Cloud-based repository hosting services GitHub has dealt with a substantial-severity security flaw that could have been exploited to generate malicious repositories and mount source chain attacks.
The RepoJacking method, disclosed by Checkmarx, involves a bypass of a security mechanism identified as popular repository namespace retirement, which aims to avoid developers from pulling unsafe repositories with the exact identify.
The issue was tackled by the Microsoft-owned subsidiary on September 19, 2022 following accountable disclosure.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
RepoJacking takes place when a creator of a repository opts to adjust the username, most likely enabling a risk actor to claim the aged username and publish a rogue repository with the exact same title in an attempt to trick end users into downloading them.
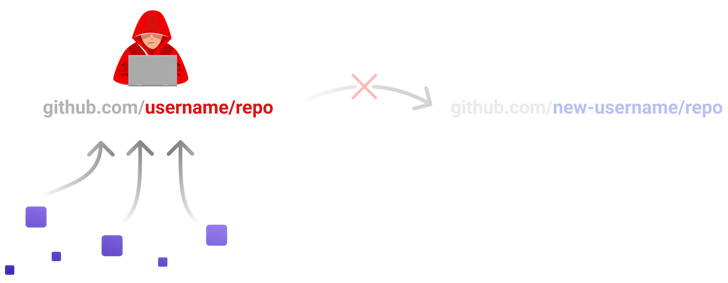
When Microsoft’s countermeasure “retire[s] the namespace of any open resource challenge that experienced far more than 100 clones in the 7 days foremost up to the owner’s account staying renamed or deleted,” Checkmarx found that this can be circumvented through the “repository transfer” aspect.
The way this performs is as follows –
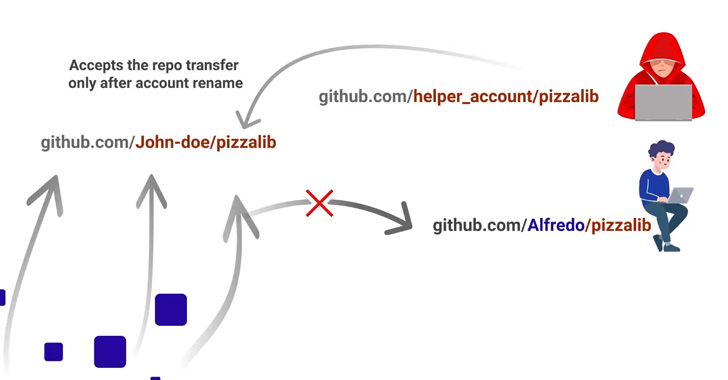
- A menace actor creates a repository with the exact title as the retired repository (say, “repo”) owned by a person named “victim” but beneath a diverse username (say, “helper”)
- “helper” transfers possession of “repo” to a next account with username “attacker”
- “attacker” renames the account’s username to “target”
- The namespace “target/repo” is now under the adversary’s control

In other words, the attack hinges on the quirk that GitHub only considers as retired the namespace, i.e., the mixture of username and repository title, permitting a bad actor to reuse the repository name in conjunction with an arbitrary username.
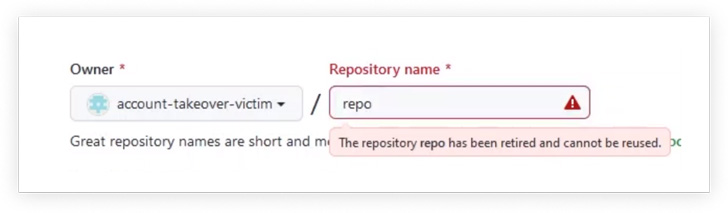
A successful exploitation could have effectively allowed attackers to force poisoned repositories, placing renamed usernames at risk of remaining a victim of source chain attacks.
“If not explicitly tended, all renamed usernames on GitHub had been susceptible to this flaw, like above 10,000 deals on the Go, Swift, and Packagist package deal professionals,” Checkmarx researcher Aviad Gershon explained.
Discovered this write-up attention-grabbing? Follow THN on Facebook, Twitter and LinkedIn to browse extra distinctive content we put up.
Some sections of this posting are sourced from:
thehackernews.com

 Real-time deepfakes are becoming a serious threat
Real-time deepfakes are becoming a serious threat