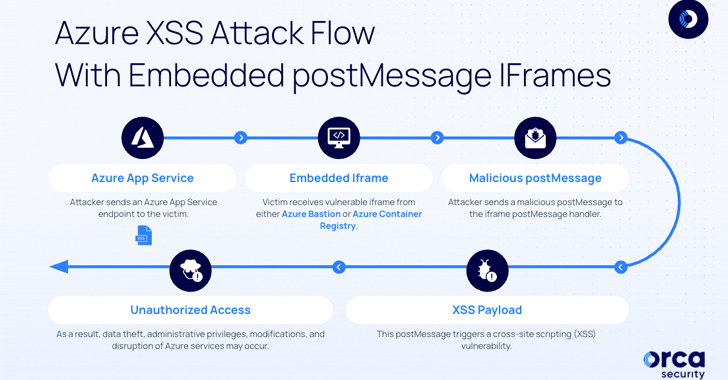
Two “risky” security vulnerabilities have been disclosed in Microsoft Azure Bastion and Azure Container Registry that could have been exploited to carry out cross-site scripting (XSS) attacks.
“The vulnerabilities authorized unauthorized accessibility to the victim’s session in the compromised Azure services iframe, which can guide to intense repercussions, like unauthorized details access, unauthorized modifications, and disruption of the Azure companies iframes,” Orca security researcher Lidor Ben Shitrit claimed in a report shared with The Hacker News.
XSS attacks acquire location when danger actors inject arbitrary code into an if not reliable website, which then receives executed each and every time when unsuspecting people visit the web-site.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The two flaws discovered by Orca leverage a weak spot in the postMessage iframe, which permits cross-origin interaction among Window objects.

This meant that the shortcoming could be abused to embed endpoints in distant servers utilizing the iframe tag and in the end execute malicious JavaScript code, primary to the compromise of delicate facts.
On the other hand, in purchase to exploit these weaknesses, a danger actor would have to conduct reconnaissance on various Azure solutions to single out vulnerable endpoints embedded in just the Azure portal that could have lacking X-Body-Possibilities headers or weak Material Security Procedures (CSPs).
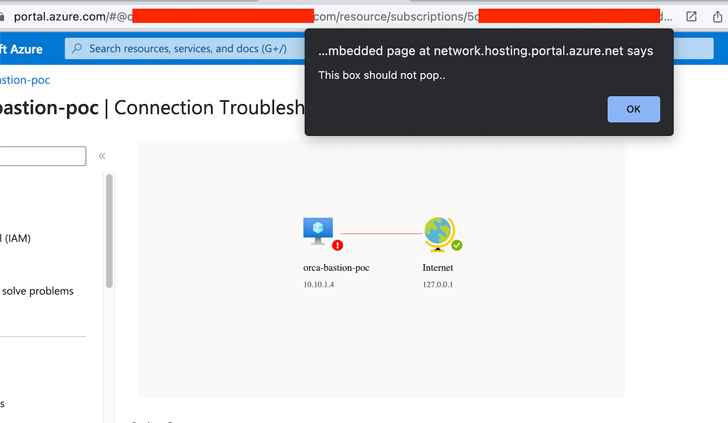
“As soon as the attacker productively embeds the iframe in a remote server, they commence to exploit the misconfigured endpoint,” Ben Shitrit discussed. “They focus on the postMessage handler, which handles distant functions this sort of as postMessages.”
By examining the respectable postMessages despatched to the iframe from portal.azure[.]com, the adversary could subsequently craft appropriate payloads by embedding the susceptible iframe in an actor-managed server (e.g., ngrok) and generating a postMessage handler that delivers the malicious payload.
Therefore when a victim is lured into visiting the compromised endpoint, the “malicious postMessage payload is delivered to the embedded iframe, triggering the XSS vulnerability and executing the attacker’s code inside the victim’s context.”
Impending WEBINAR🔐 Mastering API Security: Comprehending Your True Attack Area
Discover the untapped vulnerabilities in your API ecosystem and acquire proactive methods in direction of ironclad security. Be a part of our insightful webinar!
Sign up for the Session.wn-button,.wn-label,.wn-label:followingdisplay screen:inline-block.examine_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px good #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-best-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-ideal-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-sizing:13pxmargin:20px 0font-pounds:600letter-spacing:.6pxcolor:#596cec.wn-label:just afterwidth:50pxheight:6pxcontent:”border-best:2px solid #d9deffmargin: 8px.wn-titlefont-size:21pxpadding:10px 0font-fat:900text-align:leftline-height:33px.wn-descriptiontext-align:leftfont-size:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-dimension:15pxcolor:#fff!importantborder:0line-peak:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-fat:500letter-spacing:.2px
In a evidence-of-concept (PoC) demonstrated by Orca, a specially crafted postMessage was uncovered to be equipped to manipulate the Azure Bastion Topology Check out SVG exporter or Azure Container Registry Speedy Begin to execute an XSS payload.
Pursuing liable disclosure of the flaws on April 13 and Might 3, 2023, Microsoft rolled out security fixes to remediate them. No additional action is necessary on the aspect of Azure customers.
The disclosure comes additional than a thirty day period after Microsoft plugged three vulnerabilities in the Azure API Management support that could be abused by malicious actors to gain accessibility to delicate facts or backend products and services.
Discovered this post fascinating? Observe us on Twitter and LinkedIn to examine much more special articles we write-up.
Some sections of this report are sourced from:
thehackernews.com

 EU Passes Landmark Artificial Intelligence Act
EU Passes Landmark Artificial Intelligence Act