A point out-backed risk actor with ties to the Democratic People’s Republic of Korea (DRPK) has been attributed to a spear-phishing marketing campaign focusing on journalists covering the nation with the greatest intention of deploying a backdoor on contaminated Windows techniques.
The intrusions, reported to be the get the job done of Ricochet Chollima, resulted in the deployment of a novel malware strain termed GOLDBACKDOOR, an artifact that shares specialized overlaps with yet another malware named BLUELIGHT, which has been previously connected to the group.
“Journalists are large-value targets for hostile governments,” cybersecurity company Stairwell said in a report printed very last 7 days. “Compromising a journalist can offer access to extremely-sensitive details and permit added attacks against their sources.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Ricochet Chollima, also regarded as APT37, InkySquid, and ScarCruft, is a North Korean-nexus qualified intrusion adversary that has been associated in espionage attacks considering the fact that at least 2016. The threat actor has a keep track of report of focusing on the Republic of Korea with a noted concentrate on federal government officials, non-governmental companies, academics, journalists, and North Korean defectors.
In November 2021, Kaspersky unearthed evidence of the hacking crew offering a beforehand undocumented implant termed Chinotto as component of a new wave of extremely-qualified surveillance attacks, while other prior operations have designed use of a remote obtain resource named BLUELIGHT.
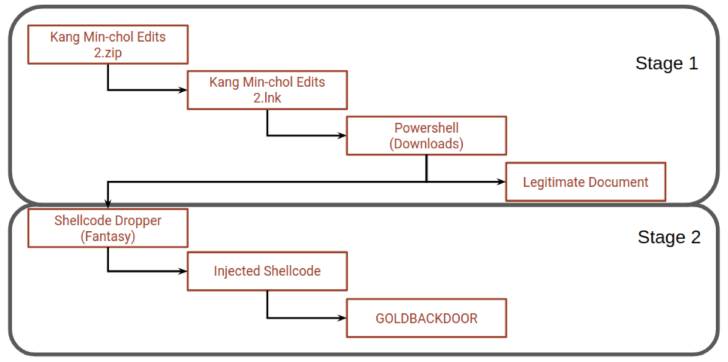
Stairwell’s investigation into the marketing campaign arrives months just after NK Information disclosed that the lure messages have been despatched from a personal email tackle belonging to a former South Korean intelligence official, eventually leading to the deployment of the backdoor in a multi-phase infection approach to evade detection.

The email messages had been found to contain a backlink to obtain a ZIP archive from a distant server made to impersonate the North Korea-focused news portal. Embedded within the file is a Windows shortcut file that functions as a jumping-off stage to execute the PowerShell script, which opens a decoy document though at the same time setting up the GOLDBACKDOOR backdoor.
The implant, for its element, is fashioned as a Moveable Executable file that’s capable of retrieving commands from a distant server, uploading and downloading information, recording information, and remotely uninstalling by itself from the compromised devices.
“More than the previous 10 decades, the Democratic People’s Republic of Korea DPRK has adopted cyber operations as a essential usually means of supporting the routine,” Stairwell’s Silas Cutler claimed.
“Whilst major notice has been compensated to the purported use of these functions as a usually means of funding DPRK’s army packages, the targeting of scientists, dissidents, and journalists probably remains a vital spot for supporting the country’s intelligence functions.”
Identified this write-up attention-grabbing? Comply with THN on Fb, Twitter and LinkedIn to read additional unique articles we article.
Some pieces of this article are sourced from:
thehackernews.com



 Security Teams Should Be Addressing Quantum Cyber-Threats Now
Security Teams Should Be Addressing Quantum Cyber-Threats Now