The operators behind the Qakbot malware are transforming their shipping vectors in an try to sidestep detection.
“Most just lately, threat actors have transformed their tactics to evade detection by working with ZIP file extensions, enticing file names with widespread formats, and Excel (XLM) 4. to trick victims into downloading destructive attachments that put in Qakbot,” Zscaler Threatlabz researchers Tarun Dewan and Aditya Sharma claimed.
Other procedures adopted by the team include code obfuscation, introducing new layers in the attack chain from original compromise to execution, and employing numerous URLs as effectively as not known file extensions (e.g., .OCX, .ooccxx, .dat, or .gyp) to produce the payload.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Also called QBot, QuackBot, or Pinkslipbot, Qakbot has been a recurring menace due to the fact late 2007, evolving from its first days as a banking trojan to a modular data stealer able of deploying next-phase payloads this kind of as ransomware.
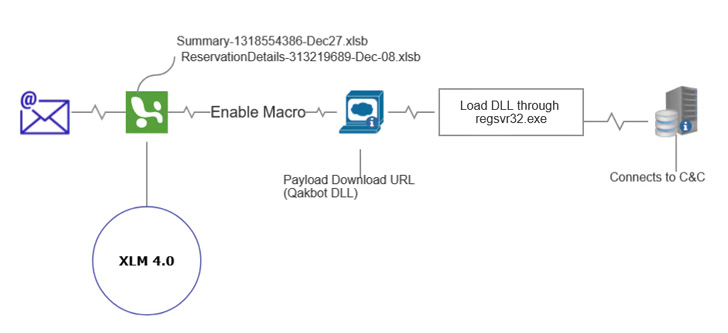
“Qakbot is a adaptable post-exploitation tool that incorporates numerous levels of protection evasion methods built to lessen detections,” Fortinet disclosed in December 2021.

“Qakbot’s modular structure and infamous resiliency in the deal with of common signature-centered detection make it a attractive first selection for numerous monetarily enthusiastic groups (cyber criminals).”
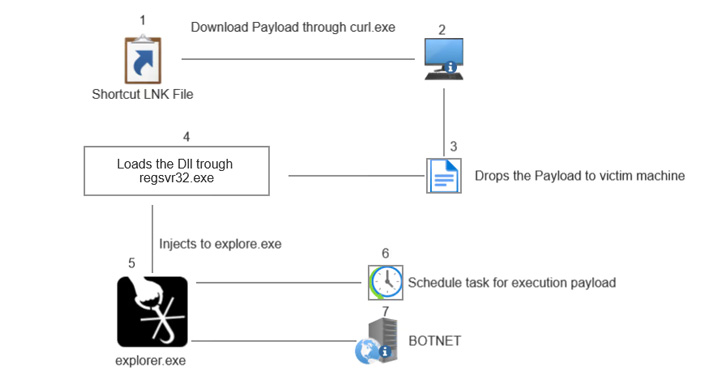
The shifting ways adopted by the malware from XLM macros in early 2022 to .LNK files in May well is witnessed as an try to counter Microsoft’s plans to block Office macros by default in April 2022, a final decision it has considering that quickly rolled back again.
In addition, further more modifications include the use of PowerShell to down load the DLL malware and a swap from regsvr32.exe to rundlll32.exe to load the payload, in what the researchers explained as a “very clear indicator of Qakbot evolving to evade updated security tactics and defenses.”
Observed this posting appealing? Comply with THN on Facebook, Twitter and LinkedIn to go through more unique articles we publish.
Some elements of this posting are sourced from:
thehackernews.com

 Microsoft Releases Fix for Zero-Day Flaw in July 2022 Security Patch Rollout
Microsoft Releases Fix for Zero-Day Flaw in July 2022 Security Patch Rollout