A critical security flaw has been disclosed in Amazon Elastic Container Registry (ECR) Community Gallery that could have been perhaps exploited to stage a multitude of attacks, in accordance to cloud security agency Lightspin.
“By exploiting this vulnerability, a destructive actor could delete all photographs in the Amazon ECR Community Gallery or update the picture contents to inject malicious code,” Gafnit Amiga, director of security investigate at Lightspin, said in a report shared with The Hacker News.
“This malicious code is executed on any equipment that pulls and operates the impression, whether or not on user’s regional equipment, Kubernetes clusters or cloud environments.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

ECR is a container graphic registry service managed by Amazon Web Expert services, enabling end users to bundle code as Docker photographs and deploy the artifacts in a scalable fashion. General public repositories hosted on ECR are shown in what’s called the ECR General public Gallery.
“By default, your account has go through and compose access to the repositories in your general public registry,” Amazon notes in its documentation. “However, IAM users involve permissions to make phone calls to the Amazon ECR APIs and to push illustrations or photos to your repositories.”
But the issue identified by Lightspin intended that it could be weaponized by external actors to delete, update, and generate poisoned versions of reputable pictures in registries and repositories that belong to other AWS accounts by using benefit of undocumented inside ECR Public APIs.
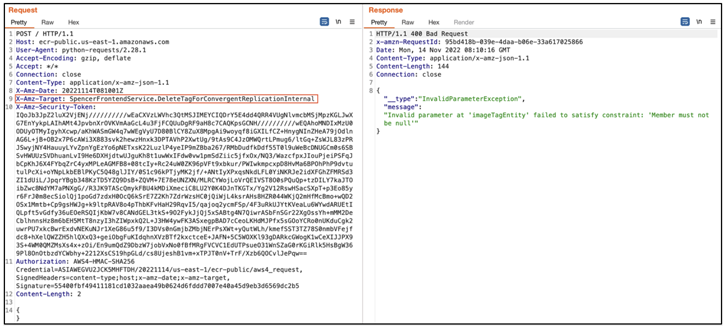
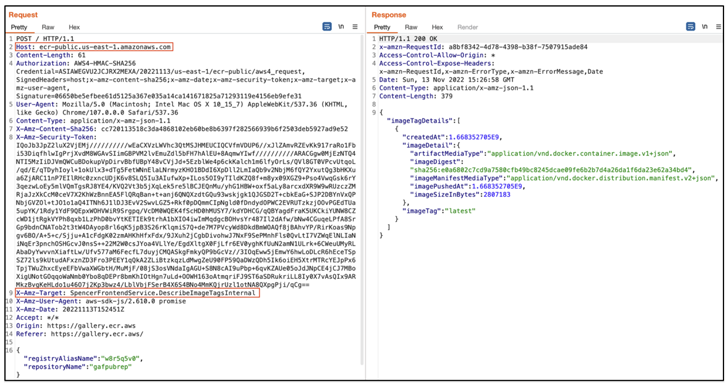
This is attained by getting short-term credentials using Amazon Cognito to authorize requests to the inside APIs and activate the motion to delete pictures utilizing “DeleteImageForConvergentReplicationInternal,” or alternatively force a new image through the “PutImageForConvergentReplicationInternal” motion.
Lightspin characterized the flaw as an instance of “deep program supply chain attack.”
Amazon has because deployed a fix to take care of the weak point as of November 16, 2022, a lot less than 24 hrs right after it was documented, indicative of the severity of the dilemma. No consumer motion is demanded.
“This vulnerability could possibly direct to denial-of-provider, facts exfiltration, lateral motion, privilege escalation, data destruction, and other multivariate attack paths that are only restricted by the craftiness and targets of the adversary,” Amiga mentioned.
“A malicious actor could poison preferred visuals, all even though abusing the trust model of ECR Public as these pictures would masquerade as getting confirmed and consequently undermine the ECR Public provide chain.”
Found this article appealing? Comply with us on Twitter and LinkedIn to study much more unique information we publish.
Some components of this short article are sourced from:
thehackernews.com


 Uber says compromised third-party to blame for data breach
Uber says compromised third-party to blame for data breach