The malware known as DirtyMoe has acquired new worm-like propagation capabilities that allow it to broaden its achieve without demanding any user conversation, the hottest study has identified.
“The worming module targets more mature very well-regarded vulnerabilities, e.g., EternalBlue and Scorching Potato Windows privilege escalation,” Avast researcher Martin Chlumecký claimed in a report printed Wednesday.
“A person worm module can produce and attack hundreds of countless numbers of non-public and community IP addresses for each day quite a few victims are at risk due to the fact a lot of equipment however use unpatched methods or weak passwords.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Active given that 2016, the DirtyMoe botnet is employed for carrying out cryptojacking and distributed denial-of-provider (DDoS) attacks, and is deployed by suggests of exterior exploit kits like PurpleFox or injected installers of Telegram Messenger.
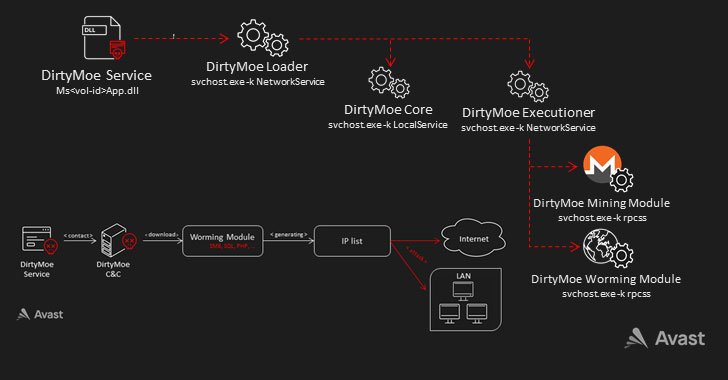
Also used as part of the attack sequence is a DirtyMoe services that triggers the start of two added processes, namely the Core and the Executioner, which is employed to load the modules for Monero mining and to unfold the malware in a worm-like fashion.
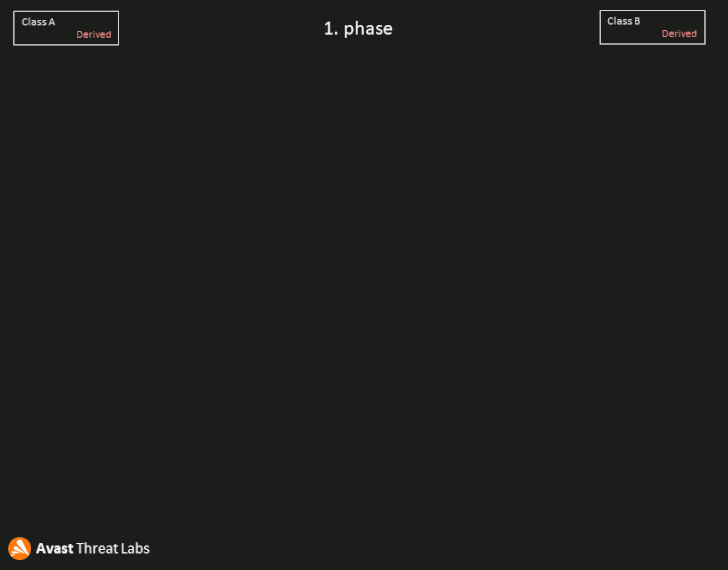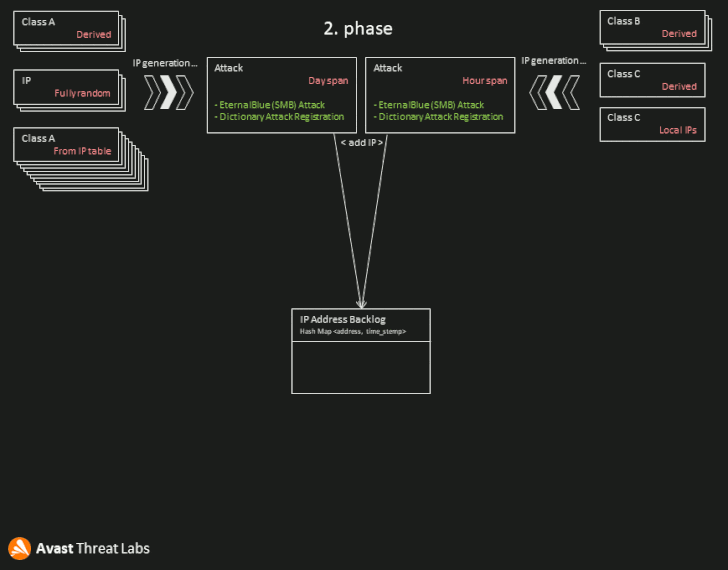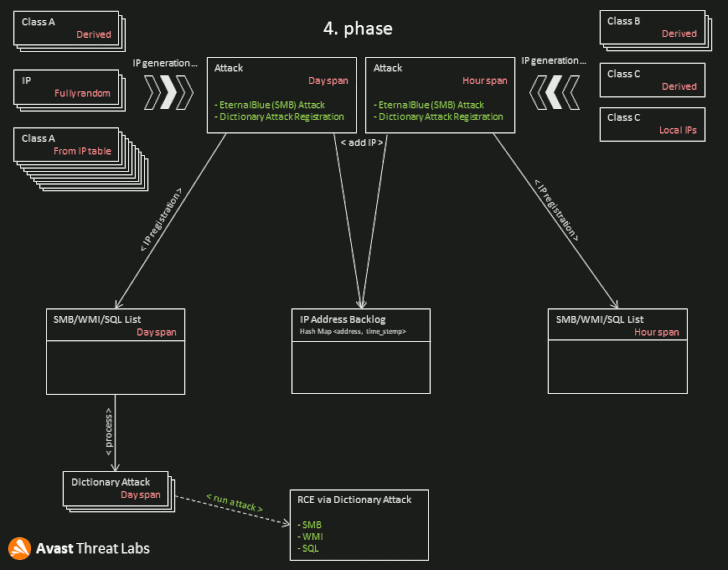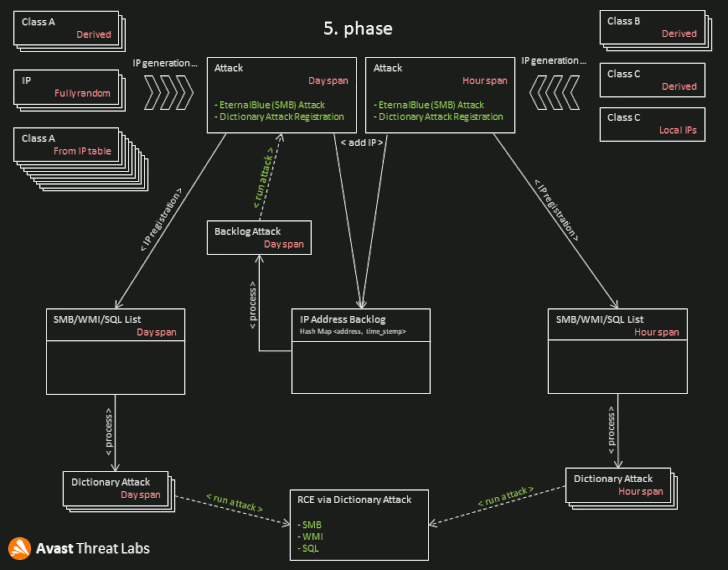
The worming modules attack target machines by applying a number of vulnerabilities to set up the malware, with each individual module concentrating on a certain flaw based mostly on information and facts gathered submit reconnaissance –
- CVE-2019-9082: ThinkPHP – Various PHP Injection RCEs
