A now-patched security flaw in Apple’s iOS and macOS operating techniques could have possibly enabled applications with Bluetooth obtain to eavesdrop on discussions with Siri.
Apple stated “an application may be equipped to document audio working with a pair of connected AirPods,” including it resolved the Core Bluetooth issue in iOS 16.1 with improved entitlements.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Credited with getting and reporting the bug in August 2022 is app developer Guilherme Rambo. The bug, dubbed SiriSpy, has been assigned the identifier CVE-2022-32946.
“Any app with entry to Bluetooth could history your conversations with Siri and audio from the iOS keyboard dictation feature when working with AirPods or Beats headsets,” Rambo explained in a produce-up.
“This would materialize without the application requesting microphone entry permission and with no the app leaving any trace that it was listening to the microphone.”
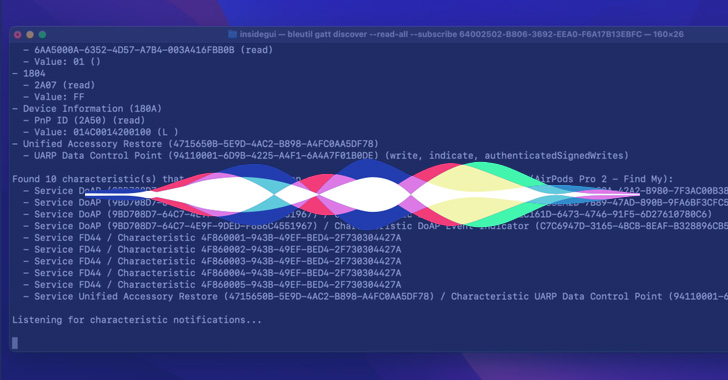
The vulnerability, according to Rambo, relates to a assistance known as DoAP that’s provided in AirPods for Siri and Dictation aid, therefore enabling a malicious actor to craft an app that could be linked to the AirPods via Bluetooth and file the audio in the qualifications.
This is compounded by the truth that “there is no ask for to obtain the microphone, and the sign in Control Center only lists ‘Siri & Dictation,’ not the app that was bypassing the microphone authorization by talking instantly to the AirPods around Bluetooth LE.”
While the attack requires that the app has entry to Bluetooth, this restriction can be trivially bypassed as users granting Bluetooth entry to the application are not likely to be expecting that it could also open the doorway to accessing their conversations with Siri and audio from dictation.
On macOS, nonetheless, the exploit could be abused to realize a full bypass of the Transparency, Consent and Command (TCC) security framework, meaning any app can report conversations with Siri without the need of requesting for any permissions in the to start with place.

Rambo reported the cause for this behavior is owing to the lack of entitlement checks for BTLEServerAgent, the daemon assistance dependable for managing DoAP audio.
A program patch remediating this flaw is readily available for iPhone 8 and later, iPad Pro (all models), iPad Air 3rd era and later, iPad 5th generation and later, and iPad mini 5th era and later. It has also been resolved in all supported versions of macOS.
The iOS 16.1 update, which was produced on Oct 24, 2022, arrives with fixes for a total of 20 flaws, together with a Kernel vulnerability (CVE-2022-42827) that it disclosed as being actively exploited in the wild.
Identified this report intriguing? Stick to THN on Fb, Twitter and LinkedIn to read through much more special material we post.
Some areas of this post are sourced from:
thehackernews.com


 White House Launches Chemical Sector Security Sprint
White House Launches Chemical Sector Security Sprint