Two well-liked Android applications from Chinese tech large Baidu have been taken out from the Google Participate in Retail outlet in Oct just after they were caught gathering delicate person particulars.
The two apps in question—Baidu Maps and Baidu Research Box—were observed to acquire system identifiers, these types of as the Global Cell Subscriber Identification (IMSI) variety or MAC deal with, without having users’ information, consequently building them likely trackable on the web.
The discovery was built by network security company Palo Alto Networks, who notified the two Baidu and Google of their findings, following which the search business pulled the apps on Oct 28, citing “unspecified violations.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
As of composing, a compliant variation of Baidu Lookup Box has been restored to the Perform Retail store on November 19, although Baidu Maps continues to be unavailable until eventually the unresolved issues highlighted by Google are set.
A different application named Homestyler was also located to accumulate private info from users’ Android devices.
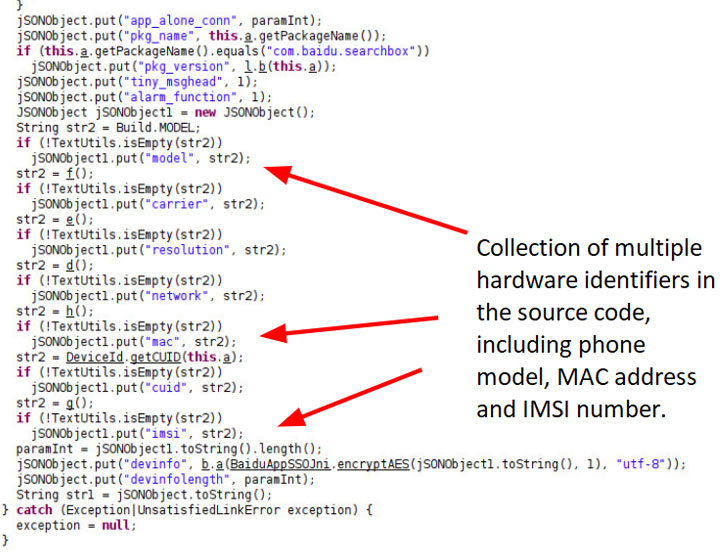
According to Palo Alto scientists, the whole list of knowledge collected by the applications consist of:
- Phone product
- Screen resolution
- Phone MAC deal with
- Carrier (Telecom Service provider)
- Network (Wi-Fi, 2G, 3G, 4G, 5G)
- Android ID
- IMSI quantity
- Intercontinental Cellular Devices Identification (IMEI) number
Making use of a equipment learning-primarily based algorithm made to detect anomalous spy ware visitors, the origin of the information leak was traced to Baidu’s Press SDK as perfectly as ShareSDK from the Chinese seller MobTech, the latter of which supports 37,500 applications, such as more than 40 social media platforms.
When Google has taken techniques to safe the Engage in retail store and end the destructive exercise, negative actors are nevertheless locating approaches to infiltrate the app marketplace and leverage the system for their gain.
Indeed, an tutorial research published by researchers from NortonLifeLock earlier this month observed the Engage in Retail outlet to be the key source of malware installs (about 67.5%) on Android products based on an evaluation of app installations on 12 million handsets above a four-thirty day period period of time involving June and September 2019, fueled in section due to the broad acceptance of the system.
However, its vector detection ratio — the ratio of undesirable applications put in by that vector total apps mounted by that vector — was uncovered to be only .6% when in contrast to option 3rd-party app retailers (3.2%).
“As a result, the Enjoy industry defenses from unwelcome apps do the job, but nonetheless significant quantities of unwanted applications are capable to bypass them, generating it the key distribution vector for unwanted apps,” the scientists said.
If something, the incident is but a different reminder that no app, even if developed by a legitimate third-party, can be taken for granted.
This also signifies the common safeguards such as scrutinizing app reviews, developer particulars, and the list of requested permissions might not supply plenty of security, hence creating it difficult to ascertain if a authorization is misused by cybercriminals to steal private facts.
“In cellular products, it is typical to question a user to grant a listing of permissions on installation of an software or to prompt a person to enable or deny a authorization when the software is jogging,” Palo Alto researchers concluded.
“Disallowing permissions can typically consequence in a non-working software, which leads to a bad person experience and could possibly tempt a user to simply click on ‘allow’ just to be in a position to use an software. Even if a selected authorization is granted, it is often up to the app builders whether it is used in accordance with the official suggestions.”
Observed this article interesting? Adhere to THN on Facebook, Twitter and LinkedIn to study much more distinctive material we publish.
Some elements of this article are sourced from:
thehackernews.com


 Biden’s DHS nominee Mayorkas offers hope of stability, resilience
Biden’s DHS nominee Mayorkas offers hope of stability, resilience