A new cyber attack campaign is leveraging the PowerShell script associated with a authentic crimson teaming tool to plunder NTLMv2 hashes from compromised Windows units mostly positioned in Australia, Poland, and Belgium.
The exercise has been codenamed Steal-It by Zscaler ThreatLabz.
“In this campaign, the risk actors steal and exfiltrate NTLMv2 hashes working with custom-made variations of Nishang’s Commence-CaptureServer PowerShell script, executing numerous technique instructions, and exfiltrating the retrieved info by means of Mockbin APIs,” security researchers Niraj Shivtarkar and Avinash Kumar mentioned.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Nishang is a framework and assortment of PowerShell scripts and payloads for offensive security, penetration screening, and purple teaming.
The attacks leverage as lots of as five diverse an infection chains, although they all leverage phishing e-mails containing ZIP archives as the commencing stage to infiltrate distinct targets employing geofencing methods –
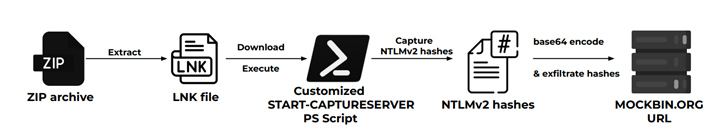
- NTLMv2 hash stealing infection chain, which employs a personalized edition of the aforementioned Start off-CaptureServer PowerShell script to harvest NTLMv2 hashes
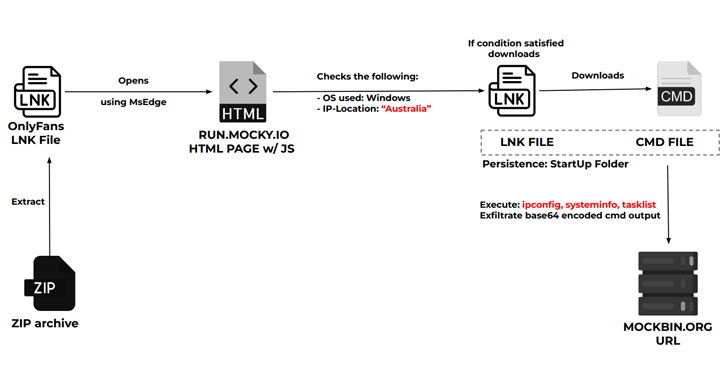
- Procedure data thieving infection chain, which OnlyFans lures to goal Australian users into downloading a CMD file that pilfers process details
- Fansly whoami an infection chain, which works by using express photographs of Ukrainian and Russian Fansly types to entice Polish users into downloading a CMD file that exfiltrates the success of the whoami command
- Windows update an infection chain, which targets Belgium consumers with fake Windows update scripts designed to run commands like tasklist and systeminfo
It is truly worth noting that the last attack sequence was highlighted by the Computer Unexpected emergency Reaction Crew of Ukraine (CERT-UA) in May perhaps 2023 as aspect of an APT28 campaign directed towards authorities establishments in the state.
Approaching WEBINARWay As well Vulnerable: Uncovering the Point out of the Identification Attack Surface area
Reached MFA? PAM? Service account safety? Obtain out how nicely-geared up your organization truly is in opposition to identification threats
Supercharge Your Abilities
This raises the probability that the Steal-It marketing campaign could also be the function of the Russian point out-sponsored danger actor.
“The risk actors’ custom made PowerShell scripts and strategic use of LNK files inside ZIP archives highlights their technical abilities,” the researchers said. “The persistence taken care of by shifting files from the Downloads to Startup folder and renaming them underscores the risk actors’ dedication to extended entry.”
Observed this post fascinating? Observe us on Twitter and LinkedIn to read extra special articles we write-up.
Some components of this posting are sourced from:
thehackernews.com

 New HijackLoader Modular Malware Loader Making Waves in the Cybercrime World
New HijackLoader Modular Malware Loader Making Waves in the Cybercrime World