The National Institute of Benchmarks and Technology (NIST) is a person of the regular-bearers in world cybersecurity. The U.S.-primarily based institute’s cybersecurity framework can help corporations of all measurements fully grasp, manage, and minimize their cyber-risk levels and greater protect their details. Its worth in the struggle versus cyberattacks won’t be able to be overstated.
When NIST has not straight formulated criteria connected to securing the SaaS ecosystem, they are instrumental in the way we technique SaaS security.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
NIST a short while ago launched its Tutorial to a Secure Enterprise Network Landscape. In it, they examine the transformation from on-premise networks to several cloud servers. Accessibility to these servers, and the accompanying SaaS apps, is through both equally protected and unsecured devices and locations across disparate geography.
The go to the cloud has proficiently obliterated the network perimeter. As a result, companies have amplified their attack surface area and are encountering an escalation of attacks that span throughout network boundaries.
Alternatively than emphasis on network-centric security, security must get a 3-pronged solution. The consumer, endpoint, and software are keys to safeguarding information. This new paradigm emphasizes the value of identification, locale, and contextual details related with the user, unit, and assistance.
Discover how Adaptive Protect can help implement NIST compliance.
The Tools to Meet Present day Troubles
Present day security resources require to scale to meet the quantity, velocity, and wide variety of today’s purposes. They have to have to integrate seamlessly with SaaS applications and give coverage for the full SaaS stack.
To be successful, these equipment require to lower human intervention for checking and remediation. Automation is critical for an ecosystem that requires secure configurations for just about every user account that has entry to the application. Substantial organizations may possibly have thousands and thousands of configurations to secure throughout their overall SaaS stack closing them manually is an difficult process.
SaaS Checking
SaaS security instruments have to be capable to combine with all the applications on the stack and determine each application as a result of the SaaS app’s APIs. Once connected, it need to keep track of the security configurations, being notify to any changes. This configuration drift can have extreme implications, as it exposes SaaS apps by eliminating the safeguards put in put to prevent unauthorized accessibility. It demands to continuously monitor programs, and issue alerts as risk boosts.
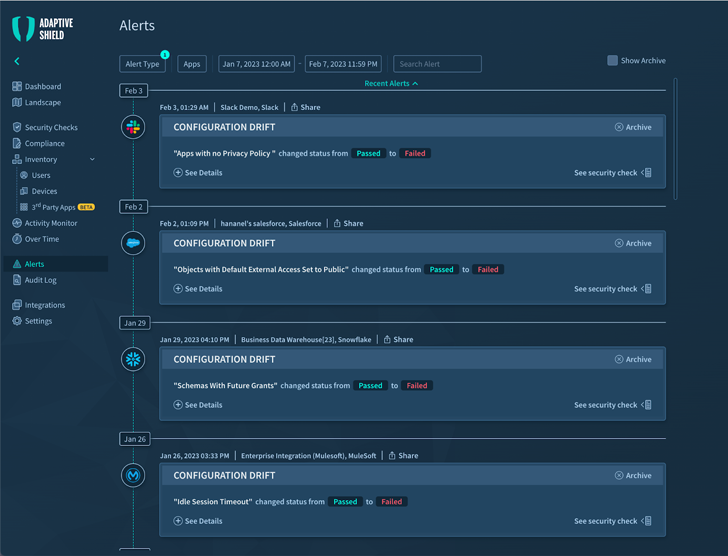 Figure 1. SaaS Monitoring in Adaptive Defend System
Figure 1. SaaS Monitoring in Adaptive Defend System
Contextual Knowledge
Powerful SaaS security instruments use contextual data to detect threats to the application and its facts. These threats can appear from human beings and machines and may have accessibility to the procedure applying verified qualifications.
Contextual knowledge from throughout the SaaS stack can assist identify paradoxical vacation, spikes in unsuccessful authentication tries from the exact IP address for multiple accounts, or tries the place automated instruments take a look at weak and prevalent passwords versus recognised person names. It can also understand destructive 3rd-party apps that are drastically overprivileged for their features.
