Microsoft is now using steps to reduce Distant Desktop Protocol (RDP) brute-pressure attacks as element of the most current builds for the Windows 11 functioning system in an attempt to raise the security baseline to meet up with the evolving danger landscape.
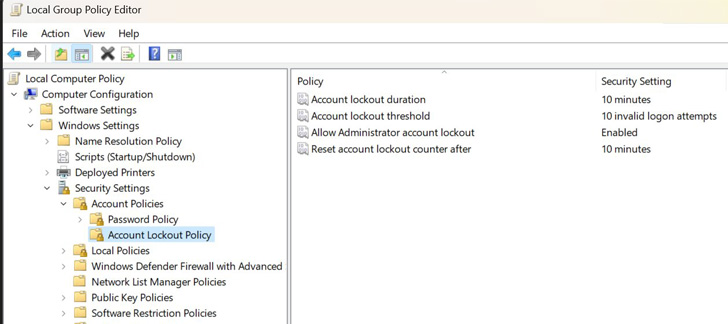
To that finish, the default coverage for Windows 11 builds – notably, Insider Preview builds 22528.1000 and newer – will instantly lock accounts for 10 minutes after 10 invalid indicator-in tries.
“Earn11 builds now have a DEFAULT account lockout coverage to mitigate RDP and other brute-pressure password vectors,” David Weston, Microsoft’s vice president for OS security and enterprise, explained in a sequence of tweets last 7 days. “This procedure is pretty commonly applied in Human Operated Ransomware and other attacks — this command will make brute forcing substantially more durable which is great!”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

It truly is worthy of pointing out that even though this account lockout location is currently included in Windows 10, it can be not enabled by default.
The element, which follows the company’s choice to resume blocking of Visual Simple Software (VBA) macros for Office environment documents, is also anticipated to be backported to more mature variations of Windows and Windows Server.
Apart from destructive macros, brute-compelled RDP access has extensive been a person of the most well-liked strategies utilized by threat actors to acquire unauthorized accessibility to Windows units.
LockBit, which is one of the most lively ransomware gangs of 2022, is recognized to normally depend on RDP for first foothold and follow-on pursuits. Other households found applying the exact same system include Conti, Hive, PYSA, Crysis, SamSam, and Dharma.

In applying this new threshold, the aim is to noticeably diminish the efficiency of the RDP attack vector and forestall intrusions that depend on password-guessing and compromised qualifications.
“Brute-forcing RDP is the most popular method applied by danger actors attempting to acquire access to Windows programs and execute malware, ” Zscaler pointed out previous calendar year.
“Danger actors scan for […] publicly open up RDP ports to carry out dispersed brute-pressure attacks. Units that use weak credentials are effortless targets, and, at the time compromised, attackers provide entry to the hacked units on the dark web to other cybercriminals.”
That said, Microsoft, in its documentation, warns of possible denial-of-company (DoS) attacks that could be orchestrated by abusing the Account lockout threshold coverage setting.
“A malicious consumer could programmatically endeavor a sequence of password attacks against all customers in the corporation,” the enterprise notes. “If the quantity of makes an attempt is larger than the price of Account lockout threshold, the attacker could perhaps lock every account.”
Discovered this posting fascinating? Abide by THN on Facebook, Twitter and LinkedIn to read extra unique material we put up.
Some components of this write-up are sourced from:
thehackernews.com


 Experts Uncover New ‘CosmicStrand’ UEFI Firmware Rootkit Used by Chinese Hackers
Experts Uncover New ‘CosmicStrand’ UEFI Firmware Rootkit Used by Chinese Hackers