- CVE-2019-2725: Oracle Weblogic Server – ‘AsyncResponseService’ Deserialization RCE
- CVE-2019-1458: WizardOpium Local Privilege Escalation
- CVE-2018-0147: Deserialization Vulnerability
- CVE-2017-0144: EternalBlue SMB Distant Code Execution (MS17-010)
- MS15-076: RCE Permit Elevation of Privilege (Scorching Potato Windows Privilege Escalation)
- Dictionary attacks aimed at MS SQL Servers, SMB, and Windows Administration Instrumentation (WMI) services with weak passwords
“The key purpose of the worming module is to reach RCE underneath administrator privileges and put in a new DirtyMoe instance,” Chlumecký defined, adding 1 of the component’s core capabilities is to crank out a list of IP addresses to attack primarily based on the geological location of the module.
On top of that, a further in-development worming module was found to incorporate exploits targeting PHP, Java Deserialization, and Oracle Weblogic Servers, implying that the attackers are wanting to broaden the scope of the infections.
“Worming concentrate on IPs are generated making use of the cleverly intended algorithm that evenly generates IP addresses across the globe and in relation to the geological site of the worming module,” Chlumecký reported. “What’s more, the module targets nearby/household networks. Due to the fact of this, public IPs and even private networks driving firewalls are at risk.”
Uncovered this post exciting? Adhere to THN on Fb, Twitter and LinkedIn to go through extra exceptional written content we put up.
Some parts of this report are sourced from:
thehackernews.com


 The Golden Hour of Incident Response
The Golden Hour of Incident Response