A China-based mostly financially determined group is leveraging the have confidence in affiliated with common intercontinental manufacturers to orchestrate a huge-scale phishing marketing campaign dating back again as much as 2019.
The risk actor, dubbed Fangxiao by Cyjax, is said to have registered over 42,000 imposter domains, with first exercise noticed in 2017.
“It targets firms in many verticals such as retail, banking, vacation, and power,” researchers Emily Dennison and Alana Witten reported. “Promised monetary or bodily incentives are used to trick victims into further more spreading the marketing campaign via WhatsApp.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Users clicking on a url despatched by way of the messaging application are directed to an actor-managed web site, which, in switch, sends them to a landing area impersonating a very well-identified brand name, from wherever the victims are once once again taken to web-sites distributing fraudulent apps and bogus rewards.
These internet sites prompt the people to complete a study to declare income prizes, in exchange for which they are asked to forward the information to five teams or 20 mates. The ultimate redirect, even so, hinges on the IP tackle of the sufferer and the browser’s Consumer-Agent string.
Additional than 400 organizations, like Emirates, Shopee, Unilever, Indomie, Coca-Cola, McDonald’s, and Knorr, are currently being imitated as section of the felony scheme, the researchers claimed.
Alternatively, attacks wherein scammy cell ads are clicked from an Android unit have been noticed to culminate in the deployment of a cell trojan referred to as Triada, which was recently spotted propagating via pretend WhatsApp applications.
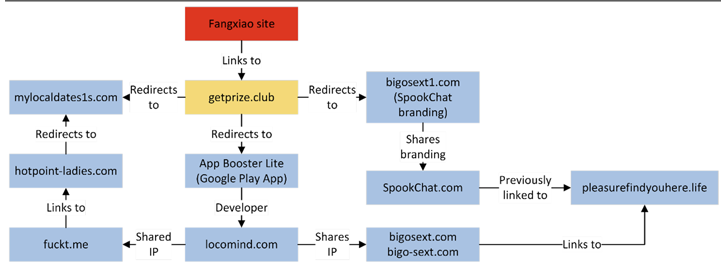
It’s not just Triada, as a further location of the campaign is the Google Perform Retail store listing of an app named “App Booster Lite – RAM Booster” (com.app.booster.lite.phonecleaner.batterysaver.cleanmaster), which has around 10 million downloads.
The app, produced by a Czechia-based developer acknowledged as LocoMind, is explained as a “Effective Phone Booster,” “Sensible Junk Cleaner,” and an “Powerful Battery Saver.”
Reviews for the app have identified as out the publisher for displaying also lots of advertisements, and even level out that they “Arrived below [the Play Store page] from one particular of those ‘your android is weakened x%’ adverts.”
“Our application can not spread viruses,” LocoMind responded to the review on Oct 31, 2022. “Each and every of our updates is checked by Google Enjoy – they would have removed our application very long ago for this rationale.”
Should really the similar action be carried out from a system functioning iOS, the target is redirected to Amazon via an affiliate website link, netting the actor a commission for each purchase on the e-commerce system manufactured in the course of the next 24 several hours.
The risk actor’s China connections stem from the existence of Mandarin text in a web services involved with aaPanel, a Python-primarily based open up resource regulate panel for hosting many web-sites.
Further examination of the TLS certificates issued to the study domains in 2021 and 2022 reveals that a bulk of the registrations overlap with the UTC+08:00 time zone, which corresponds to China Normal Time from 9:00 a.m. to 11:00 p.m.
“The operators are expert in operating these sorts of imposter strategies, eager to be dynamic to reach their goals, and technically and logistically able of scaling to expand their business,” the researchers explained.
“The Fangxiao strategies are effective direct technology strategies which have been redirected to various domains, from malware, to referral hyperlinks, to ads and adware.”
Found this article appealing? Abide by THN on Fb, Twitter and LinkedIn to study far more exclusive information we publish.
Some components of this report are sourced from:
thehackernews.com

 PCI Council Launches Flexible Mobile Payments Standard
PCI Council Launches Flexible Mobile Payments Standard