Researchers have disclosed a new household of Android malware that abuses accessibility expert services in the gadget to hijack user qualifications and report audio and movie.
Dubbed “Oscorp” by Italy’s CERT-AGID, the malware “induce(s) the person to install an accessibility service with which [the attackers] can read what is existing and what is typed on the display.”
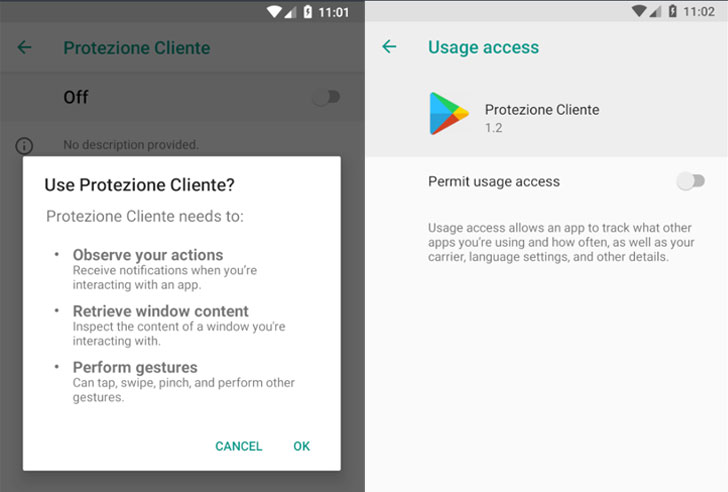
So named due to the fact of the title of the login page of its command-and-control (C2) server, the destructive APK (called “Assistenzaclienti.apk” or “Client Security”) is distributed by using a domain named “supportoapp[.]com,” which upon installation, requests intrusive permissions to permit the accessibility service and establishes communications with a C2 server to retrieve additional commands.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Furthermore, the malware regularly reopens the Options display screen just about every 8 seconds until eventually the consumer turns on permissions for accessibility and system utilization statistics, thus pressurizing the person into granting the excess privileges.
When the entry is provisioned, the malware exploits the permissions to log keystrokes, uninstall applications on the system, make phone calls, send SMS messages, steal cryptocurrency by redirecting payments designed by using Blockchain.com Wallet application, and access two-factor authentication codes from the Google Authenticator app.
The attacker-managed wallet had $584 as of January 9, the scientists mentioned.
In the ultimate phase, the malware exfiltrates the captured knowledge — alongside with process facts (e.g., applications put in, phone product, provider) — to the C2 server, in addition to fetching instructions from the server that enables it to launch the Google Authenticator application, steal SMS messages, uninstall apps, start certain URLs, and document audio and online video of the monitor through WebRTC.
What’s much more, buyers opening the applications focused by the malware are displayed a phishing web site that asks for their username and password, CERT observed, incorporating the model of this monitor differs from app to app and that it’s intended with an intent to trick the sufferer into delivering the details.
The correct sort of apps singled out by this malware stays unclear, but the researchers claimed it could be any application that specials with sensitive knowledge, this kind of as these for banking and messaging.
“Android protections avert malware from doing any kind of injury right up until the user allows [accessibility] company,” CERT-AGID concluded. “Once enabled, however, a ‘dam’ opens up. In fact, Android has normally experienced a very permissive coverage towards application developers, leaving the final selection to believe in an app or not to the end person.”
Observed this write-up fascinating? Stick to THN on Facebook, Twitter and LinkedIn to browse far more exclusive information we publish.
Some pieces of this short article are sourced from:
thehackernews.com


 10 ways to protect your company from the next big data breach
10 ways to protect your company from the next big data breach