessen risk.
RESERVE YOUR SEAT
The 2nd-phase provides many capabilities that involve a crypto stealer and an auto-updater module that pings the C2 server for an current model of the malware.
The results appear as the software program supply chain has come to be an significantly rewarding pathway to compromise developers’ systems and stealthily propagate backdoored code to downstream customers.
“This proves that no open source repository is harmless from destructive actors,” Shachar Menashe, senior director at JFrog Security Analysis, said in a statement shared with The Hacker Information.
“.NET builders using NuGet are still at superior risk of malicious code infecting their environments and really should take warning when curating open up-supply components for use in their builds – and at each individual phase of the software package growth lifecycle – to make sure the software program provide chain stays protected.”
Observed this report intriguing? Abide by us on Twitter and LinkedIn to study more special written content we post.
Some pieces of this post are sourced from:
thehackernews.com


 New NAPLISTENER Malware Used by REF2924 Group to Evade Network Detection
New NAPLISTENER Malware Used by REF2924 Group to Evade Network Detection