A Linux variant of a backdoor identified as SideWalk was applied to target a Hong Kong college in February 2021, underscoring the cross-system skills of the implant.
Slovak cybersecurity firm ESET, which detected the malware in the university’s network, attributed the backdoor to a country-state actor dubbed SparklingGoblin. The unnamed college is reported to have been already targeted by the group in Might 2020 for the duration of the pupil protests.
“The group consistently qualified this corporation above a prolonged period of time of time, productively compromising a number of vital servers, including a print server, an email server, and a server used to control pupil schedules and course registrations,” ESET said in a report shared with The Hacker Information.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

SparklingGoblin is the name offered to a Chinese sophisticated persistent menace (APT) team with connections to the Winnti umbrella (aka APT41, Barium, or Wicked Panda). It is principally recognised for its attacks focusing on numerous entities in East and Southeast Asia at least considering that 2019, with a distinct focus on the tutorial sector.
In August 2021, ESET unearthed a new piece of custom Windows malware codenamed SideWalk that was completely leveraged by the actor to strike an unnamed computer retail organization primarily based in the U.S.
Subsequent conclusions from Symantec, element of Broadcom software package, have joined the use of SideWalk to an espionage attack team it tracks under the moniker Grayfly, when pointing out the malware’s similarities to that of Crosswalk.
“SparklingGoblin’s Methods, Techniques and Procedures (TTPs) partly overlap with APT41 TTPs,” Mathieu Tartare, malware researcher at ESET, advised The Hacker News. “Grayfly’s definition presented by Symantec appears to be to (at minimum partially) overlap with SparklingGoblin.”
The latest exploration from ESET dives into SideWalk’s Linux counterpart (originally called StageClient in July 2021), with the analysis also uncovering that Specter RAT, a Linux botnet that came to light-weight in September 2020, is in point a Linux variant of SideWalk as properly.
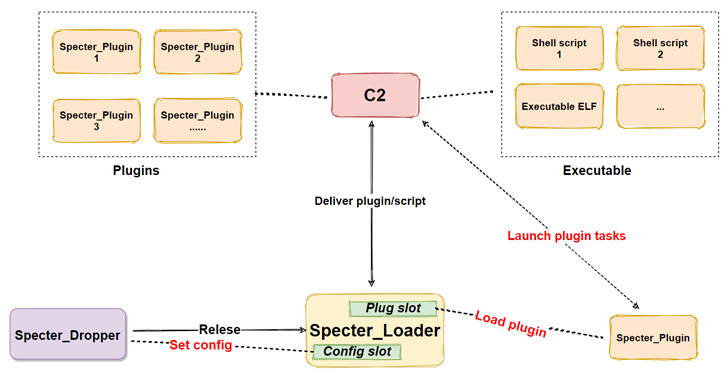
Aside from numerous code similarities among the SideWalk Linux and different SparklingGoblin instruments, just one of the Linux samples has been uncovered making use of a command-and-handle tackle (66.42.103[.]222) that was beforehand utilised by SparklingGoblin.

Other commonalities involve the use of the identical bespoke ChaCha20 implementation, a number of threads to execute just one distinct endeavor, ChaCha20 algorithm for decrypting its configuration, and an identical useless fall resolver payload.
Inspite of these overlaps, there are some major changes, the most noteworthy currently being the switch from C to C++, addition of new built-in modules to execute scheduled responsibilities and assemble technique facts, and variations to 4 instructions that are not handled in the Linux model.
“Because we have seen the Linux variant only after in our telemetry (deployed at a Hong Kong college in February 2021) a single can consider the Linux variant to be significantly less prevalent — but we also have significantly less visibility on Linux programs which could clarify this,” Tartare claimed.
“On the other hand, the Specter Linux variant is applied towards IP cameras and NVR and DVR products (on which we have no visibility) and is mass unfold by exploiting a vulnerability on these devices.”
Located this write-up exciting? Comply with THN on Fb, Twitter and LinkedIn to browse additional exceptional information we write-up.
Some elements of this posting are sourced from:
thehackernews.com

 How to Do Malware Analysis?
How to Do Malware Analysis?