Cybersecurity researchers have taken the wraps off a previously undocumented and stealthy customized malware termed SockDetour that focused U.S.-based mostly protection contractors with the objective of becoming made use of as a secondary implant on compromised Windows hosts.
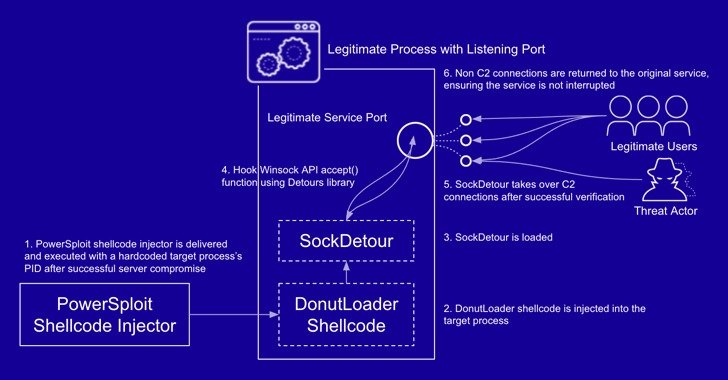
“SockDetour is a backdoor that is designed to keep on being stealthily on compromised Windows servers so that it can provide as a backup backdoor in circumstance the key one particular fails,” Palo Alto Networks’ Unit 41 risk intelligence claimed in a report published Thursday. “It is tough to detect, considering the fact that it operates filelessly and socketlessly on compromised Windows servers.”
Even much more concerningly, SockDetour is believed to have been used in attacks due to the fact at minimum July 2019, based mostly on a compilation timestamp on the sample, implying that the backdoor effectively managed to slip earlier detection for in excess of two-and-a-50 percent decades.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The attacks have been attributed to a risk cluster it tracks as TiltedTemple (aka DEV-0322 by Microsoft), which is selected moniker for a hacking group running out of China and was instrumental in exploiting zero-day flaws in Zoho ManageEngine ADSelfService Plus and ServiceDesk In addition deployments as a launchpad for malware attacks last 12 months.
The ties to TiltedTemple appear from overlaps in the attack infrastructure, with just one of the command-and-control (C2) servers that was utilized to facilitate the distribution of malware for the late 2021 strategies also hosting the SockDetour backdoor, together with a memory dumping utility and variety of web shells for distant access.
Device 42 reported it unearthed proof of at minimum four defense contractors targeted by the new wave of attacks, ensuing in the compromise of one particular of them.
The intrusions also predate the attacks that happened by means of compromised Zoho ManageEngine servers in August 2021 by a thirty day period. Investigation of the marketing campaign has uncovered that SockDetour was sent from an exterior FTP server to a U.S.-based mostly protection contractor’s internet-going through Windows server on July 27, 2021.
“The FTP server that hosted SockDetour was a compromised High-quality Network Appliance Service provider (QNAP) compact place of work and home business office (SOHO) network-hooked up storage (NAS) server,” the scientists pointed out. “The NAS server is recognised to have numerous vulnerabilities, like a remote code execution vulnerability, CVE-2021-28799.”
What is additional, the very same server is mentioned to have been already contaminated with the QLocker ransomware, elevating the likelihood the TiltedTemple actor leveraged the exact flaw to attain unauthorized first obtain.
SockDetour, for its element, is fashioned as a stand-in backdoor that hijacks authentic processes network sockets to create its personal encrypted C2 channel, followed by loading an unknown plugin DLL file retrieved from the server.
“Consequently, SockDetour needs neither opening a listening port from which to acquire a relationship nor contacting out to an external network to set up a remote C2 channel,” the researchers explained. “This can make the backdoor much more tricky to detect from both equally host and network degree.”
Discovered this article attention-grabbing? Comply with THN on Fb, Twitter and LinkedIn to go through far more distinctive content material we article.
Some pieces of this article are sourced from:
thehackernews.com


 CISA Issues MuddyWater Warning
CISA Issues MuddyWater Warning