A new ransomware marketing campaign qualified the transportation and logistics sectors in Ukraine and Poland on October 11 with a beforehand unidentified payload dubbed Prestige.
“The action shares victimology with latest Russian state-aligned action, precisely on afflicted geographies and nations around the world, and overlaps with former victims of the FoxBlade malware (also recognised as HermeticWiper),” the Microsoft Menace Intelligence Middle (MSTIC) said.
The tech large remarked the intrusions occurred within just an hour of every other throughout all victims, attributing the infections to an unnamed cluster termed DEV-0960. It did not disclose the scale of the attacks, but stated it can be notifying all impacted clients.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The campaign is also believed to be distinctive from other modern damaging attacks that have concerned the use of HermeticWiper and CaddyWiper, the latter of which is introduced by a malware loader named ArguePatch (aka AprilAxe).

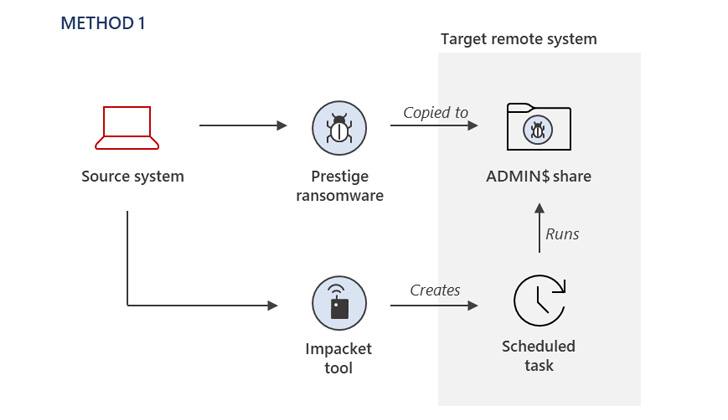
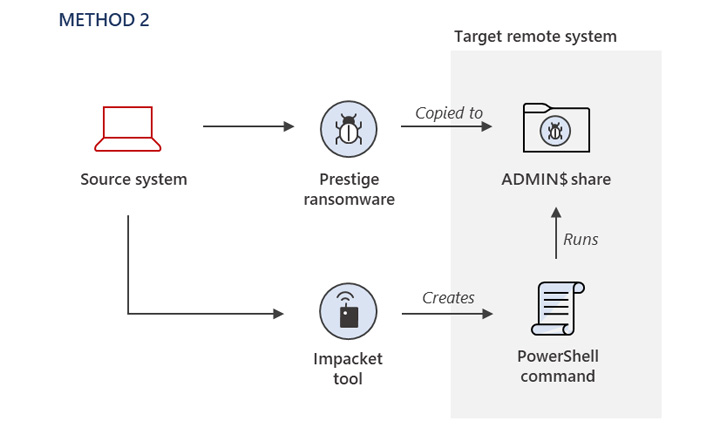
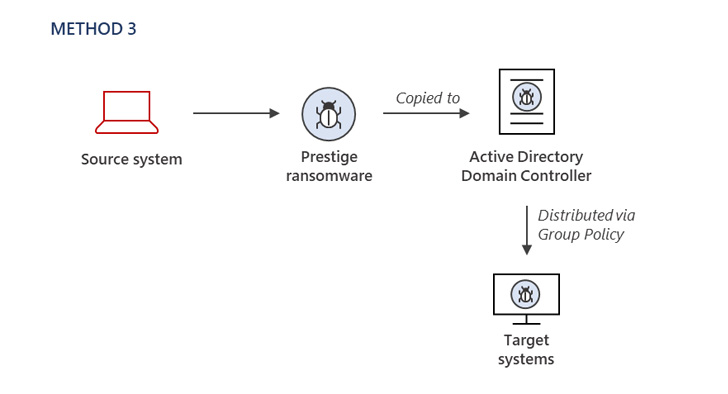
The process of original entry stays mysterious, with Microsoft noting that the danger actor had now obtained privileged entry to the compromised environment to deploy the ransomware employing a few distinct procedures.
In a similar enhancement, Fortinet FortiGuard Labs took the wraps off a multi-stage attack chain that leverages a weaponized Microsoft Excel document, which masquerades as a spreadsheet for creating salaries for Ukrainian navy staff to fall Cobalt Strike Beacon.
“The threat landscape in Ukraine carries on to evolve, and wipers and harmful attacks have been a steady concept,” Redmond noted. “Ransomware and wiper attacks rely on several of the exact security weaknesses to realize success.”
The results come amid an explosion of relatively new ransomware strains that have been getting traction on the danger landscape, like that of Bisamware, Chile Locker, Royal, and Ransom Cartel, more than the previous couple months.
Ransom Cartel, which surfaced in mid-December 2021, is also noteworthy for sharing technical overlaps with REvil ransomware, which shut store in Oct 2021 adhering to immense legislation enforcement scrutiny into its operations just after a string of higher-profile attacks on JBS and Kaseya.
It is suspected that “Ransom Cartel operators had accessibility to before variations of REvil ransomware supply code,” Palo Alto Networks Device 42 observed on October 14, stating that “there was a romantic relationship between the teams at some position, while it may not have been latest.”

REvil, earlier this January, suffered additional setback when Russian authorities arrested a number of associates, but there are indications that the notorious cybercrime cartel might have staged a return in some variety.
Cybersecurity firm Trellix, in late September, also exposed how a “disgruntled internal resource” from the team shared specifics about the adversary’s Practices, Tactics and Procedures (TTPs), lending a critical insight into the “relationships and inner workings of REvil and its members.”
It can be not just REvil that’s back again on the ransomware radar. HP Wolf Security previous 7 days stated it isolated a Magniber marketing campaign that has been found targeting Windows household end users with pretend security updates which employ a JavaScript file to proliferate the file-encrypting malware.
“The attackers utilized clever tactics to evade security and detection mechanisms,” malware analyst Patrick Schläpfer pointed out. “Most of the infection chain is ‘fileless,’ that means the malware only resides in memory, lowering the odds of it remaining detected.”
Uncovered this post appealing? Adhere to THN on Fb, Twitter and LinkedIn to browse far more exceptional content material we publish.
Some components of this report are sourced from:
thehackernews.com


 Spanish Police Bust Region’s “Biggest Narco Bank”
Spanish Police Bust Region’s “Biggest Narco Bank”