Editor’s Notice: This set of evaluations initially appeared in June 2020. To discover out extra about SC Labs, speak to Adrian Sanabria at [email protected]
This thirty day period, SC Labs assessed a number of id and obtain administration methods. This evaluate will come at a suitable time with the recent gatherings surrounding COVID-19 and the worldwide shift to doing the job from residence. The classic, identified perimeter has grown more and more immaterial in excess of the several years. The unparalleled, planet-huge scramble to work remotely has emphasized that the beforehand acknowledged perimeter is nearly non-existent.
These hoping instances have mercilessly highlighted a selection of cybersecurity weaknesses across industries. It is our sincere hope that these critiques find our viewers in a condition of proactive thanks diligence rather of a submit-incident scramble pursuing a lesson figured out the tricky way. The identification and obtain management answers reviewed in this article guard the proverbial gates of critical group sources, examining the IDs of every person that makes an attempt to enter, guaranteeing identities match close-consumer promises and privileged entry is enough for entry. Without having this cybersecurity bouncer to guard the door to your methods, destructive actors have a no cost go into critical programs and knowledge.
Merchandise Group Opener

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
This month, SC Labs seemed at a handful of solutions within just the identity and accessibility management (IAM) space, which collectively perform as an organization gateway among conclusion-end users and critical corporation facts with centralized access control of cloud, on-premises and legacy purposes and means. The emphasis here is on the word collectively. Even though these alternatives practically completely present core capabilities this kind of as authentication and authorization, the merchandise we assessed are most successful when deployed alongside at least a single other IAM alternative. A number of of these goods previously have designed-in integration to aid one a further.
Onboarding buyers onto the platform, in most conditions, is automatic with a wide assortment of directory integrations. Bisynchronous associations in between the identification system and supported directories will take the guide operate nearly completely out of the palms of administrators and dramatically lessens the complexity of implementation and time-to-worth.
Some of this month’s products and solutions may run on the frontend with MSSP functionality whilst a paired identification and access management answer operates in the backend. This particular use case and form of deployment enables a seamless change between IAM methods without having the require to retrain stop-end users. A 3rd style of merchandise, YubiKey (hardware), can include an added layer of id security operating as a crucial to the backend id and accessibility administration lock.
We see the industrywide pattern of incorporating artificial intelligence and machine mastering with identity options as perfectly. State-of-the-art capabilities this sort of as consumer conduct analysis empower dynamic assessments of, and responses to, varying risk at the consumer or session stage. A baseline understanding of envisioned person conduct (time of day, IP handle, place, etcetera.) enables the flagging of anomalous habits.
Identification and access management goods enrich regular login qualifications with several security abilities which include password management and examination, solitary indicator-on and multifactor authentication. Some of the methods have password vaults so that conclude users may possibly securely retail store organization credentials. Password administration keeps tabs on the frequency with which passwords are reused and the inherent security of people passwords according to size and complexity. One sign-on streamlines application and resource access serving as a central, unified login portal. This encourages end end users to use long and intricate passwords simply because only need to sign in once to accessibility all an organization’s methods alternatively of having to log into every solitary particular person resource. Some products and solutions even allow authentication at the workstation degree.
Identification and obtain management items are essential to company security across industries and significantly enrich present security investments. In addition to bringing in an additional layer of security and going a move farther with info loss avoidance, their abilities and options can maximize productivity and general return on expense.
Decide on of the Litter
Yubico YubiKey 5Ci delivers the least complicated and best amount of security obtainable for an identification resolution that is so purchaser welcoming. If there ended up an ease-of-use classification, this would gain by a mile. The a person-touch YubiKey encounter comes with a massive ecosystem of integrations, a reduced total cost of ownership, and a considerable return on investment, generating Yubico YubiKey an SC Labs Greatest Acquire.
Okta Identification Cloud is a versatile alternative with an comprehensive integration network that handles each and every id use case for any technology. Okta reliably and efficiently boosts productiveness and security, driving profitability and growth to improve total return on financial commitment and to reduce the overall price tag of ownership, earning this our SC Labs Encouraged product or service for this month’s spherical of testing.
June critiques
Auth0
JumpCloud
LogMeIn LastPass Id
Microsoft Azure Energetic Directory (Azure Ad)
Okta Identity Cloud
OneLogIn Reliable Practical experience System (TEP)
Simeio Id Orchestrator
Yubico YubiKey 5Ci
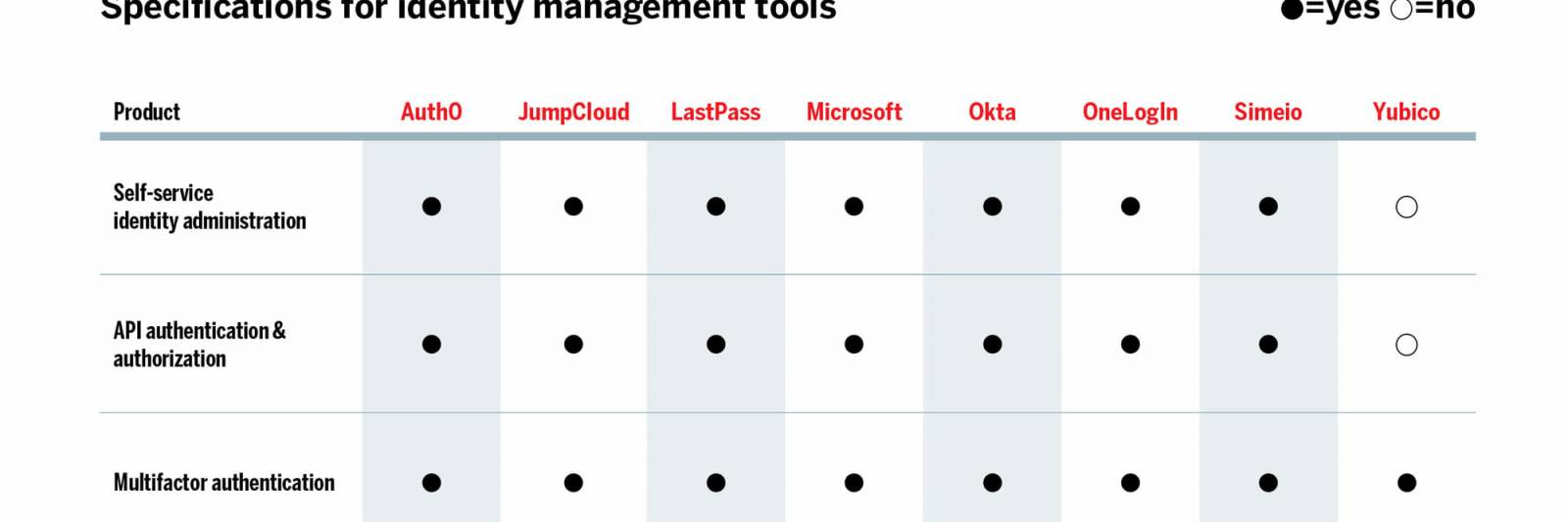
Simply click on the chart beneath for the complete-sizing version
Some pieces of this article are sourced from:
www.scmagazine.com

 SC Product Reviews: Identity & Access Management
SC Product Reviews: Identity & Access Management