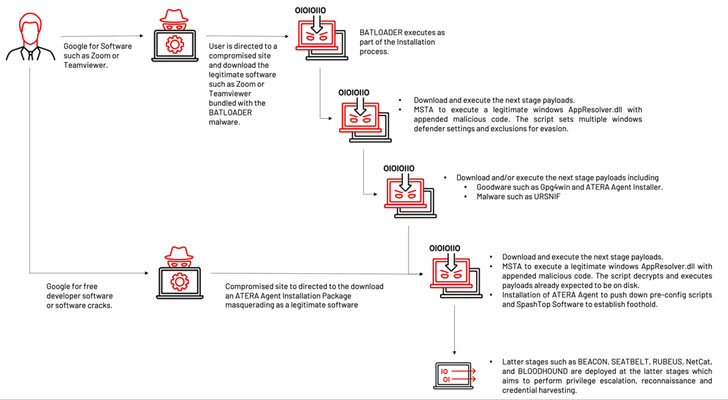
An ongoing search motor optimization (Search engine optimization) poisoning attack campaign has been observed abusing have faith in in legitimate software program utilities to trick people into downloading BATLOADER malware on compromised devices.
“The menace actor made use of ‘free efficiency applications installation’ or ‘free program enhancement resources installation’ themes as Seo key terms to lure victims to a compromised web page and to down load a malicious installer,” researchers from Mandiant claimed in a report published this 7 days.
In Search engine optimisation poisoning attacks, adversaries artificially enhance the lookup motor ranking of internet websites (authentic or in any other case) hosting their malware to make them present up on major of look for final results so that buyers seeking for unique apps like TeamViewer, Visual Studio, and Zoom are infected with malware.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The installer, although packing the reputable software package, is also bundled with the BATLOADER payload which is executed during the set up method. The malware then acts as a stepping stone for attaining more perception into the qualified firm by downloading upcoming-stage executables that propagate the multi-stage an infection chain.
1 of those people executables is a tampered version of an internal element of Microsoft Windows that’s appended with a malicious VBScript. The attack subsequently leverages a system referred to as signed binary proxy execution to operate the DLL file applying the legitimate “Mshta.exe” utility.
This outcomes in the execution of the VBScript code, proficiently triggering the upcoming stage of the attack whereby additional payloads this sort of as Atera Agent, Cobalt Strike Beacon, and Ursnif are delivered in the afterwards levels to enable conduct remote reconnaissance, privilege escalation, and credential harvesting.
What is a lot more, in a indicator that the operators experimented with distinctive ploys, an alternative variant of the same marketing campaign sent the Atera remote checking administration software directly as a consequence of the first compromise for further stick to-on post-exploitation pursuits.
Mandiant also named out the attacks’ overlaps with that of tactics adopted by the Conti ransomware gang, which have been publicized in August 2021. “At this time, because of to the community release of this info, other unaffiliated actors may perhaps be replicating the strategies for their very own motives and goals,” the researchers explained.
Identified this short article attention-grabbing? Comply with THN on Fb, Twitter and LinkedIn to study extra distinctive written content we post.
Some parts of this posting are sourced from:
thehackernews.com



 Online Thieves Steal $320m from Crypto Firm Wormhole
Online Thieves Steal $320m from Crypto Firm Wormhole