Cybersecurity scientists on Tuesday disclosed a new substantial-scale campaign concentrating on Kubeflow deployments to run destructive cryptocurrency mining containers.
The marketing campaign associated deploying TensorFlow pods on Kubernetes clusters, with the pods operating authentic TensorFlow photos from the formal Docker Hub account. Even so, the container visuals were being configured to execute rogue commands that mine cryptocurrency. Microsoft stated the deployments witnessed an uptick towards the conclusion of May possibly.
Kubeflow is an open up-resource device studying system designed to deploy device understanding workflows on Kubernetes, an orchestration company utilized for taking care of and scaling containerized workloads across a cluster of equipment.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The deployment, in by itself, was reached by having gain of Kubeflow, which exposes its UI features via a dashboard that is deployed in the cluster. In the attack noticed by Microsoft, the adversaries applied the centralized dashboard as an ingress position to make a pipeline to operate TensorFlow visuals that perform cryptocurrency mining duties.

The intrusions also echo related attacks noticed by Microsoft’s Azure Security Center last April that abused Internet-exposed Kubeflow dashboards to deploy a backdoor container for a crypto mining marketing campaign.
“The burst of deployments on the numerous clusters was simultaneous. This indicates that the attackers scanned people clusters in advance and preserved a record of opportunity targets, which had been later attacked on the same time,” Microsoft’s Senior Security Study Engineer Yossi Weizman mentioned in a report.
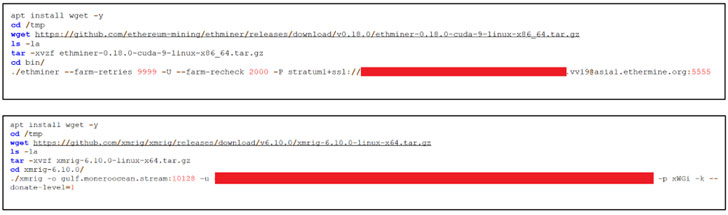
The ongoing attacks are claimed to have utilised two distinct TensorFlow photographs — tagged “most current” and “latest-gpu” — to operate the destructive code. Making use of reputable TensorFlow photographs is also a clever layout to keep away from detection in that TensorFlow containers are prevalent in equipment studying-based workloads.
On top of that, Microsoft mentioned the attackers are capable to consider benefit of the visuals to run GPU duties employing CUDA, therefore enabling the adversary to “maximize the mining gains from the host.”
“As section of the attacking circulation, the attackers also deployed [a] reconnaissance container that queries details about the setting this sort of as GPU and CPU facts, as planning for the mining exercise,” Weizman claimed. “This also ran from a TensorFlow container.”
The enhancement will come times soon after Palo Alto Networks’ Unit 42 danger intelligence staff disclosed a brand name new variety of malware identified as Siloscope designed to compromise Kubernetes clusters through Windows containers.

People running Kubeflow are suggested to make certain that the centralized dashboard just isn’t insecurely uncovered to the Internet, and if considered important, have to have that they be guarded powering authentication boundaries.
Microsoft has also posted a threat matrix for Kubernetes to greater recognize the attack surface of containerized environments and assist businesses in determining latest gaps in their defenses to protected in opposition to threats concentrating on Kubernetes.
Before this April, the company, alongside other users of Middle for Threat-Informed Protection teamed up to release what’s known as the ATT&CK for Containers matrix that builds on the Kubernetes threat matrix to detect “hazards linked with containers, like misconfigurations that are generally the first vector for attacks, as effectively as the unique implementation of attack approaches in the wild.”
Identified this article intriguing? Stick to THN on Fb, Twitter and LinkedIn to browse more exclusive material we write-up.
Some elements of this write-up are sourced from:
thehackernews.com


 A Third of Execs Plan to Spy on Staff to Guard Trade Secrets
A Third of Execs Plan to Spy on Staff to Guard Trade Secrets