A country-condition actor acknowledged for its cyber espionage strategies due to the fact 2012 is now utilizing coin miner tactics to stay beneath the radar and set up persistence on target devices, in accordance to new exploration.
Attributing the change to a threat actor tracked as Bismuth, Microsoft’s Microsoft 365 Defender Danger Intelligence Workforce said the team deployed Monero coin miners in attacks that specific both the non-public sector and govt establishments in France and Vietnam among July and August earlier this yr.
“The coin miners also allowed Bismuth to cover its much more nefarious routines behind threats that may possibly be perceived to be considerably less alarming due to the fact they are ‘commodity’ malware,” the researchers said in an analysis revealed yesterday.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The principal victims of the attack have been traced to condition-owned enterprises in Vietnam and entities with ties to a Vietnamese federal government company.
The Windows maker likened Bismuth to OceanLotus (or APT32), linking it to spyware attacks applying both of those customized and open-supply toolsets to concentrate on large multinational organizations, governments, economical services, instructional institutions, and human and civil legal rights corporations.
The advancement arrives as OceanLotus was located leveraging a new macOS backdoor that permits the attackers to snoop on and steals confidential info and sensitive company documents from contaminated equipment.
Using Coin Miners to Blend In
Whilst the group’s espionage and exfiltration techniques have fundamentally remained the exact, the inclusion of coin miners in their arsenal points to a contemporary way to monetize compromised networks, not to mention a crafty means of mixing in and evading detection for as extensive as doable.
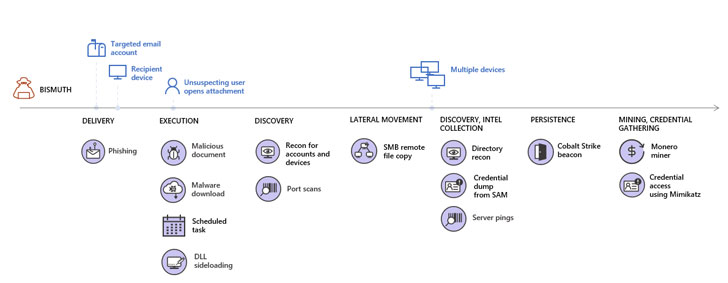
The idea is to get time to shift laterally and infect superior-benefit targets like servers for even further propagation.
To accomplish this, tailored spear-phishing e-mails prepared in Vietnamese have been crafted to precise recipients in a concentrate on corporation, and in some conditions, the menace actor even set up correspondence with the targets in a bid to increase the chances of opening the destructive doc embedded in the emails and bring about the an infection chain.
A individual method included the use of DLL facet-loading, wherein a legitimate library is changed with a malicious variant, employing outdated versions of authentic application these kinds of as Microsoft Defender Antivirus, Sysinternals DebugView, and Microsoft Term 2007 to load rogue DLL information and build a persistent command-and-control (C2) channel to the compromised device and the network.
The newly set up channel was then utilized to drop a number of future-phase payloads, including applications for network scanning, credential theft, Monero coin mining, and conducting reconnaissance, the outcomes of which have been transmitted back to the server in the variety of a “.csv” file.
Hiding in Basic Sight
“Bismuth attacks set strong emphasis on hiding in basic sight by mixing in with normal network action or prevalent threats that attackers anticipate will get very low-priority notice,” Microsoft explained.
“The combination of social engineering and use of authentic programs to sideload malicious DLLs entail various layers of security concentrated on halting threats at the earliest achievable phase and mitigating the development of attacks if they deal with to slip as a result of.”
It can be proposed that corporations restrict the attack floor utilised to attain initial accessibility by beefing up email filtering and firewall configurations, enforce credential cleanliness, and turn on multi-factor authentication.
Observed this short article appealing? Adhere to THN on Fb, Twitter and LinkedIn to browse far more exclusive content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 4 Free Online Cyber Security Testing Tools For 2021
4 Free Online Cyber Security Testing Tools For 2021