Governing administration and military companies in the Asia Pacific region are currently being targeted by a earlier not known innovative persistent risk (APT) actor, per the latest investigate.
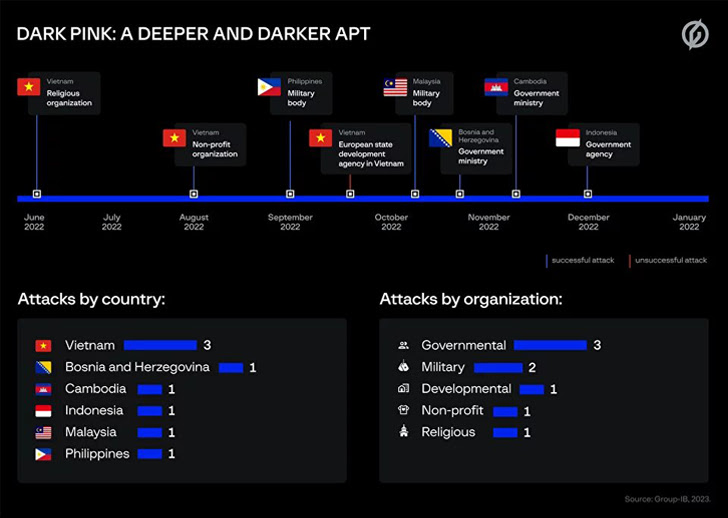
Singapore-headquartered Team-IB, in a report shared with The Hacker News, claimed it can be tracking the ongoing marketing campaign below the title Dark Pink and attributed seven successful attacks to the adversarial collective amongst June and December 2022.
The bulk of the attacks have singled out navy bodies, government ministries and businesses, and spiritual and non-earnings companies in Cambodia, Indonesia, Malaysia, Philippines, Vietnam, and Bosnia and Herzegovina, with 1 unsuccessful intrusion described versus an unnamed European state growth overall body centered in Vietnam.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The danger actor is approximated to have commenced its operations way back in mid-2021, although the attacks ramped up only a 12 months later on applying a never-prior to-noticed custom toolkit designed to plunder worthwhile details from compromised networks.
“Dark Pink APT’s key plans are to carry out corporate espionage, steal files, seize the sound from the microphones of infected equipment, and exfiltrate information from messengers,” Group-IB researcher Andrey Polovinkin mentioned, describing the exercise as a “really advanced APT marketing campaign launched by seasoned threat actors.”
In addition to its advanced malware arsenal, the group has been observed leveraging spear-phishing e-mail to initiate its attacks as very well as Telegram API for command-and-management (C2) communications.
Also noteworthy is the use of a single GitHub account for hosting destructive modules and which has been active considering that May possibly 2021, suggesting that Dark Pink has been equipped to function without the need of having detected for around 1.5 decades.
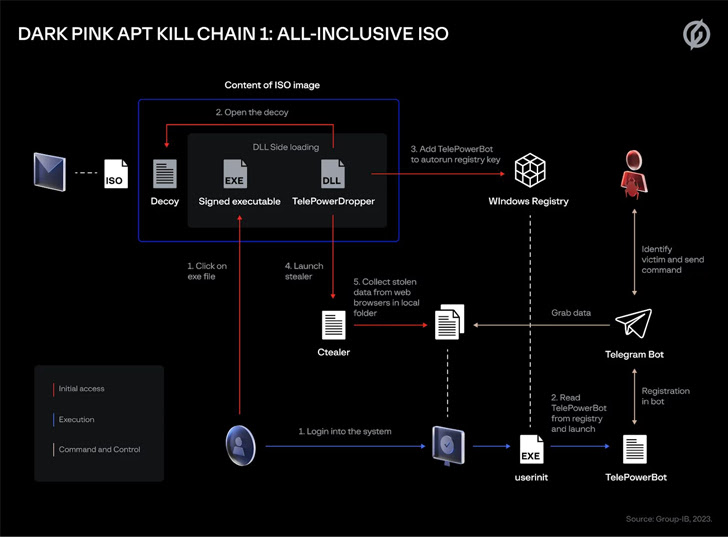
The Dark Pink marketing campaign even further stands out for employing a number of an infection chains, wherein the phishing messages contain a hyperlink to a booby-trapped ISO picture file to activate the malware deployment process. In a person occasion, the adversary posed as a candidate implementing for a PR internship.
It’s also suspected that the hacking crew might be trawling career boards in order to tailor their messages and increase the chance of good results of their social engineering attacks.
The supreme goal is to deploy TelePowerBot and KamiKakaBot, which are capable of executing commands sent by using an actor-managed Telegram bot, in addition to working with bespoke equipment like Ctealer and Cucky to siphon qualifications and cookies from web browsers.
Though Ctealer is prepared in C/C++, Cucky is a .NET plan. An additional personalized malware is ZMsg, a .NET-centered application that enables Dark Pink to harvest messages despatched via messaging apps such as Telegram, Viver, and Zalo.
An alternate kill chain determined by Team-IB utilizes a decoy doc bundled in the ISO file to retrieve a rogue macro-enabled template from GitHub, which, in change, harbors TelePowerBot, a PowerShell script malware.
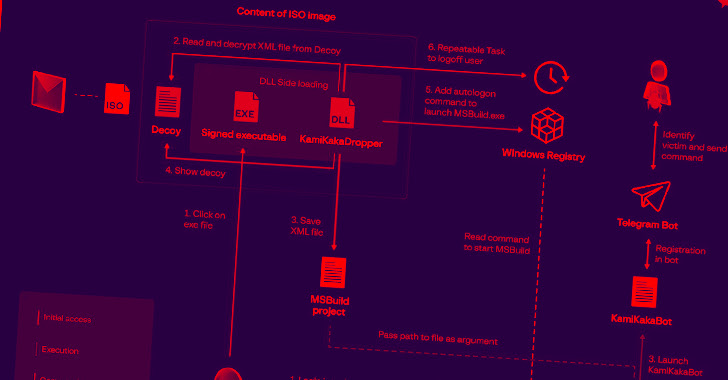
That is not all. A third approach spotted not long ago in December 2022 sees the launch of KamiKakaBot, a .NET version of TelePowerBot, with the help of an XML file that contains an MSBuild project that’s found at the close of a Phrase doc in encrypted view. The Word file is present in an ISO impression sent to the victim in a spear-phishing email.
“The danger actors behind this wave of attacks were in a position to craft their equipment in numerous programming languages, providing them versatility as they attempted to breach defense infrastructure and gain persistence on victims’ networks,” Polovinkin discussed.
A effective compromise is followed by reconnaissance, lateral movement, and info exfiltration pursuits, with the actor also using Dropbox and email in some scenarios to transmit data files of interest. A publicly offered PowerSploit module is also used to record microphone audio on the equipment, alongside executing instructions to infect connected USB disks to propagate the malware.
“The use of an nearly fully customized toolkit, advanced evasion techniques, the menace actors’ means to rework their malware to ensure utmost success, and the profile of the specific organizations reveal the menace that this certain team poses,” Polovinkin claimed.
Uncovered this short article attention-grabbing? Stick to us on Twitter and LinkedIn to read much more exceptional articles we article.
Some pieces of this report are sourced from:
thehackernews.com

 Microsoft Issues January 2023 Patch Tuesday Updates, Warns of Zero-Day Exploit
Microsoft Issues January 2023 Patch Tuesday Updates, Warns of Zero-Day Exploit