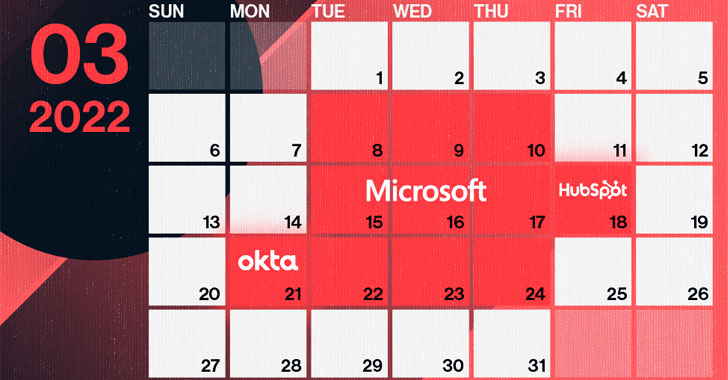
Throughout the final 7 days of March, three big tech corporations – Microsoft, Okta, and HubSpot – documented considerable details breaches. DEV-0537, also regarded as LAPSUS$, executed the to start with two. This remarkably refined team makes use of state-of-the-art attack vectors to excellent accomplishment. In the meantime, the group powering the HubSpot breach was not disclosed. This website will evaluate the 3 breaches based mostly on publicly disclosed info and advise greatest techniques to lessen the risk of these attacks succeeding versus your group.
HubSpot – Worker Obtain
On March 21, 2022, HubSpot described the breach which took place on March 18. Malicious actors compromised a HubSpot personnel account that the employee made use of for client aid. This permitted destructive actors the ability to entry and export make contact with information making use of the employee’s access to quite a few HubSpot accounts.
With little data relating to this breach, defending versus an attack is hard, but a key configuration within just HubSpot can assist. This is the “HubSpot Worker Obtain” control (revealed in the figure under) in HubSpot’s account setting. Shoppers should really disable this location at all situations, unless of course they call for certain aid, and then promptly change it off after finishing the services connect with.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
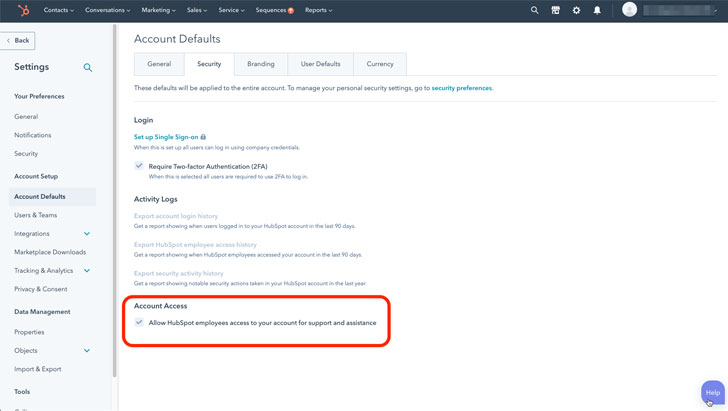
A identical setting seems in other SaaS apps and must be disabled there as perfectly. Staff entry is generally recorded in Audit Logs, which must be reviewed consistently.
Study how an SSPM can assistance safeguard your organization from SaaS misconfigurations
Okta – Absence of Machine Security for Privileged Person
Okta subcontracts some of its buyer help to the Sitel Group. On January 21, an Okta security crew member been given an alert that a new MFA factor was extra to a Sitel Team personnel account from a new site.
An investigation uncovered that a Sitel help engineer’s laptop or computer was compromised applying a remote desktop protocol. This acknowledged vulnerability is typically disabled apart from when specially needed — which helped Okta investigators slender the timeframe for the attack to a five-day window in between Jan. 16-21, 2022.
Thanks to the minimal obtain assistance engineers have to their program, the influence on Okta prospects was minimal. Assist engineers never have obtain to generate or delete users or down load client databases. Their entry to consumer details is quite constrained as effectively.
On March 22, DEV-0537, which is additional normally regarded as LAPSUS$, shared screenshots on line. In reaction, Okta released a assertion stating, “there are no corrective steps our shoppers require to just take.” The subsequent day the enterprise shared facts of its investigation, which bundled a detailed reaction timeline.
Although this breach was constrained in the problems it triggered, it offers three significant security lessons.
See Cloudflare’s investigation of the January 2022 Okta compromise for a superior case in point of a response to such a breach.
Find out how Adaptive Defend delivers endpoint posture administration and SaaS configuration manage
Microsoft – MFA for all privileged people
On March 22, Microsoft Security shared information and facts relating to an attack it endured at the arms of DEV-0537. Microsoft experienced a single account compromised, which resulted in source code getting stolen and posted.
Microsoft confident its users that the LAPSUS$ attack did not compromise any of their information and facts, and even more said that there was no risk to any of their goods due to the stolen code.
Microsoft did not precisely share how the breach was carried out, although it did inform readers that LAPSUS$ actively recruits staff members at telecoms, key computer software builders, contact facilities, and other industries to share credentials.
The enterprise also offered these strategies for securing platforms in opposition to these attacks.
For a whole listing of Microsoft’s suggestions, see this notice.
Remaining views
Securing SaaS platforms is a major challenge, and as observed this week, even world enterprises require to keep on top rated of their security. Malicious actors continue to evolve and increase their attack techniques, which forces companies to be on the lookout and prioritize their SaaS security consistently.
Potent passwords and SSO alternatives are no for a longer time plenty of by on their own. Organizations require highly developed security measures, these types of as sturdy MFA, IP allow for lists, and blocking unneeded support engineer accessibility. An automated answer like SaaS Security Posture Administration (SSPM) can aid security groups remain on leading of these issues.
The great importance of machine security in SaaS is a further takeaway from these attacks. Even a absolutely secured SaaS system can be compromised when a privileged user accesses a SaaS app from a compromised gadget. Leverage a security resolution that brings together system security posture with SaaS security posture for whole, conclude-to-conclusion safety.
The challenge of securing SaaS remedies is complex and over and above burdensome to total manually. SSPM solutions, like Adaptive Protect, can deliver automatic SaaS security posture management, with configuration regulate, endpoint posture administration, and 3rd party software manage.
Notice — This write-up is published and contributed by Hananel Livneh, Senior Item Analyst at Adaptive Defend.
Discovered this post fascinating? Observe THN on Facebook, Twitter and LinkedIn to examine extra exceptional content material we article.
Some parts of this posting are sourced from:
thehackernews.com

 #SecureLondon: Defining Cyber Roles Critical to Tackling Skills Shortage
#SecureLondon: Defining Cyber Roles Critical to Tackling Skills Shortage