An Iranian state-sponsored actor has been observed scanning and trying to abuse the Log4Shell flaw in publicly-uncovered Java programs to deploy a hitherto undocumented PowerShell-primarily based modular backdoor dubbed “CharmPower” for abide by-on article-exploitation.
“The actor’s attack setup was obviously rushed, as they employed the essential open up-supply resource for the exploitation and dependent their operations on former infrastructure, which produced the attack less difficult to detect and attribute,” scientists from Look at Stage claimed in a report released this 7 days.
The Israeli cybersecurity organization connected the attack to a team identified as APT35, which is also tracked utilizing the codenames Charming Kitten, Phosphorus, and TA453, citing overlaps with toolsets formerly discovered as infrastructure applied by the menace actor.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Log4Shell aka CVE-2021-44228 (CVSS rating: 10.) problems a critical security vulnerability in the preferred Log4j logging library that, if productively exploited, could direct to remote execution of arbitrary code on compromised techniques.
The ease of the exploitation coupled with the prevalent use of Log4j library has designed a broad pool of targets, even as the shortcoming has attracted swarms of poor actors, who have seized on the option to phase a dizzying array of attacks since its community disclosure very last month.
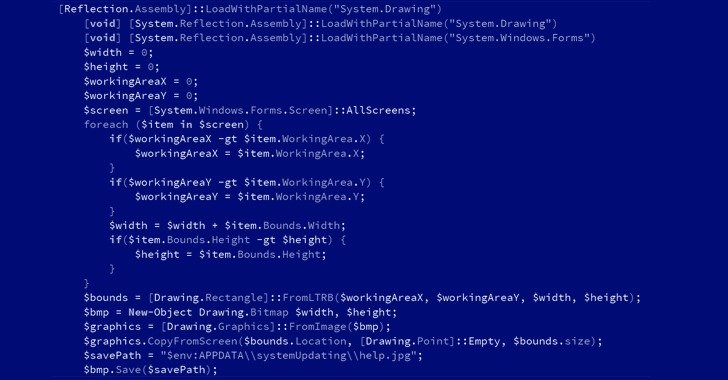
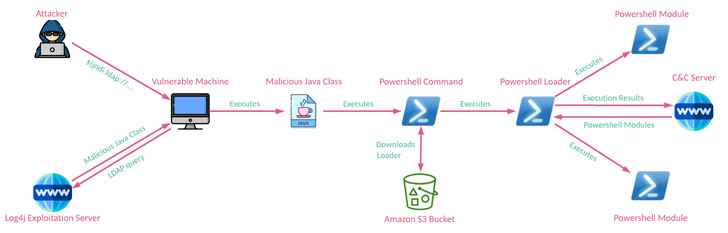
Though Microsoft beforehand pointed out APT35’s endeavours to receive and modify the Log4j exploit, the most recent conclusions clearly show that the hacking team has operationalized the flaw to distribute the PowerShell implant able of retrieving following-phase modules and exfiltrating facts to a command-and-manage (C2) server.
CharmPower’s modules also help a selection of intelligence collecting performance, together with characteristics to obtain method facts, listing mounted applications, acquire screenshots, enumerate jogging procedures, execute commands sent from the C2 server, and clean up up any signs of evidence produced by these factors.
The disclosure will come as Microsoft and the NHS cautioned that internet-facing units functioning VMware Horizon are becoming targeted to deploy web shells and a pressure of ransomware identified as NightSky, with the tech big connecting the latter to a China-based operator dubbed DEV-0401, which has also deployed LockFile, AtomSilo, and Rook ransomware in the past.
What is actually additional, Hafnium, a different risk actor group operating out of China, has also been noticed using the vulnerability to attack virtualization infrastructure to extend their usual focusing on, Microsoft pointed out.
“Judging by their capability to get benefit of the Log4j vulnerability and by the code parts of the CharmPower backdoor, the actors are ready to transform gears rapidly and actively build various implementations for just about every phase of their attacks,” the researchers claimed.
Identified this report exciting? Adhere to THN on Fb, Twitter and LinkedIn to examine a lot more special articles we publish.
Some areas of this write-up are sourced from:
thehackernews.com


 Meeting Patching-Related Compliance Requirements with TuxCare
Meeting Patching-Related Compliance Requirements with TuxCare