Scientists have disclosed a new variety of attack that exploits misconfigurations in transport layer security (TLS) servers to redirect HTTPS visitors from a victim’s web browser to a different TLS service endpoint positioned on another IP deal with to steal delicate details.
The attacks have been dubbed ALPACA, quick for “Application Layer Protocol Confusion – Examining and mitigating Cracks in tls Authentication,” by a team of academics from Ruhr College Bochum, Münster College of Used Sciences, and Paderborn University.
“Attackers can redirect targeted visitors from a person subdomain to an additional, resulting in a valid TLS session,” the analyze mentioned. “This breaks the authentication of TLS and cross-protocol attacks may possibly be possible where by the conduct of 1 protocol service may perhaps compromise the other at the software layer.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
TLS is a cryptographic protocol underpinning several application layer protocols like HTTPS, SMTP, IMAP, POP3, and FTP to protected communications over a network with the goal of incorporating a layer of authentication and preserving integrity of exchanged details though in transit.

ALPACA attacks are attainable mainly because TLS does not bind a TCP relationship to the intended application layer protocol, the researchers elaborated. The failure of TLS to secure the integrity of the TCP relationship could hence be abused to “redirect TLS site visitors for the intended TLS assistance endpoint and protocol to a different, substitute TLS provider endpoint and protocol.”
Given a customer (i.e., web browser) and two software servers (i.e., the supposed and substitute), the objective is to trick the substitute server into accepting application facts from the client, or vice versa. Given that the shopper takes advantage of a particular protocol to open a safe channel with the supposed server (say, HTTPS) when the substitute server employs a diverse application layer protocol (say, FTP) and operates on a separate TCP endpoint, the mix-up culminates in what’s identified as a cross-protocol attack.
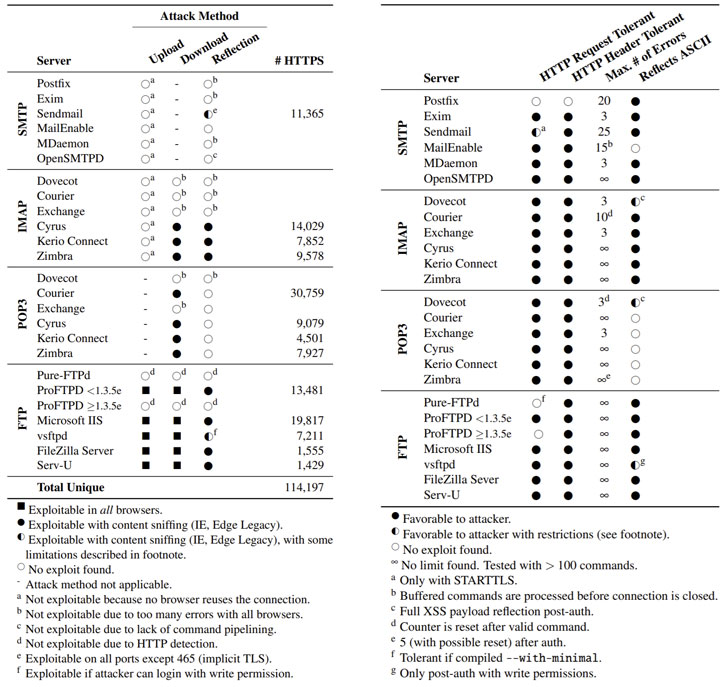
At the very least 3 hypothetical cross-protocol attack eventualities have been uncovered, which can be leveraged by an adversary to circumvent TLS protections and focus on FTP and email servers. The attacks, even so, hinge on the prerequisite that the perpetrator can intercept and divert the victim’s website traffic at the TCP/IP layer.
Place simply, the attacks acquire the type of a gentleman-in-the-center (MitM) scheme whereby the destructive actor entices a victim into opening a web site underneath their handle to cause a cross-origin HTTPS request with a specially crafted FTP payload. This request is then redirected to an FTP server that works by using a certificate that’s compatible with that of the website, culminating in a valid TLS session.
Therefore, the misconfiguration in TLS services can be exploited to exfiltrate authentication cookies or other personal information to the FTP server (Add Attack), retrieve a destructive JavaScript payload from the FTP server in a saved XSS attack (Obtain Attack), or even execute a reflected XSS in the context of the target web page (Reflection Attack).

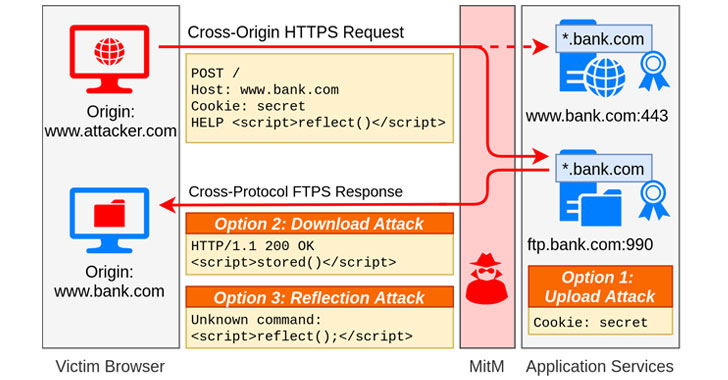
All TLS servers that have suitable certificates with other TLS solutions are anticipated to be afflicted. In an experimental setup, the researchers found that at minimum 1.4 million web servers had been vulnerable to cross-protocol attacks, with 114,197 of the servers deemed inclined to attacks working with an exploitable SMTP, IMAP, POP3, or FTP server with a trusted and compatible certificate.
To counter cross-protocol attacks, the researchers suggest employing Software Layer Protocol Negotiation (ALPN) and Server Name Indication (SNI) extensions to TLS that can be applied by a client to let the server know about the intended protocol to be utilized over a protected connection and the hostname it is really attempting to link to at the get started of the handshake process.
The results are envisioned to be offered at Black Hat United states of america 2021 and at USENIX Security Symposium 2021. Supplemental artifacts suitable to the ALPACA attack can be accessed through GitHub in this article.
Observed this short article intriguing? Comply with THN on Fb, Twitter and LinkedIn to study more distinctive content material we put up.
Some components of this article are sourced from:
thehackernews.com

 Intel Plugs 29 Holes in CPUs, Bluetooth, Security
Intel Plugs 29 Holes in CPUs, Bluetooth, Security