Hackers tied to the Iranian govt have been concentrating on individuals specializing in Center Eastern affairs, nuclear security and genome study as part of a new social engineering marketing campaign developed to hunt for sensitive data.
Enterprise security agency attributed the specific attacks to a risk actor named TA453, which broadly overlaps with cyber routines monitored below the monikers APT42, Charming Kitten, and Phosphorus.
It all starts with a phishing email impersonating reputable persons at Western international policy study companies that’s finally intended to gather intelligence on behalf of Iran’s Islamic Groundbreaking Guard Corps (IRGC).

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Spoofed personas contain folks from Pew Investigation Middle, the International Plan Study Institute (FRPI), the U.K.’s Chatham House, and the scientific journal Nature. The procedure is said to have been deployed in mid-June 2022.
What is actually diverse from other phishing attacks is the use of a tactic Proofpoint calls Multi-Persona Impersonation (MPI), wherein the risk actor employs not just one but several actor-controlled personas in the exact email discussion to bolster the odds of good results.

The plan is to “leverage the psychology principle of social evidence” and increase the authenticity of the menace actor’s correspondence so as to make the goal invest in into the scheme, a tactic that demonstrates the adversary’s ongoing ability to stage up its activity.
“This is an intriguing strategy due to the fact it involves a lot more methods to be made use of for every goal – likely burning additional personas – and a coordinated technique amid the a variety of personalities in use by TA453,” Sherrod DeGrippo, vice president of danger analysis and detection at Proofpoint, stated in a statement.
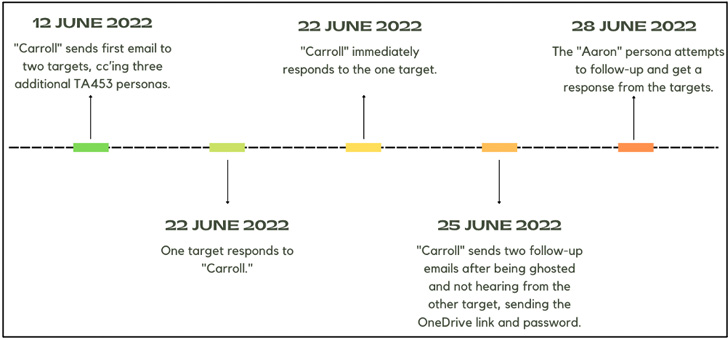
Once the first email elicits a reaction from the focus on, the persona then sends a stick to-up information made up of a malicious OneDrive website link that downloads a Microsoft Business office doc, a person of which purportedly alludes to a clash involving Russia and the U.S.
This doc subsequently utilizes a method called remote template injection to down load Korg, a template consisting of a few macros that are able of gathering usernames, a record of functioning processes, and the victims’ community IP addresses.
In addition to the exfiltration of the beaconing facts, no other post-exploitation actions have been noticed. The “irregular” deficiency of code execution and command-and-regulate habits has led to an assessment that the compromised end users could be subjected to further attacks based on the mounted application.
This is not the 1st time the danger actor has carried out impersonation campaigns. In July 2021, Proofpoint exposed a phishing operation dubbed SpoofedScholars that qualified people today focused on Center East affairs in the U.S. and the U.K. below the guise of scholars with the College of London’s University of Oriental and African Scientific tests (SOAS).
Then in July 2022, the cybersecurity firm uncovered makes an attempt on the part of TA453 to masquerade as journalists to entice lecturers and policy experts into clicking on destructive back links that redirect the targets to credential harvesting domains.

The disclosure arrives amid a flurry of Iranian-linked cyber exercise. Final 7 days, Microsoft took the wraps off a string of ransomware attacks mounted by a Phosphorus subgroup dubbed DEV-0270 utilizing residing-off-the-land binaries these types of as BitLocker.
On top of that, cybersecurity business Mandiant, which is now officially element of Google Cloud, in-depth the pursuits of an Iranian espionage actor codenamed APT42 that has been linked to about 30 functions since 2015.
To major it all, the Treasury Division declared sanctions from Iran’s Ministry of Intelligence and Security (MOIS) and its Minister of Intelligence, Esmaeil Khatib, in response to “cyber-enabled routines in opposition to the United States and its allies.”
Albania, which has severed diplomatic relations with Iran following blaming it for a sequence of cyber offensives given that July, pointed fingers at the “same aggressors” above the weekend for conducting a different attack on a governing administration method used to observe border crossings.
“Condition-aligned threat actors are some of the best at crafting well assumed-out social engineering strategies to attain their meant victims,” DeGrippo reported.
“Scientists associated in intercontinental security, significantly those specializing in Center Japanese scientific studies or nuclear security, should really preserve a heightened sense of awareness when receiving unsolicited emails.”
Discovered this write-up exciting? Comply with THN on Fb, Twitter and LinkedIn to go through much more unique content we article.
Some sections of this report are sourced from:
thehackernews.com


 Researchers Warn of 674% Surge in Deadbolt Ransomware
Researchers Warn of 674% Surge in Deadbolt Ransomware