It’s no mystery that 3rd party apps can boost productivity, empower distant and hybrid get the job done and are over-all, essential in creating and scaling a company’s work processes.
An innocuous course of action substantially like clicking on an attachment was in the before days of email, individuals don’t imagine two times when connecting an app they need with their Google workspace or M365 ecosystem, and so on. Simple actions that users choose, from creating an email to updating a speak to in the CRM, can consequence in several other computerized actions and notifications in the connected platforms.
As seen in the graphic below, the OAuth mechanism helps make it unbelievably straightforward to interconnect apps and a lot of you should not take into account what the probable ramifications could be. When these applications and other include-ons for SaaS platforms request for permissions’ access, they are normally granted with out a next assumed, presenting a lot more options for bad actors to achieve accessibility to a company’s info. This places corporations at risk for provide chain entry attacks, API takeovers and malicious 3rd party applications.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
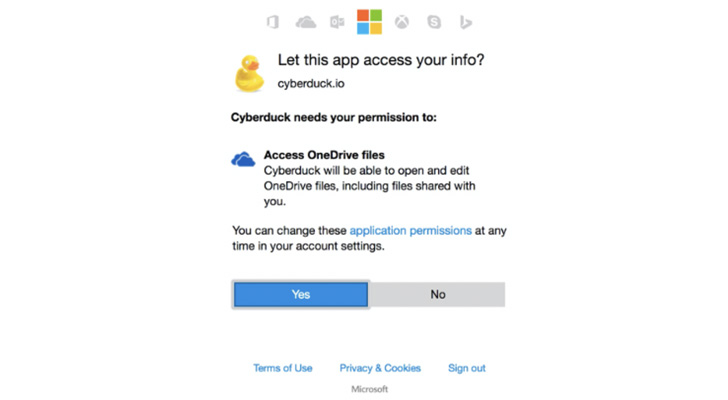 Oauth mechanism authorization ask for
Oauth mechanism authorization ask for
When it arrives to community machines and executable documents, businesses previously have regulate constructed in that permits security groups to block problematic applications and documents. It desires to be the very same when it comes to SaaS applications.
Find out how to get visibility into 3rd party applications
How Do 3rd Party Applications Obtain Accessibility?
OAuth 2. has tremendously simplified authentication and authorization, and delivers a great-grained delegation of accessibility legal rights. Represented in the kind of scopes, an software asks for the user’s authorization for distinct permissions. An app can request one or much more scopes. By means of acceptance of the scopes, the person grants these apps permissions to execute code to perform logic behind the scenes in their setting. These apps can be harmless or as threatening as an executable file.
Simply click listed here to program a 15-minute demo to understand how to get visibility of your SaaS applications
Greatest Techniques to Mitigate Third Party Application Entry Risk
To safe a company’s SaaS stack, the security team wants to be in a position to establish and monitor all that comes about within just their SaaS ecosystem. This is what a security staff can share with employees and manage them selves to mitigate third party app access risk.
1 — Teach the staff members in the business
The initially move in cybersecurity normally will come back again to boosting recognition. Once the employees turn into more conscious of the challenges and risks that these OAuth mechanisms present, they will be far more hesitant to use them. Businesses should also generate a policy that enforces staff to post requests for 3rd party apps.
2 — Attain visibility into the 3rd party entry for all company-critical apps
Security groups should gain visibility into each and every business enterprise critical application and evaluation all the distinctive third party applications that have been integrated with their business-critical SaaS apps – across all tenets. One of the initial ways when shrinking the risk area is gaining an knowledge of the total natural environment.
3 — Map the permissions and accessibility stages asked for by the linked 3rd party applications
As soon as the security crew appreciates which 3rd party applications are related, they must map the permissions and the style of accessibility that each individual third party application has been offered. From there they will be capable to see which 3rd party application presents a bigger risk, dependent on the increased degree of scope. Currently being equipped to differentiate concerning an application that can study compared to an application that can generate will aid the security crew prioritize which demands to be managed initial.
In addition, the security group must map which consumers granted these permissions. For case in point, a substantial-privileged user, someone who has delicate files in their workspace, who grants access to a 3rd party application can present a higher risk to the corporation and requirements to be remediated immediately.
4 — Get the automated strategy to handle 3rd party application access
SaaS Security Posture Administration methods can automate the discovery of 3rd party applications. The proper SSPM remedy, like Adaptive Shield, has constructed-in logic that maps out all the 3rds party applications with accessibility to the organization’s SSPM built-in applications. This visibility and oversight empowers security teams so whether a company has a 100 or 600 applications, they can very easily continue to be in regulate, keep track of and protected their company’s SaaS stack.
The More substantial SaaS Security Picture
To secure a firm’s SaaS stack, the security staff demands to be equipped to establish and keep track of all that happens inside of their SaaS ecosystem. 3rd party application accessibility is just 1 part of the SaaS Security Posture Administration picture.
Most current cybersecurity options nonetheless do not supply sufficient protection or a practical way to keep an eye on a firm’s SaaS stack, enable on your own the communications amongst their known applications and platforms, leaving organizations vulnerable and not able to successfully know or regulate which get-togethers have entry to delicate company or personal details.
Companies require to be equipped to see all the configurations and user permissions of just about every and each app, including all the 3rd party apps that have been granted accessibility by end users. This way security groups can retain manage of the SaaS stack, remediate any issues, block any apps utilizing much too numerous privileges and mitigate their risk.
Find out how to secure your 3rd party application obtain and SaaS stack
Observed this report intriguing? Stick to THN on Fb, Twitter and LinkedIn to go through extra exceptional information we article.
Some sections of this write-up are sourced from:
thehackernews.com


 India backtracks on biometric ID system warning
India backtracks on biometric ID system warning