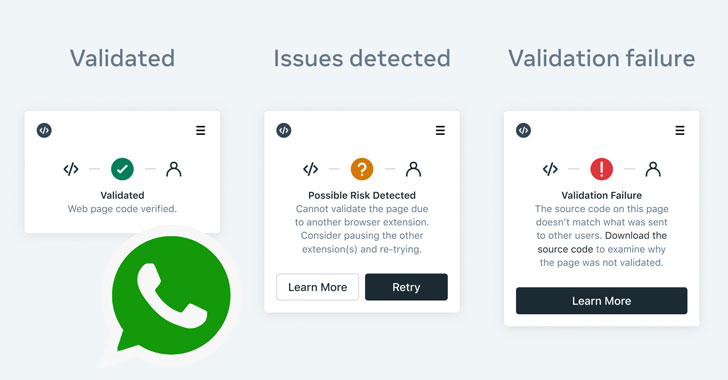
Meta Platforms’ WhatsApp and Cloudflare have banded jointly for a new initiative referred to as Code Validate to validate the authenticity of the messaging service’s web app on desktop pcs.
Offered in the variety of a Chrome and Edge browser extension, the open up-resource add-on is created to “immediately verif[y] the authenticity of the WhatsApp Web code currently being served to your browser,” Fb mentioned in a statement.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The aim with Code Validate is to validate the integrity of the web application and be certain that it has not been tampered with to inject malicious code. The social media corporation is also preparing to launch a Firefox plugin to obtain the very same amount of security across browsers.
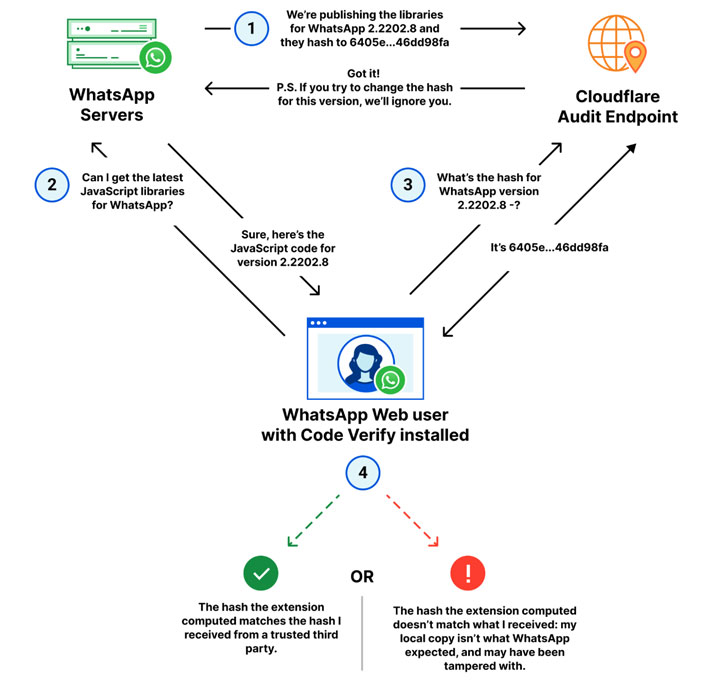
The process operates with Cloudflare performing as a third-party audit to review the cryptographic hash of WhatsApp Web’s JavaScript code that is shared by Meta with that of a regionally computed hash of the code operating on the browser shopper.
Code Confirm is also intended to be versatile in that anytime the code for WhatsApp Web is current, the cryptographic hash worth will be up-to-date immediately in tandem, so that the code served to buyers is licensed on the fly.
WhatsApp, in a different FAQ on the hottest security function, emphasized that “the extension will never read through or accessibility the messages you mail or receive, and we is not going to know if you have downloaded the extension.” The increase-on will also not log any knowledge, metadata, or person knowledge, and isn’t going to share any facts with WhatsApp, it observed.
“The strategy by itself — evaluating hashes to detect tampering or even corrupted information — is just not new, but automating it, deploying it at scale, and building sure it ‘just works’ for WhatsApp buyers is,” Cloudflare claimed.
Identified this write-up interesting? Stick to THN on Facebook, Twitter and LinkedIn to study much more exclusive articles we post.
Some areas of this write-up are sourced from:
thehackernews.com



 Malware Posing as Russia DDoS Tool Bites Pro-Ukraine Hackers
Malware Posing as Russia DDoS Tool Bites Pro-Ukraine Hackers