An assessment of 4 months of chat logs spanning more than 40 discussions between the operators of Conti and Hive ransomware and their victims has offered an perception into the groups’ interior workings and their negotiation tactics.
In a person exchange, the Conti Crew is said to have drastically reduced the ransom need from a staggering $50 million to $1 million, a 98% drop, suggesting a willingness to settle for a considerably lessen volume.
“Both Conti and Hive are rapid to decrease ransom needs, routinely providing substantial reductions many occasions all over negotiations,” Cisco Talos reported in a report shared with The Hacker Information. “This indicators that despite well-liked perception, victims of a ransomware attack truly have important negotiating electrical power.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Conti and Hive are among the most prevalent ransomware strains in the danger landscape, cumulatively accounting for 29.1% of attacks detected during the 3-month-interval amongst October and December 2021.
A crucial takeaway from the overview of the chat logs is the contrast in interaction models amongst the two teams. When Conti’s conversations with victims are specialist and marked by the use of diverse persuasion practices to persuade victims to pay back the ransom, Hive employs a “a great deal shorter, a lot more immediate” casual technique.
Apart from giving holidays and exclusive reductions, Conti is also acknowledged to supply “IT assist” to avoid potential attacks, sending its victims a so-identified as security report that lists a sequence of actions the impacted entities can take to safe their networks.
Furthermore, the fiscally inspired group has made use of scare methods, cautioning victims of the reputational harm and legal issues stemming as a consequence of a info leak and threatening to share the stolen info with opponents and other stakeholders.
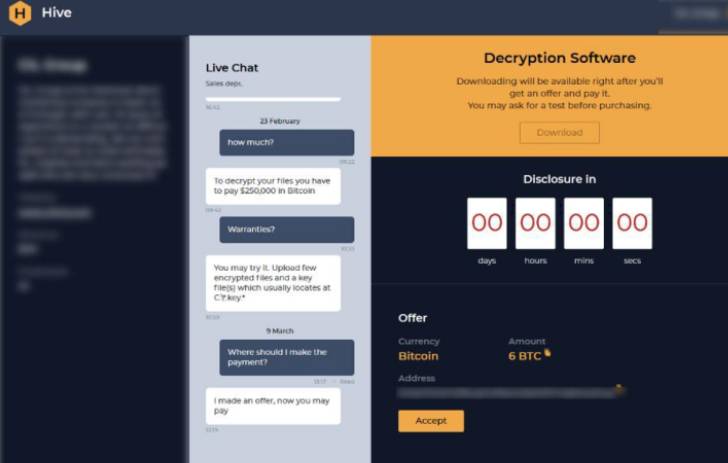
“After encrypting target networks, ransomware danger actors increasingly made use of ‘triple extortion’ by threatening to (1) publicly release stolen sensitive facts, (2) disrupt the victim’s internet obtain, and/or (3) notify the victim’s associates, shareholders, or suppliers about the incident,” CISA pointed out in an advisory earlier this 12 months.
One more stage of difference is Conti’s overall flexibility when it arrives to payment deadlines. “These behaviors suggest Conti operators are remarkably opportunistic cybercriminals who eventually would like some payment as opposed to none,” Talos researcher Kendall McKay claimed.

Hive, on the other hand, has been observed to immediately elevate its ransom calls for should really a target fall short to make the payment by the stipulated date.
What is also noteworthy is Hive’s emphasis on pace above accuracy through the encryption process, producing it vulnerable to cryptographic blunders that allow for recovering the grasp crucial.
“Like a lot of cybercriminals, Conti and Hive are opportunistic actors who likely request to compromise victims by means of the easiest and speediest suggests achievable, which often consist of exploiting known vulnerabilities,” McKay reported. “This is a reminder to all organizations to carry out a sturdy patch management program and hold all devices up-to-day.”
Found this posting fascinating? Adhere to THN on Fb, Twitter and LinkedIn to read through a lot more exclusive material we publish.
Some pieces of this posting are sourced from:
thehackernews.com


 Microsoft makes Defender for Business generally available
Microsoft makes Defender for Business generally available