Cybersecurity researchers have decoded the mechanism by which the functional Qakbot banking trojan handles the insertion of encrypted configuration details into the Windows Registry.
Qakbot, also identified as QBot, QuackBot and Pinkslipbot, has been observed in the wild given that 2007. Even though largely fashioned as an data-stealing malware, Qakbot has because shifted its targets and obtained new features to supply publish-compromise attack platforms these kinds of as Cobalt Strike Beacon, with the ultimate objective of loading ransomware on contaminated equipment.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“It has been constantly developed, with new capabilities released these as lateral movement, the ability to exfiltrate email and browser data, and to set up additional malware,” Trustwave scientists Lloyd Macrohon and Rodel Mendrez mentioned in a report shared with The Hacker News.
In the latest months, phishing campaigns have culminated in the distribution of a new loader named SQUIRRELWAFFLE, which acts as a channel to retrieve ultimate-phase payloads these kinds of as Cobalt Strike and QBot.
Newer variations of Qakbot have also received the means to hijack email and browser information as well as insert encrypted configuration data pertaining to the malware into the registry as opposed to crafting them to a file on disk as component of its attempts to go away no trace of the infection.
“Even though QakBot is not heading fully fileless, its new methods will absolutely lessen its detection,” Hornetsecurity researchers pointed out in December 2020.
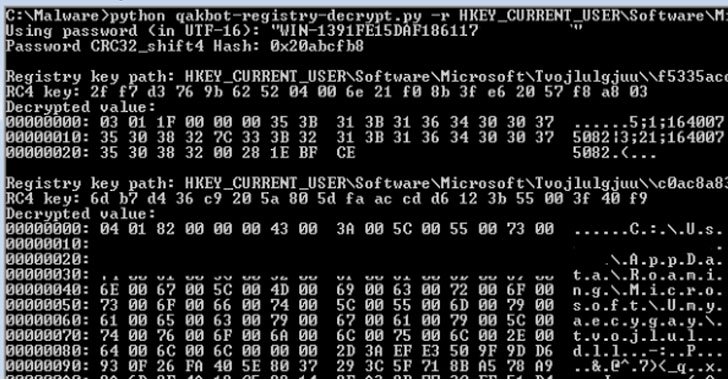
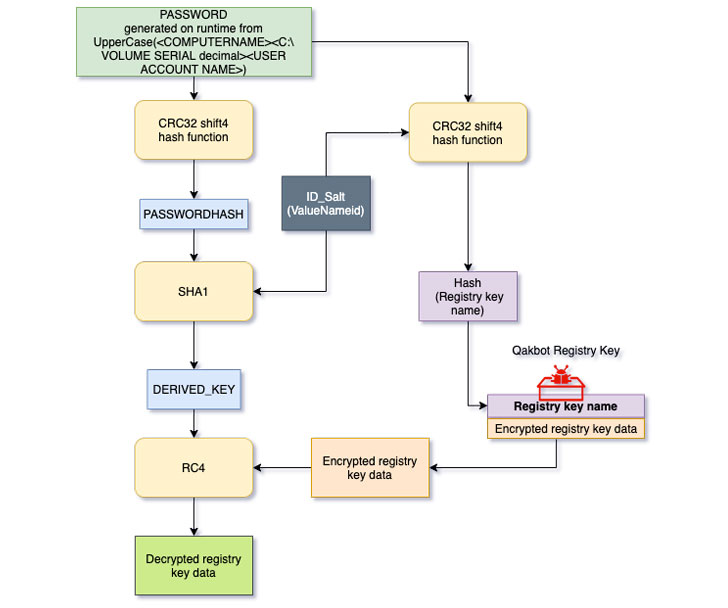
Trustwave’s investigation into the malware aims to reverse engineer this system and decrypt the configuration stored in the registry crucial, with the cybersecurity business noting that the important employed to encrypt the registry critical price details is derived from a blend of computer system identify, volume serial selection, and the user account title, which is then hashed and salted together with a 1-byte identifier (ID).
“The SHA1 hash result will be made use of as a derived important to decrypt the registry crucial value knowledge respective to the ID employing the RC4 algorithm,” the researchers reported, in addition to creating readily available a Python-primarily based decryptor utility that can be applied to extract the configuration from the registry.
Located this short article appealing? Observe THN on Fb, Twitter and LinkedIn to go through extra exceptional content we submit.
Some pieces of this posting are sourced from:
thehackernews.com


 Adobe Cloud Abused to Steal Office 365, Gmail Credentials
Adobe Cloud Abused to Steal Office 365, Gmail Credentials