Malicious actors are resorting to voice phishing (vishing) ways to dupe victims into installing Android malware on their devices, new research from ThreatFabric reveals.
The Dutch cellular security company reported it determined a network of phishing sites concentrating on Italian on-line-banking customers that are designed to get maintain of their get hold of specifics.
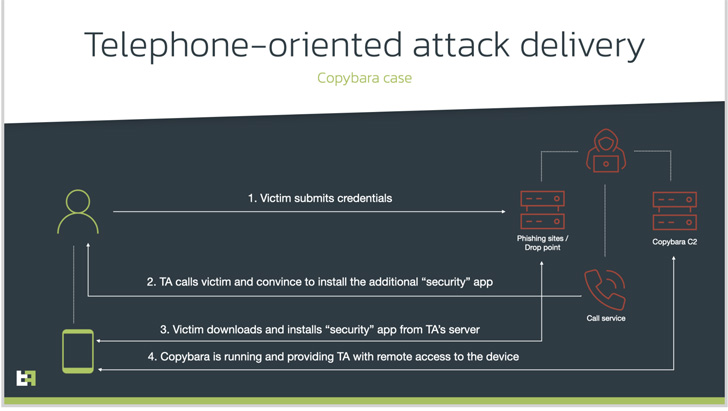
Telephone-oriented attack shipping and delivery (TOAD), as the social engineering strategy is called, will involve contacting the victims employing previously gathered information and facts from fraudulent internet websites.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The caller, who purports to be a help agent for the lender, instructs the personal, on the other hand, to install a security app and grant it substantial permissions, when, in truth, it’s destructive computer software meant to acquire distant accessibility or carry out financial fraud.

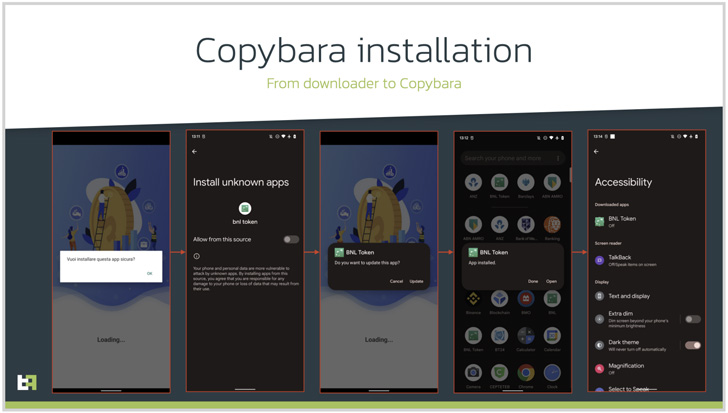
In this circumstance, it potential customers to the deployment of an Android malware dubbed Copybara, a cell trojan 1st detected in November 2021 and is largely utilised to conduct on-machine fraud by way of overlay attacks concentrating on Italian users. Copybara has also been baffled with a further malware spouse and children known as BRATA.
ThreatFabric assessed the TOAD-primarily based strategies to have commenced all around the exact time, indicating that the exercise has been ongoing for just about a year.
Like any other Android-based mostly malware, Copybara’s RAT capabilities are driven by abusing the working system’s accessibility providers API to get sensitive info and even uninstall the downloader application to lessen its forensic footprint.
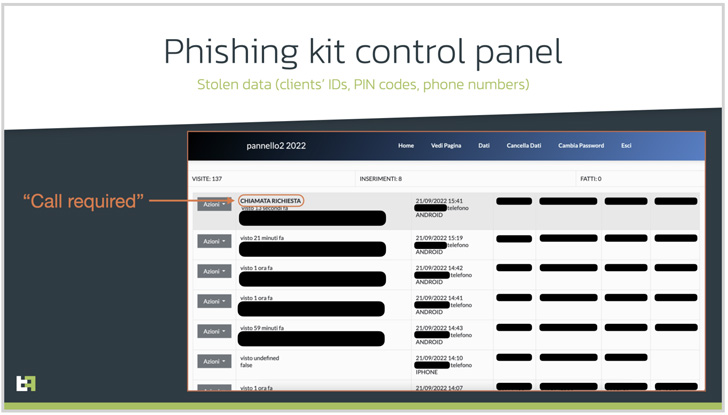
What is actually a lot more, the infrastructure used by the danger actor has been uncovered to supply a 2nd malware named SMS Spy that allows the adversary to attain entry to all incoming SMS messages and intercept 1-time passwords (OTPs) sent by banking institutions.

The new wave of hybrid fraud attacks provides a new dimension for scammers to mount convincing Android malware campaigns that have or else relied on conventional procedures these kinds of as Google Perform Retailer droppers, rogue advertisements, and smishing.
“Such attacks require additional methods on [threat actors’] facet and are more innovative to conduct and maintain,” ThreatFabric’s Cell Menace Intelligence (MTI) team explained to The Hacker Information.
“We also like to position out that specific attacks from a fraud achievements point of view are sadly much more thriving, at least in this unique campaign.”
This is not the 1st time TOAD tactics are being used to orchestrate banking malware strategies. Very last thirty day period, the MalwareHunterTeam in-depth a related attack aimed at users of the Indian lender Axis Financial institution in a bid to put in an data-stealer that impersonates a credit score card rewards app.
“Any suspicious contact must be double checked by contacting your money organization,” the MTI group stated, including “monetary companies should offer their customers with understanding about ongoing strategies and boost the client apps with mechanisms to detect suspicious exercise.”
Observed this short article interesting? Stick to THN on Fb, Twitter and LinkedIn to study more exceptional information we article.
Some components of this post are sourced from:
thehackernews.com


 Zoom-themed cyber attacks fuel rapid malware growth
Zoom-themed cyber attacks fuel rapid malware growth