U.S. and Bulgarian authorities this week took command of the dark web internet site utilised by the NetWalker ransomware cybercrime team to publish info stolen from its victims.
“We are placing again from the developing danger of ransomware by not only bringing legal expenses towards the responsible actors, but also disrupting prison on the web infrastructure and, where ever feasible, recovering ransom payments extorted from victims,” mentioned Acting Assistant Attorney Basic Nicholas L. McQuaid of the Justice Department’s Criminal Division.
“Ransomware victims should know that coming ahead to legislation enforcement as before long as possible soon after an attack can direct to major success like those people accomplished in today’s multi-faceted operation.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
In link with the takedown, a Canadian nationwide named Sebastien Vachon-Desjardins from the city of Gatineau was billed in the U.S. condition of Florida for extorting $27.6 million in cryptocurrency from ransom payments.

Individually, the Bulgarian Countrywide Investigation Services and General Directorate Combating Organized Criminal offense seized a dark web hidden resource applied by NetWalker ransomware affiliates — i.e., cybercrime groups dependable for figuring out and attacking high-price victims working with the ransomware — to deliver payment recommendations and connect with victims.
Guests to the web-site will now be greeted by a seizure banner notifying them that it has been taken in excess of by law enforcement authorities.
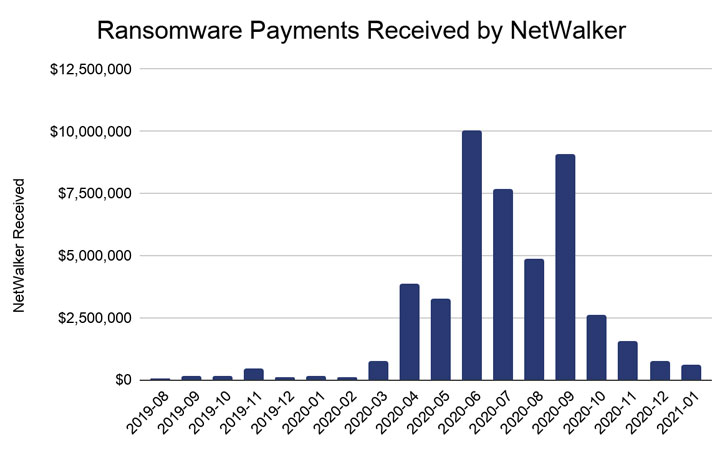
Chainalysis, which aided in the investigation, stated it has “traced extra than $46 million value of funds in NetWalker ransoms because it first arrived on the scene in August 2019,” incorporating “it picked up steam in mid-2020, developing the typical ransom to $65,000 past 12 months, up from $18,800 in 2019.”
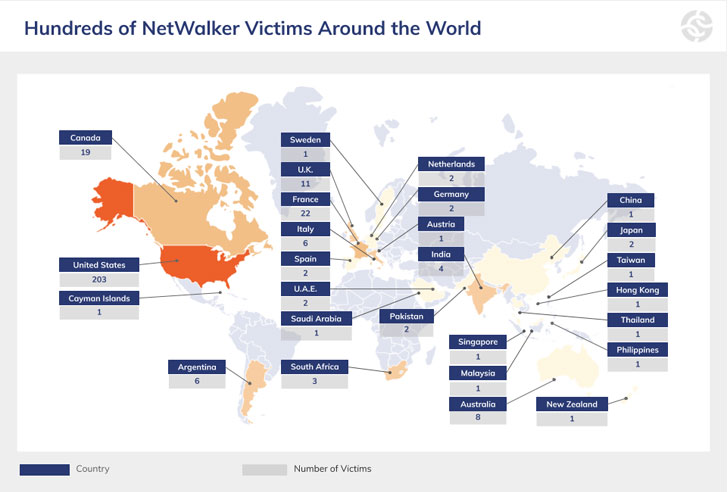
In modern months, Netwalker emerged as a popular decision of ransomware strain besides Ryuk, Maze, Doppelpaymer, and Sodinokibi, with many firms, municipalities, hospitals, educational facilities, and universities qualified by the cybercriminals to extort victims.
Right before the takedown, the NetWalker administrator, who goes by the moniker “Bugatti” on darknet community forums, is claimed to have posted an ad in May 2020 hunting for further Russian-talking affiliates as element of a changeover to a ransomware-as-a-assistance (RaaS) design, employing the associates to compromise targets and steal facts in advance of encrypting the data files.
The NetWalker operators have also been aspect of a escalating ransomware pattern named double extortion, where the attackers maintain the stolen details hostage and threaten to publish the information and facts should the concentrate on refuse to pay back the ransom.
“Immediately after a sufferer pays, builders and affiliate marketers break up the ransom,” the U.S. Division of Justice (DoJ) reported.
Chainalysis researchers suspect that aside from involving in at least 91 attacks working with NetWalker due to the fact April 2020, Vachon-Desjardins worked as an affiliate for other RaaS operators these as Sodinokibi, Suncrypt, and Ragnarlocker.
The NetWalker disruption will come on the exact working day that European authorities introduced a coordinated takedown targeting the Emotet crimeware-as-a-provider network. The botnet has been applied by numerous cybercrime teams to deploy second-stage malware — most notably Ryuk and TrickBot.
Discovered this report attention-grabbing? Observe THN on Facebook, Twitter and LinkedIn to examine far more distinctive written content we write-up.
Some parts of this post are sourced from:
thehackernews.com


 #DataPrivacyDay: Leaks and Breaches Soared 93% in 2020
#DataPrivacyDay: Leaks and Breaches Soared 93% in 2020