Cybersecurity scientists on Tuesday disclosed 16 new large-severity vulnerabilities in many implementations of Unified Extensible Firmware Interface (UEFI) firmware impacting various HP company equipment.
The shortcomings, which have CVSS scores ranging from 7.5 to 8.8, have been uncovered in HP’s UEFI firmware. The wide range of devices influenced consists of HP’s laptops, desktops, issue-of-sale (PoS) systems, and edge computing nodes.
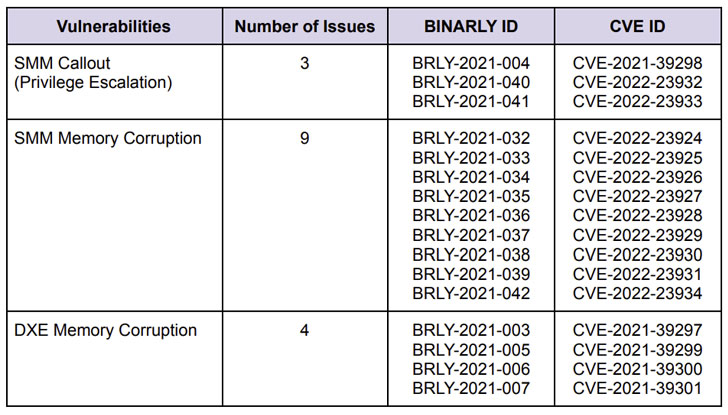
“By exploiting the vulnerabilities disclosed, attackers can leverage them to perform privileged code execution in firmware, underneath the operating procedure, and potentially provide persistent destructive code that survives functioning method re-installations and allows the bypass of endpoint security methods (EDR/AV), Protected Boot and Virtualization-Centered Security isolation,” firmware security business Binarly explained in a report shared with The Hacker Information.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The most intense of the flaws worry a range of memory corruption vulnerabilities in the System Administration Mode (SMM) of the firmware, thus enabling the execution of arbitrary code with the highest privileges.
Subsequent a coordinated disclosure approach with HP and CERT Coordination Middle (CERT/CC), the issues had been dealt with as portion of a collection of security updates transported in February and March 2022.
“Sad to say, most of the issues […] are repeatable failures, some of which are due to the complexity of the codebase or legacy parts that get much less security interest, but are continue to widely employed in the industry,” the scientists pointed out.
The disclosure comes a tiny in excess of a month just after Binarly publicized the discovery of 23 superior-effect vulnerabilities in Insyde Software’s InsydeH2O UEFI firmware that could be weaponized to deploy persistent malware that’s able of evading security systems.
The newest conclusions are also important in light of the fact that firmware has emerged as an ever-expanding attack area for risk actors to launch hugely-qualified devastating attacks. At the very least five unique firmware malware strains have been detected in the wild to date because 2018.
“Securing the firmware layer is usually ignored, but it is a one place of failure in equipment and is a person of the stealthiest methods in which an attacker can compromise units at scale,” the U.S. Commerce and Homeland Security departments highlighted in a report posted last thirty day period.
Observed this write-up exciting? Comply with THN on Facebook, Twitter and LinkedIn to study extra distinctive content we article.
Some areas of this report are sourced from:
thehackernews.com



 Prison for Man Who Scammed US Government to Buy Pokémon Card
Prison for Man Who Scammed US Government to Buy Pokémon Card