A menace actor tracked as Polonium has been connected to more than a dozen really targeted attacks aimed at Israelian entities with seven different customized backdoors given that at the very least September 2021.
The intrusions have been aimed at corporations in different verticals, these as engineering, data technology, regulation, communications, branding and promoting, media, insurance, and social companies, cybersecurity firm ESET mentioned.
Polonium is the chemical element-themed moniker specified by Microsoft to a innovative operational group that is believed to be based mostly in Lebanon and is recognized to exclusively strike Israeli targets.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Activities carried out by the group 1st came to light before this June when the Windows maker disclosed it suspended a lot more than 20 malicious OneDrive accounts created by the adversary for command-and-manage (C2) functions.

Core to the attacks has been the use of implants coined CreepyDrive and CreepyBox for their skill to exfiltrate delicate data to actor-controlled OneDrive and Dropbox accounts. Also deployed is a PowerShell backdoor dubbed CreepySnail.
ESET’s most recent discovery of five a lot more earlier undocumented backdoors provides into concentrate an lively espionage-oriented danger actor that is continuously refining and retooling its malware arsenal.
“The several variations and adjustments Polonium launched into its customized instruments clearly show a steady and lengthy-time period effort and hard work to spy on the group’s targets,” ESET researcher Matías Porolli reported. “The team doesn’t appear to be to interact in any sabotage or ransomware actions.”
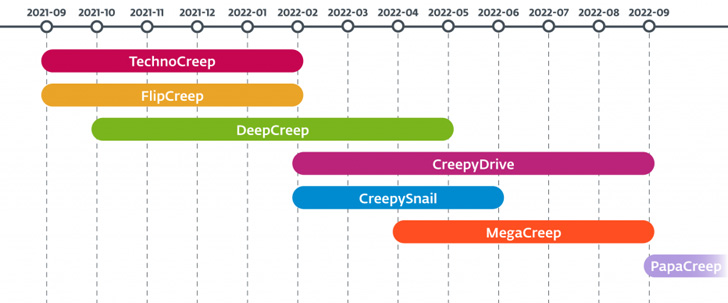
The checklist of bespoke hacking equipment is as follows –
- CreepyDrive/CreepyBox – A PowerShell backdoor that reads and executes commands from a text file saved on OneDrive or Dropbox.
- CreepySnail – A PowerShell backdoor that gets commands from the attacker’s own C2 server
- DeepCreep – A C# backdoor that reads instructions from a text file saved in Dropbox accounts and exfiltrates info
- MegaCreep – A C# backdoor that reads commands from a text file saved in Mega cloud storage service
- FlipCreep – A C# backdoor that reads commands from a textual content file saved in an FTP server and exfiltrates details
- TechnoCreep – A C# backdoor that communicates with the C2 server by using TCP sockets to execute commands and exfiltrate facts
- PapaCreep – A C++ backdoor that can get and execute commands from a remote server via TCP sockets
PapaCreep, noticed as not long ago as September 2022, is a modular malware that includes four unique factors that are created to run instructions, obtain and ship commands and their outputs, and add and obtain files.

The Slovak cybersecurity organization mentioned it also uncovered several other modules liable for logging keystrokes, capturing screenshots, using pictures by way of webcam, and establishing a reverse shell on the compromised device.
Despite the abundance of malware used in the attacks, the initial entry vector made use of to breach the networks is currently mysterious, though it is really suspected that it might have concerned the exploitation of VPN flaws.
“Most of the group’s destructive modules are tiny, with confined functionality,” Porolli claimed. “They like to divide the code in their backdoors, distributing destructive functionality into numerous modest DLLs, potentially expecting that defenders or scientists will not notice the comprehensive attack chain.”
Discovered this post exciting? Stick to THN on Fb, Twitter and LinkedIn to browse additional distinctive articles we article.
Some elements of this write-up are sourced from:
thehackernews.com


 FormBook Tops Check Point’s Most Wanted Malware List For September
FormBook Tops Check Point’s Most Wanted Malware List For September