A malicious extension for Chromium-centered web browsers has been noticed to be dispersed by using a very long-standing Windows information and facts stealer identified as ViperSoftX.
Czech-primarily based cybersecurity corporation dubbed the rogue browser incorporate-on VenomSoftX owing to its standalone characteristics that help it to accessibility web page visits, steal qualifications and clipboard knowledge, and even swap cryptocurrency addresses by using an adversary-in-the-middle (AiTM) attack.
ViperSoftX, which initially arrived to light in February 2020, was characterized by Fortinet as a JavaScript-dependent remote access trojan and cryptocurrency stealer. The malware’s use of a browser extension to advance its details-accumulating ambitions was documented by Sophos threat analyst Colin Cowie before this calendar year.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“This multi-stage stealer displays fascinating hiding abilities, hid as compact PowerShell scripts on a solitary line in the center of normally innocent-searching large log documents, among many others,” Avast researcher Jan Rubín explained in a specialized create-up.
“ViperSoftX focuses on stealing cryptocurrencies, clipboard swapping, fingerprinting the contaminated equipment, as properly as downloading and executing arbitrary extra payloads, or executing commands.”
The distribution vector applied to propagate ViperSoftX is usually achieved by cracked application for Adobe Illustrator and Microsoft Place of work that are hosted on file-sharing web sites.
The downloaded executable file will come with a clean variation of cracked program together with more information that established up persistence on the host and harbor the ViperSoftX PowerShell script.
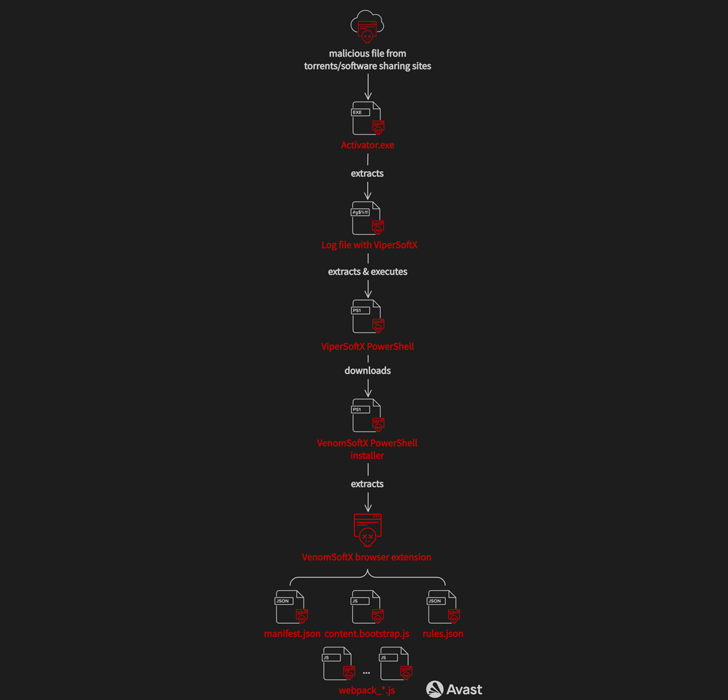
More recent variants of the malware are also capable of loading the VenomSoftX incorporate-on, which is retrieved from a remote server, to Chromium-based browsers this kind of as Google Chrome, Microsoft Edge, Opera, Courageous, and Vivaldi.
This is accomplished by looking for LNK files for the browser purposes and modifying the shortcuts with a “–load-extension” command line switch that factors to the path where by the unpacked extension is stored.
“The extension tries to disguise by itself as perfectly recognised and prevalent browser extensions this sort of as Google Sheets,” Rubín discussed. “In truth, the VenomSoftX is still one more information and facts stealer deployed on to the unsuspecting sufferer with complete entry permissions to every single web page the person visits from the infected browser.”
It can be worthy of noting that the –load-extension tactic has also been put to use by an additional browser-based mostly info stealer referred to as ChromeLoader (aka Choziosi Loader or ChromeBack).
VenomSoftX, like ViperSoftX, is also orchestrated to steal cryptocurrencies from its victims. But contrary to the latter, which functions as a clipper to reroute fund transfers to an attacker-controlled wallet, VenomSoftX tampers with API requests to crypto exchanges to drain the digital property.
Companies targeted by the extension include Blockchain.com, Binance, Coinbase, Gate.io, and Kucoin.
The development marks a new level of escalation to traditional clipboard swapping, though also not elevating any speedy suspicion as the wallet deal with is replaced at a much a lot more basic amount.
Avast explained it has detected and blocked around 93,000 bacterial infections given that the start out of 2022, with a greater part of the impacted end users situated in India, the U.S., Italy, Brazil, the U.K., Canada, France, Pakistan, and South Africa.
An examination of the tricky-coded wallet addresses in the samples reveals that the operation has netted its authors a sum complete of about $130,421 as of November 8, 2022, in several cryptocurrencies. The collective monetary acquire has considering that dropped to $104,500.
“Considering that the transactions on blockchains/ledgers are inherently irreversible, when the user checks the transaction historical past of payments afterward, it is by now way too late,” Rubín stated.
Identified this article appealing? Follow THN on Facebook, Twitter and LinkedIn to examine a lot more special information we post.
Some components of this posting are sourced from:
thehackernews.com


 US Takes Down Domains Used in ‘Pig Butchering’ Cryptocurrency Scheme
US Takes Down Domains Used in ‘Pig Butchering’ Cryptocurrency Scheme