Cryptocurrency buyers in Ethiopia, Nigeria, India, Guatemala, and the Philippines are remaining targeted by a new variant of the Phorpiex botnet termed Twizt that has resulted in the theft of digital cash amounting to $500,000 around the final a person calendar year.
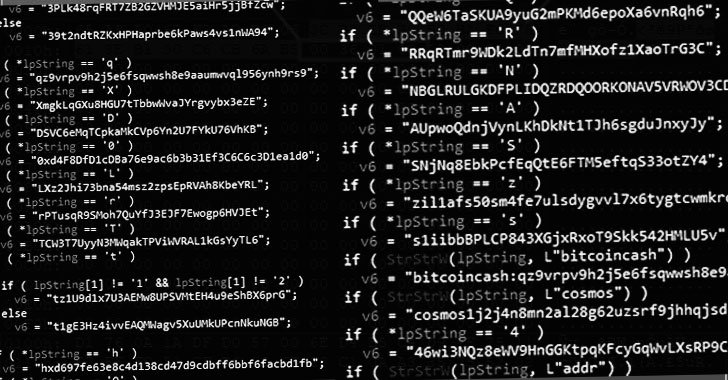
Israeli security business Check Level Research, which in depth the attacks, stated the most up-to-date evolutionary edition “permits the botnet to function correctly with no active [command-and-control] servers,” incorporating it supports no much less than 35 wallets involved with distinct blockchains, like Bitcoin, Ethereum, Dash, Dogecoin, Litecoin, Monero, Ripple, and Zilliqa, to aid crypto theft.
Phorpiex, usually regarded as Trik, is regarded for its sextortion spam and ransomware campaigns as effectively as cryptojacking, a plan that leverages the targets’ units these types of as desktops, smartphones, and servers to secretly mine cryptocurrency with no their consent or understanding.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

It is also notorious for its use of a method identified as cryptocurrency clipping, which requires thieving cryptocurrency in the system of a transaction by deploying malware that quickly substitutes the supposed wallet address with the danger actor’s wallet handle. Verify Issue stated it identified 60 exceptional Bitcoin wallets and 37 Ethereum wallets employed by Phorpiex.
Though the botnet operators shut down and place its source code for sale on a dark web cybercrime forum in August 2021, the command-and-regulate (C&C) servers resurfaced a mere two months later to distribute Twizt, a formerly undiscovered payload that can deploy supplemental malware and perform in peer-to-peer method, so eliminating the will need for a centralized C&C server.
The clipping characteristic also comes with an added edge in that, the moment deployed, it can work even in the absence of any C&C servers and siphon dollars from victims’ wallets. “This usually means that each and every of the contaminated pcs can act as a server and send instructions to other bots in a chain,” Examine Point’s Alexey Bukhteyev explained in a report. “The emergence of such options indicates that the botnet may perhaps turn out to be even much more steady and for that reason, more unsafe.”
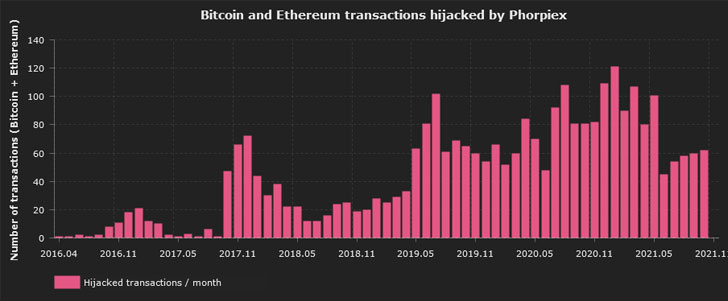
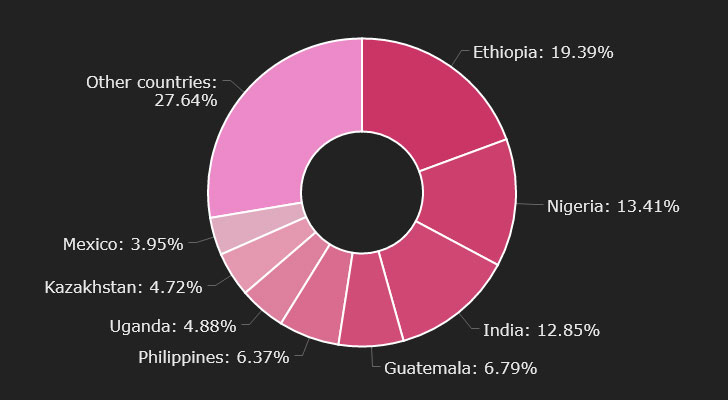
Phorpiex-infected bots have been noticed in 96 nations, topped by Ethiopia, Nigeria, and India. The botnet is also estimated to have hijacked approximately 3,000 transactions with a complete worth of somewhere around 38 Bitcoin and 133 Ether. It is really, on the other hand, worthy of noting that the botnet is created to halt its execution really should the contaminated system’s locale be defaulted to Ukraine, suggesting that the botnet operators are from the East European nation.
“Malware with the features of a worm or a virus can keep on to distribute autonomously for a very long time devoid of any more involvement by its creators,” Bukhteyev stated. “In the previous year, Phorpiex received a major update that remodeled it into a peer-to-peer botnet, letting it to be managed without having a centralized infrastructure. The C&C servers can now change their IP addresses and issue instructions, hiding among the the botnet victims.”
Found this write-up appealing? Adhere to THN on Facebook, Twitter and LinkedIn to study much more exclusive content material we write-up.
Some areas of this posting are sourced from:
thehackernews.com


 New Jersey Cancer Care Providers Settle Data Breach Claim
New Jersey Cancer Care Providers Settle Data Breach Claim