The U.S. Cybersecurity and Infrastructure Security Company (CISA) is urging federal businesses to secure their units towards an actively exploited security vulnerability in Windows that could be abused to gain elevated permissions on impacted hosts.
To that finish, the company has additional CVE-2022-21882 (CVSS score: 7.) to the Known Exploited Vulnerabilities Catalog, necessitating that Federal Civilian Govt Branch (FCEB) organizations patch all units in opposition to this vulnerability by February 18, 2022.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“These kinds of vulnerabilities are a frequent attack vector for destructive cyber actors of all styles and pose substantial risk to the federal business,” CISA claimed in an advisory revealed final 7 days.
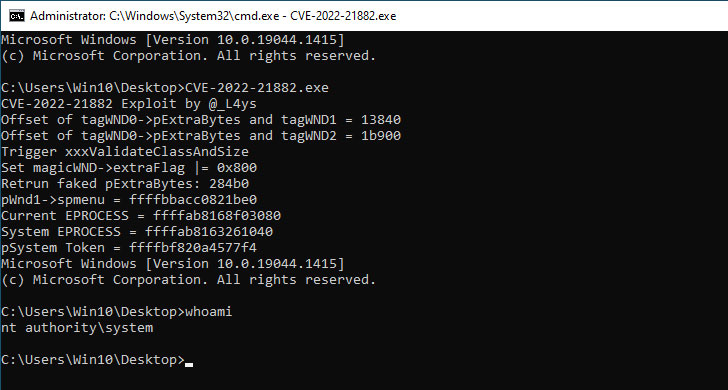
CVE-2022-21882, which has been tagged with an “Exploitation Much more Likely” exploitability index evaluation, issues a circumstance of elevation of privilege vulnerability affecting the Get32k element. The bug was resolved by Microsoft as part of its January 2022 Patch Tuesday updates.
“A area, authenticated attacker could obtain elevated community program or administrator privileges by a vulnerability in the Earn32k.sys driver,” the Windows maker mentioned. The flaw impacts Windows 10, Windows 11, Windows Server 2019, and Windows server 2022.
It really is value noting that the security vulnerability is also a bypass for yet another escalation of privilege flaw in the same module (CVE-2021-1732, CVSS score: 7.8) that Microsoft settled in February 2021 and has given that been detected in exploits in the wild.
Located this post exciting? Adhere to THN on Facebook, Twitter and LinkedIn to study additional exclusive material we publish.
Some elements of this short article are sourced from:
thehackernews.com




 New Argo CD Bug Could Let Hackers Steal Secret Info from Kubernetes Apps
New Argo CD Bug Could Let Hackers Steal Secret Info from Kubernetes Apps