Microsoft and a consortium of cybersecurity providers took authorized and complex techniques to disrupt the ZLoader botnet, seizing handle of 65 domains that had been utilized to handle and converse with the contaminated hosts.
“ZLoader is created up of computing devices in corporations, hospitals, faculties, and houses all around the environment and is operate by a world-wide internet-dependent arranged criminal offense gang running malware as a service that is developed to steal and extort funds,” Amy Hogan-Burney, standard manager of Microsoft’s Digital Crimes Device (DCU), reported.
The operation, Microsoft claimed, was carried out in collaboration with ESET, Lumen’s Black Lotus Labs, Palo Alto Networks Unit 42, Avast, Money Solutions Info Sharing and Analysis Middle (FS-ISAC), and Wellness Information and facts Sharing and Investigation Centre (H-ISAC).

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
As a end result of the disruption, the domains are now redirected to a sinkhole, proficiently blocking the botnet’s prison operators from making contact with the compromised devices. An additional 319 backup domains that were being generated by using an embedded domain generation algorithm (DGA) have also been confiscated as aspect of the identical procedure.

ZLoader, like its notorious counterpart TrickBot, commenced off as a derivative of the Zeus banking trojan in November 2019 before undergoing energetic refinements and upgrades that have enabled other risk actors to purchase the malware from underground boards and repurpose it to match their targets.
“ZLoader has remained suitable as attackers’ device of decision by such as defense evasion capabilities, like disabling security and antivirus resources, and offering obtain-as-a-support to other affiliate teams, these kinds of as ransomware operators,” Microsoft stated.
“Its capabilities incorporate capturing screenshots, gathering cookies, stealing qualifications and banking knowledge, accomplishing reconnaissance, launching persistence mechanisms, misusing authentic security tools, and supplying remote obtain to attackers.”
ZLoader’s transition from a primary monetary trojan to a innovative malware-as-a-services (MaaS) alternative has also manufactured it possible for the operators to monetize the compromises by promoting the entry to other affiliate actors, who then misuse it to deploy additional payloads like Cobalt Strike and ransomware.
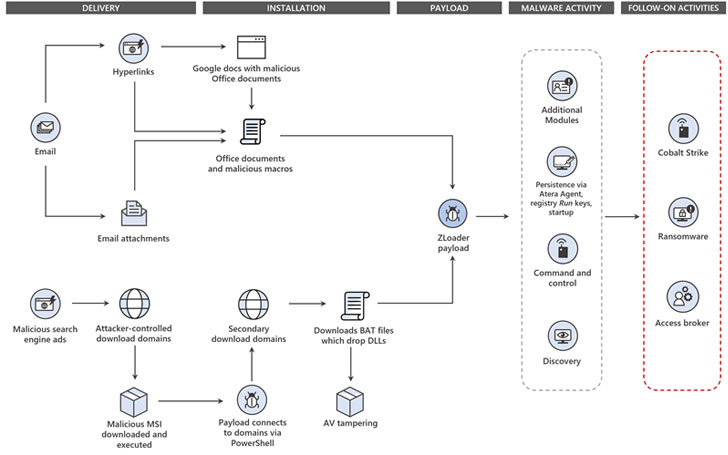
Strategies involving ZLoader have abused phishing e-mails, remote administration program, and rogue Google Adverts to gain initial entry to the target devices, when simultaneously utilizing various intricate tactics for defense evasion, such as injecting destructive code into respectable processes.
Interestingly, an examination of the malware’s malicious activities given that February 2020 has uncovered that most of the functions originated from just two affiliate marketers considering that Oct 2020: “dh8f3@3hdf#hsf23” and “03d5ae30a0bd934a23b6a7f0756aa504.”
Although the previous utilized “ZLoader’s skill to deploy arbitrary payloads to distribute destructive payloads to its bots,” the other affiliate, active to day, seems to have focussed on siphoning credentials from banking, cryptocurrency platforms, and e-commerce websites, Slovak cybersecurity company ESET mentioned.
To major it all, Microsoft also unmasked Denis Malikov, who lives in the metropolis of Simferopol on the Crimean Peninsula, as a person of the actors powering the improvement of a module used by the botnet to distribute ransomware strains, stating that it chose to identify the perpetrator to “make clear that cybercriminals will not be authorized to conceal powering the anonymity of the internet to dedicate their crimes.”
The takedown effort and hard work is reminiscent of a international procedure to disrupt the notorious TrickBot botnet in Oct 2020. Even though the botnet managed to bounce again very last year, it has due to the fact been retired by the malware authors in favor of other stealthy variants these as BazarBackdoor.
“Like numerous modern day malware variants, getting ZLoader on to a device is in many cases just the very first stage in what ends up remaining a more substantial attack,” Microsoft stated. “The trojan further more exemplifies the craze of widespread malware more and more harboring more hazardous threats.”
Discovered this article fascinating? Adhere to THN on Fb, Twitter and LinkedIn to examine additional special material we submit.
Some components of this report are sourced from:
thehackernews.com


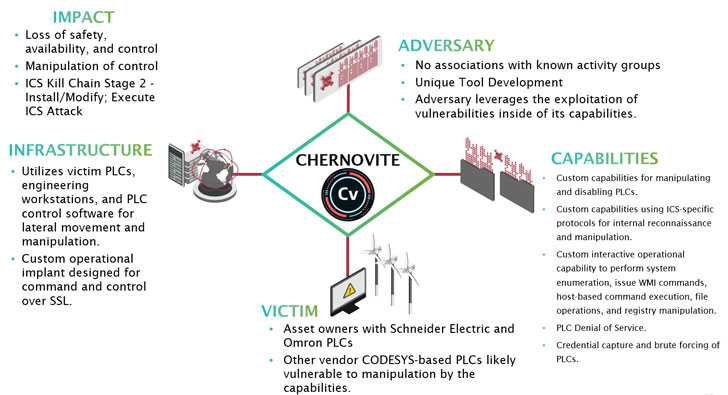
 U.S. Warns of APT Hackers Targeting ICS/SCADA Systems with Specialized Malware
U.S. Warns of APT Hackers Targeting ICS/SCADA Systems with Specialized Malware