Cybersecurity researchers have taken the wraps off a earlier undocumented spyware focusing on the Apple macOS working technique.
The malware, codenamed CloudMensis by Slovak cybersecurity organization ESET, is stated to solely use community cloud storage providers such as pCloud, Yandex Disk, and Dropbox for acquiring attacker instructions and exfiltrating documents.
“Its capabilities clearly exhibit that the intent of its operators is to collect info from the victims’ Macs by exfiltrating documents, keystrokes, and monitor captures,” ESET researcher Marc-Etienne M.Léveillé stated in a report published currently.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

CloudMensis, composed in Aim-C, was to start with identified in April 2022 and is created to strike each Intel and Apple silicon architectures. The first infection vector for the attacks and the targets continue being unidentified as still. But its quite constrained distribution is an sign that the malware is getting used as section of a really specific procedure directed from entities of interest.
The attack chain noticed by ESET abuses code execution and administrative privileges to launch a 1st-phase payload which is utilized to fetch and execute a 2nd-stage malware hosted on pCloud, which, in turn, exfiltrates paperwork, screenshots, and email attachments, between some others.
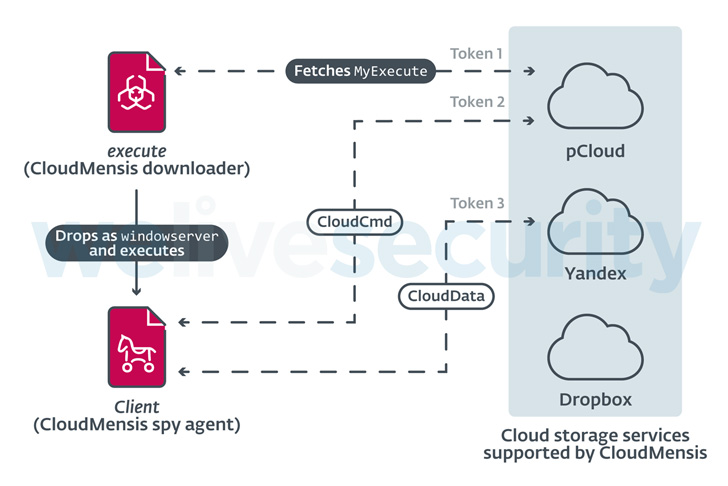
The very first-stage downloader is also recognized to erase traces of Safari sandbox escape and privilege escalation exploits that make use of 4 now-solved security flaws in 2017, suggesting that CloudMensis may well have flown less than the radar for a lot of a long time.
The implant also comes with features to bypass the Transparency, Consent, and Management (TCC) security framework, which aims to make sure that all apps obtain consumer consent just before accessing data files in Paperwork, Downloads, Desktop, iCloud Drive, and network volumes.

It achieves this by exploiting another patched security vulnerability tracked as CVE-2020-9934 that arrived to gentle in 2020. Other functions supported by the backdoor include things like having the list of functioning processes, capturing screenshots, listing data files from detachable storage products, and running shell instructions and other arbitrary payloads.
On leading of that, an analysis of metadata from the cloud storage infrastructure exhibits that the pCloud accounts ended up designed on January 19, 2022, with the compromises commencing on February 4 and peaking in March.
“The common high quality of the code and lack of obfuscation exhibits the authors might not be quite common with Mac enhancement and are not so advanced,” M.Léveillé stated. “Nonetheless a good deal of means were place into creating CloudMensis a impressive spying tool and a menace to prospective targets.”
Located this post intriguing? Adhere to THN on Fb, Twitter and LinkedIn to browse additional distinctive material we article.
Some areas of this report are sourced from:
thehackernews.com


 Security Experts Warn of Two Primary Client-Side Risks Associated with Data Exfiltration and Loss
Security Experts Warn of Two Primary Client-Side Risks Associated with Data Exfiltration and Loss