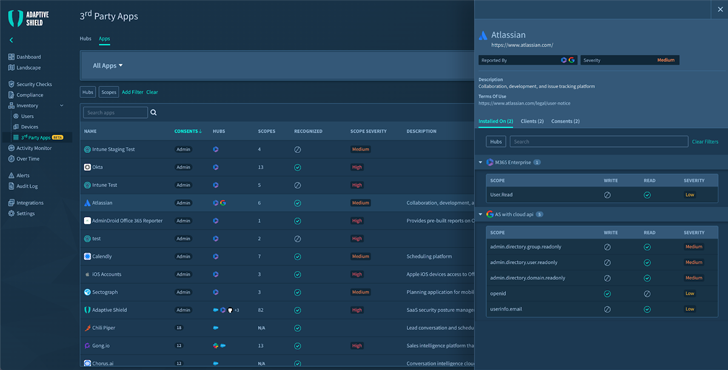 Determine 2. Contextual Information as Viewed in Adaptive Defend
Determine 2. Contextual Information as Viewed in Adaptive Defend
Get a demo of how Adaptive Defend can assist secure your SaaS stack
Machine Management
In the environment of SaaS, the gadgets signify the network perimeter. Accessing SaaS programs with devices that have lousy cleanliness can put all the information at risk. Compromised devices can hand over login credentials to menace actors, who can leverage that into breaching and thieving information.
Effective SaaS security equipment husband or wife with endpoint security providers to be certain that the devices that obtain SaaS apps have an up-to-day operating procedure, all software package has been current, and any patches have been applied.
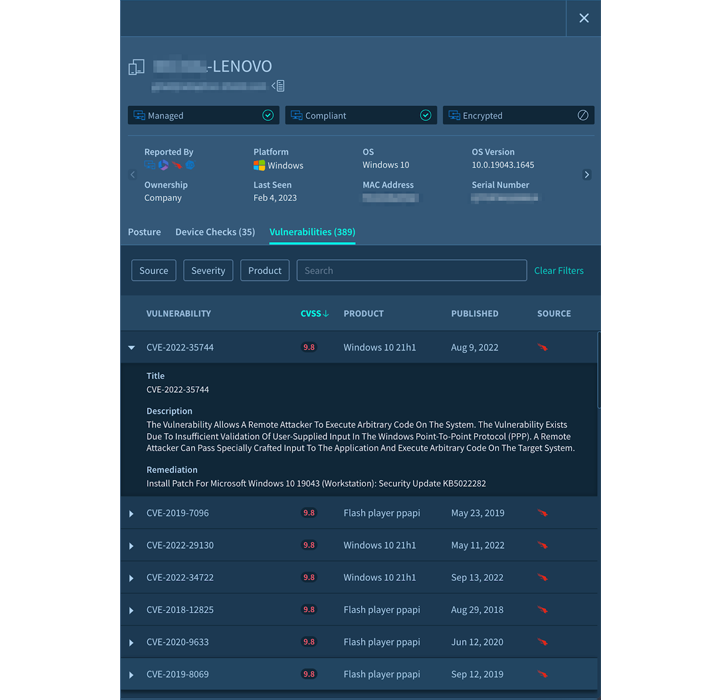 Determine 3. Device Management in Adaptive Shield System
Determine 3. Device Management in Adaptive Shield System
Consumer Authentication
Though units may possibly be the perimeter, user ID is the barrier preventing unfettered obtain to enterprise data. Accessibility ought to be provided working with a zero-trust tactic. All obtain really should be granted as a result of an SSO connected to an company-managed IdP. Companies should really reinforce this entryway with a phishing-resistant MFA authenticator.
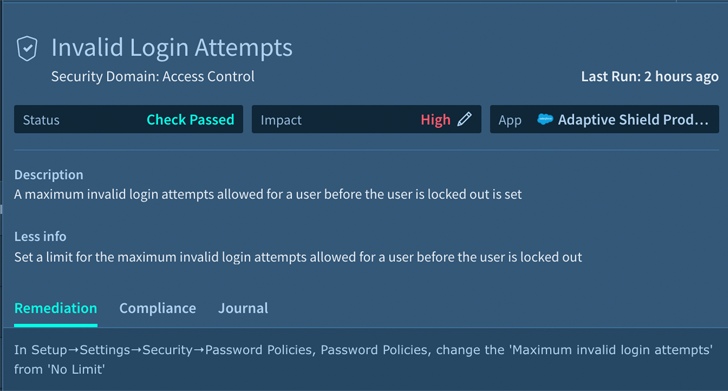 Determine 4. Invalid Login Tries Inform
Determine 4. Invalid Login Tries Inform
Conference NIST Expectations
Successful SSPM platforms are built on robust security checks that overview each individual SaaS configuration to ensure they are optimized for defense. Generally, security placing suggestions are motivated intensely by NIST’s cybersecurity approach, and their steering enables SSPM sellers to observe and track use, end users, and behaviors, as well as determine threats.
See how Adaptive Shield’s SSPM could shield your SaaS stack
Located this post interesting? Adhere to us on Twitter and LinkedIn to read more unique written content we publish.
Some sections of this posting are sourced from:
thehackernews.com


 MI5 to establish new security agency to counter Chinese hacking, espionage
MI5 to establish new security agency to counter Chinese hacking, espionage