A cybercrime team known as Vice Culture has been linked to many ransomware strains in its destructive campaigns aimed at the education and learning, federal government, and retail sectors.
The Microsoft Security Danger Intelligence staff, which is tracking the risk cluster under the moniker DEV-0832, claimed the group avoids deploying ransomware in some cases and instead most likely carries out extortion making use of exfiltrated stolen facts.
“Shifting ransomware payloads about time from BlackCat, Quantum Locker, and Zeppelin, DEV-0832’s hottest payload is a Zeppelin variant that contains Vice Society-unique file extensions, such as .v-s0ciety, .v-society, and, most a short while ago, .locked,” the tech giant’s cybersecurity division explained.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Vice Culture, active given that June 2021, has been steadily observed encrypting and exfiltrating victim knowledge, and threatening corporations with exposure of siphoned information and facts to strain them into paying a ransom.
“Unlike other RaaS (Ransomware-as-a-Services) double extortion teams, Vice Culture focuses on obtaining into the victim system to deploy ransomware binaries bought on Dark web discussion boards,” cybersecurity business SEKOIA claimed in an assessment of the team in July 2022.
The financially enthusiastic danger actor is known to depend on exploits for publicly disclosed vulnerabilities in internet-going through applications for original accessibility, whilst also making use of PowerShell scripts, repurposed genuine resources, and commodity backdoors these kinds of as SystemBC prior to deploying the ransomware.
Vice Culture actors have also been spotted leveraging Cobalt Strike for lateral motion, in addition to making scheduled duties for persistence and abusing vulnerabilities in Windows Print Spooler (aka PrintNightmare) and Typical Log File Technique (CVE-2022-24521) to escalate privileges.
“Vice Culture actors attempt to evade detection by means of masquerading their malware and resources as reputable data files, making use of method injection, and most likely use evasion tactics to defeat automated dynamic assessment,” the U.S. Cybersecurity and Infrastructure Security Agency (CISA) stated very last month.
In a person July 2022 incident disclosed by Microsoft, the menace actor is mentioned to have tried to at first deploy QuantumLocker executables, only to stick to it up with suspected Zeppelin ransomware binaries five several hours later on.

“These types of an incident may well recommend that DEV-0832 maintains several ransomware payloads and switches dependent on concentrate on defenses or, alternatively, that dispersed operators operating less than the DEV-0832 umbrella could possibly retain their personal most popular ransomware payloads for distribution,” Redmond famous.
Amid other equipment used by DEV-0832 is a Go-based backdoor known as PortStarter that features the functionality to change firewall settings and open ports to set up connections with pre-configured command-and-management (C2) servers.
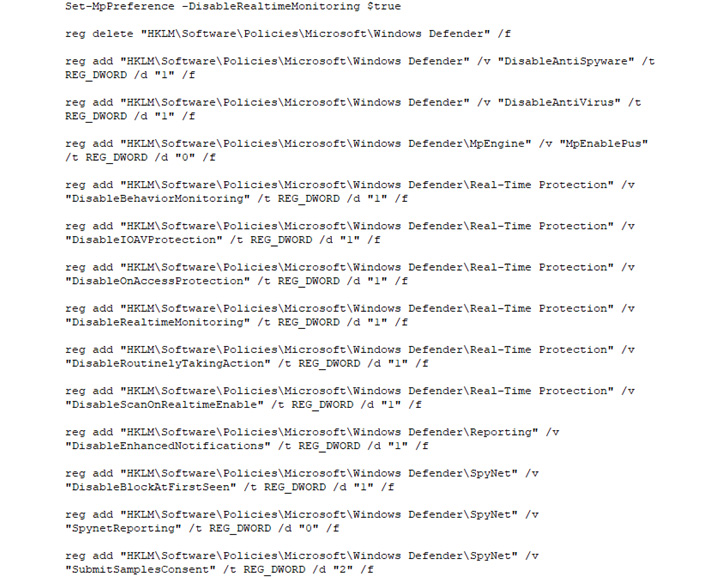
Vice Culture, aside from having advantage of dwelling-off-the-land binaries (LOLBins) to operate destructive code, has also been identified making an attempt to turn off Microsoft Defender Antivirus utilizing registry commands.
Details exfiltration is finally achieved by launching a PowerShell script that transmits large-ranging sensitive data, ranging from fiscal documents to healthcare details, to a difficult-coded attacker-owned IP handle.
Redmond further more pointed out that the cybercrime group focuses on businesses with weaker security controls and a higher chance of a ransom payout, underscoring the require to use important safeguards to protect against this sort of attacks.
“The change from a ransomware as a support (RaaS) featuring (BlackCat) to a ordered wholly-owned malware supplying (Zeppelin) and a tailor made Vice Culture variant indicates DEV-0832 has energetic ties in the cybercriminal financial state and has been screening ransomware payload efficacy or post-ransomware extortion possibilities,” Microsoft explained.
Identified this write-up exciting? Comply with THN on Facebook, Twitter and LinkedIn to go through additional exclusive articles we article.
Some components of this short article are sourced from:
thehackernews.com


 Hackers Actively Exploiting Cisco AnyConnect and GIGABYTE Drivers Vulnerabilities
Hackers Actively Exploiting Cisco AnyConnect and GIGABYTE Drivers Vulnerabilities