Intelligence companies in the U.K. and the U.S. disclosed aspects of a new botnet malware referred to as Cyclops Blink which is been attributed to the Russian-backed Sandworm hacking team and deployed in attacks relationship back again to 2019.
“Cyclops Blink seems to be a replacement framework for the VPNFilter malware uncovered in 2018, which exploited network devices, principally tiny business/household business office (SOHO) routers, and network-attached storage (NAS) equipment,” the agencies explained. “In widespread with VPNFilter, Cyclops Blink deployment also seems indiscriminate and popular.”
The joint authorities advisory comes from the U.K. Countrywide Cyber Security Centre (NCSC), the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI) in the U.S.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Sandworm, aka Voodoo Bear, is the identify assigned to a really sophisticated adversary working out of Russia that is regarded to be lively because at the very least 2008. The hacking team has exhibited a distinct focus on targeting entities in Ukraine and is alleged to be behind the Ukrainian energy sector attacks that triggered common electrical power outages in late 2015.
The threat actor, in Oct 2020, was formally joined to Russia’s Typical Personnel Key Intelligence Directorate (GRU) Most important Centre for Special Systems (GTsST) armed forces unit 74455.
VPNFilter was to start with documented by Cisco Talos in May 2018, describing it as a “complex modular malware procedure” that shares overlaps with the Sandworm’s BlackEnergy malware and attributes abilities to assist intelligence-assortment and destructive cyber attack functions.
The IoT botnet malware was uncovered to have compromised much more than 500,000 routers in at the very least 54 nations around the world, concentrating on units from Linksys, MikroTik, NETGEAR, and TP-Website link, ASUS, D-Hyperlink, Huawei, Ubiquiti, QNAP, UPVEL, and ZTE.
That very same month, the U.S. government declared the seizure and takedown of a vital internet area utilised for the attacks, urging owners of SOHO and NAS appliances that might be infected to reboot their units to quickly disrupt the malware.
As of January 2021, an investigation from Pattern Micro determined “residual infections” nevertheless remaining on hundreds of networks yrs immediately after sinkholing VPNFilter, even as the Sandworm actor concurrently opted to retool the malware in reaction to general public disclosures.
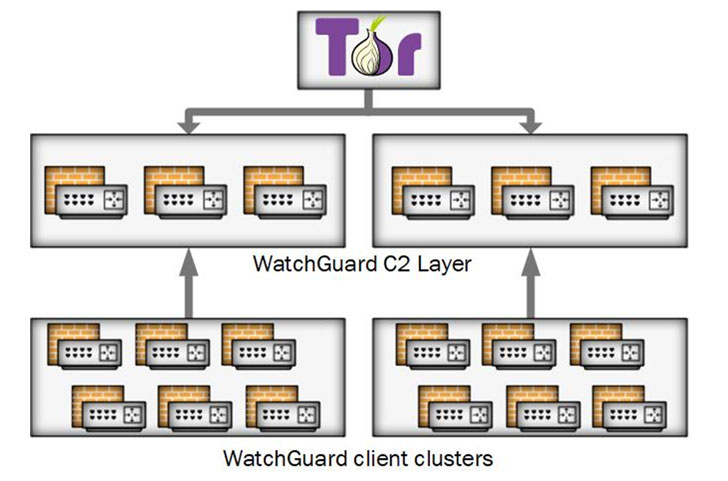
Cyclops Blink, as the substitute is called, is believed to have been in motion considering the fact that at the very least June 2019 mainly environment its eyes on WatchGuard firewall units, even though the agencies claimed that the malware could be repurposed to strike other architectures and firmware.
Even extra concerningly, the botnet malware is deployed as a bogus update and is able of surviving reboots and firmware upgrades, with command-and-control (C2) communications facilitated about the Tor anonymity network.
“The malware by itself is complex and modular with primary core functionality to beacon unit data again to a server and enable information to be downloaded and executed,” the researchers mentioned. “There is also operation to add new modules even though the malware is running, which lets Sandworm to implement more ability as needed.”
WatchGuard, in an independent bulletin, known as it a point out-sponsored botnet that leveraged a earlier recognized security vulnerability in the Firebox firmware as the preliminary entry vector. The shortcoming was ultimately tackled as of Might 2021.
“Based on present-day estimates, Cyclops Blink may possibly have impacted somewhere around 1% of lively WatchGuard firewall appliances,” the organization explained. “Only all those appliances that experienced been configured to have administration open up to the Internet are susceptible to Cyclops Blink.”
The Seattle-headquartered company is also recommending clients to quickly adhere to the ways outlined in the 4-Move Cyclops Blink Prognosis and Remediation Plan to diagnose and get rid of the menace posed by opportunity malicious action from the botnet.
The conclusions come as Russia formally introduced a total scale military operation to invade Ukraine, just as its IT infrastructure was crippled by a string of info wiper and dispersed denial-of-provider (DDoS) attacks.
Uncovered this article interesting? Stick to THN on Fb, Twitter and LinkedIn to browse extra special material we publish.
Some sections of this report are sourced from:
thehackernews.com



 UK Launches Free Cyber Skills Training for Secondary School Pupils
UK Launches Free Cyber Skills Training for Secondary School Pupils