A new pressure of Android malware has been spotted in the wild concentrating on online banking and cryptocurrency wallet customers in Spain and Italy, just months immediately after a coordinated regulation enforcement operation dismantled FluBot.
The facts thieving trojan, codenamed MaliBot by F5 Labs, is as function-abundant as its counterparts, allowing it to steal qualifications and cookies, bypass multi-factor authentication (MFA) codes, and abuse Android’s Accessibility Company to observe the victim’s machine display.
MaliBot is recognized to largely disguise alone as cryptocurrency mining apps this sort of as Mining X or The CryptoApp that are dispersed through fraudulent sites built to draw in prospective readers into downloading them.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

It also requires yet another leaf out of the cellular banking trojan playbook in that it employs smishing as a distribution vector to proliferate the malware by accessing an contaminated smartphone’s contacts and sending SMS messages made up of back links to the malware.
“MaliBot’s command-and-handle (C2) is in Russia and seems to use the exact servers that have been utilized to distribute the Sality malware,” F5 Labs researcher Dor Nizar mentioned. “It is a intensely modified re-performing of the SOVA malware, with different features, targets, C2 servers, domains, and packing schemes.”
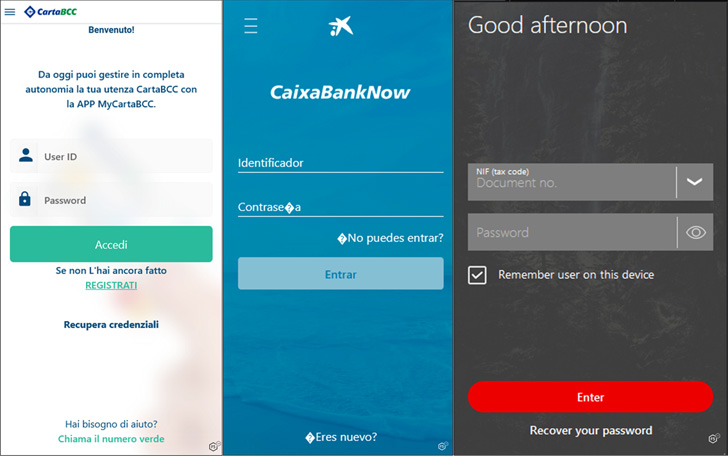
SOVA (meaning “Owl” in Russian), which was first detected in August 2021, is notable for its potential to perform overlay attacks, which do the job by exhibiting a fraudulent site employing WebView with a backlink offered by the C2 server must a victim open a banking application involved in its lively focus on list.
Some of the banking institutions specific by MaliBot using this technique incorporate UniCredit, Santander, CaixaBank, and CartaBCC.
Accessibility Support is a track record support working in Android products to assist users with disabilities. It has prolonged been leveraged by adware and trojans to capture the system contents and intercept credentials entered by unsuspecting users on other apps.

Other than staying ready to siphon passwords and cookies of the victim’s Google account, the malware is built to swipe 2FA codes from the Google Authenticator app as perfectly as exfiltrate sensitive details this sort of as whole balances and seed phrases from Binance and Belief Wallet apps.
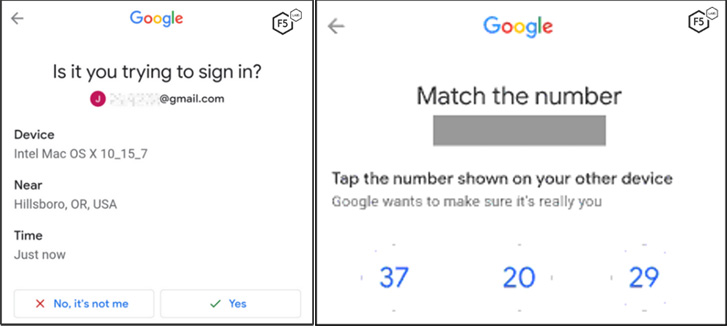
What is extra, Malibot is capable of weaponizing its entry to the Accessibility API to defeat Google’s two-factor authentication (2FA) methods, this sort of as Google prompts, even in eventualities where by an try is designed to signal in to the accounts applying the stolen qualifications from a earlier not known machine.
“The versatility of the malware and the handle it provides attackers more than the device necessarily mean that it could, in theory, be applied for a broader variety of attacks than stealing credentials and cryptocurrency,” the researchers claimed.
“In fact, any application which would make use of WebView is liable to obtaining the users’ qualifications and cookies stolen.”
Observed this report appealing? Adhere to THN on Facebook, Twitter and LinkedIn to read through far more distinctive articles we put up.
Some areas of this short article are sourced from:
thehackernews.com


 Critical Flaw in Cisco Secure Email and Web Manager Lets Attackers Bypass Authentication
Critical Flaw in Cisco Secure Email and Web Manager Lets Attackers Bypass Authentication