Cybersecurity researchers have uncovered new variants of the ChromeLoader data-thieving malware, highlighting its evolving aspect set in a small span of time.
Primarily made use of for hijacking victims’ browser queries and presenting advertisements, ChromeLoader came to gentle in January 2022 and has been dispersed in the form of ISO or DMG file downloads marketed by means of QR codes on Twitter and no cost gaming sites.
ChromeLoader has also been codenamed Choziosi Loader and ChromeBack by the broader cybersecurity neighborhood. What can make the adware notable is that it really is fashioned as a browser extension as opposed to a Windows executable (.exe) or Dynamic Url Library (.dll).

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The bacterial infections typically function by attractive unsuspecting buyers into downloading film torrents or cracked movie games via malvertising campaigns on pay back-for every-set up web sites and social media.
In addition to requesting invasive permissions to obtain browser details and manipulate web requests, it is also developed to capture users’ search engine queries on Google, Yahoo, and Bing, proficiently letting the threat actors to harvest their on the web actions.
Whilst the very first Windows variant of ChromeLoader malware was noticed in January, a macOS variation of the malware emerged in March to distribute the rogue Chrome extension (model 6.) via sketchy disk picture (DMG) files.
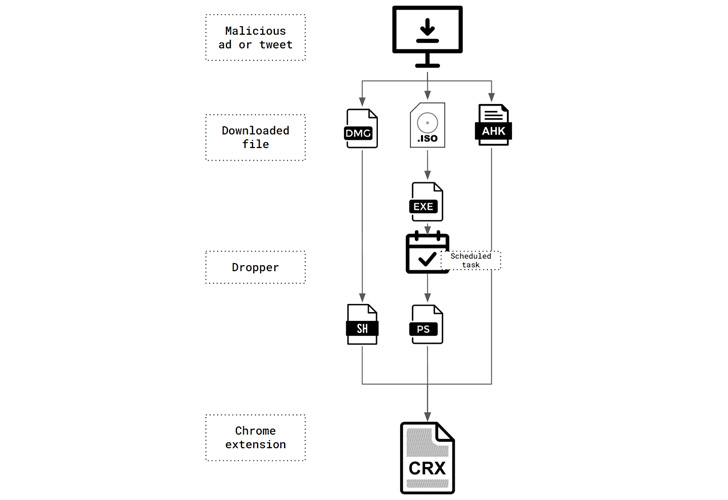
But a new analysis from Palo Alto Networks Device 42 indicates that the earliest regarded attack involving the malware happened in December 2021 working with an AutoHotKey-compiled executable in place of the later on-noticed ISO information.
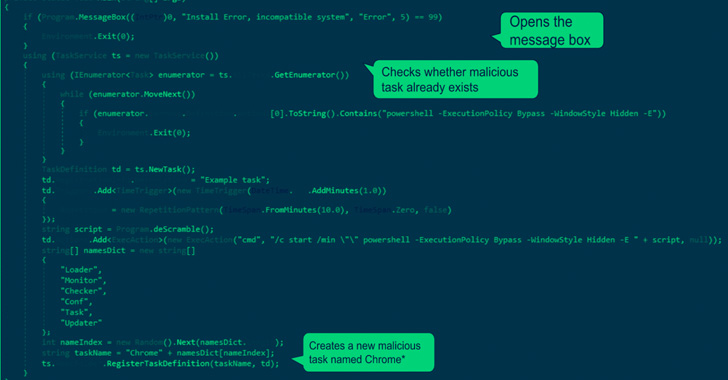
“This malware was an executable file created utilizing AutoHotKey (AHK) — a framework made use of for scripting automation,” Device 42 researcher Nadav Barak stated, incorporating it was applied to fall “version 1.” of the browser include-on.

This 1st model is also mentioned to absence obfuscation abilities, a element that has been picked up in subsequent iterations of the malware to conceal its intent and destructive code.
Also observed given that March 2022 is a formerly undocumented campaign employing the 6. version of the Chrome extension and depends on an ISO picture that contains a seemingly benign Windows shortcut, but, in reality, functions as a conduit to launch a hidden file in the mounted impression which deploys the malware.
“This malware demonstrates how established cybercriminals and malware authors can be: In a brief time time period, the authors of ChromeLoader released various different code versions, utilized several programming frameworks, improved options, advanced obfuscators, fastened issues, and even adding cross-OS support concentrating on both equally Windows and macOS,” Barak reported.
Located this write-up exciting? Abide by THN on Facebook, Twitter and LinkedIn to read through more exclusive content we article.
Some sections of this write-up are sourced from:
thehackernews.com

 What is cyber insurance and should your business buy into it?
What is cyber insurance and should your business buy into it?