A Sydney man has been sentenced to an 18-thirty day period Group Correction Purchase (CCO) and 100 hours of local community service for trying to get benefit of the Optus information breach very last calendar year to blackmail its shoppers.
The unnamed person, 19 when arrested in Oct 2022 and now 20, utilised the leaked documents stolen from the security lapse to orchestrate an SMS-primarily based extortion scheme.
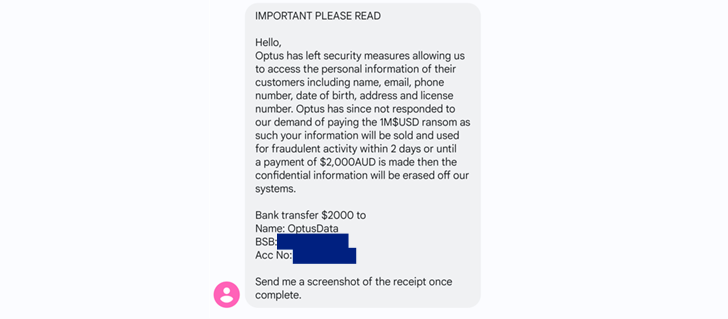
The suspect contacted dozens of victims to threaten that their private data would be bought to other hackers and “employed for fraudulent activity” except if an AU$ 2,000 payment is created to a financial institution account underneath their regulate.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The scammer is stated to have despatched the SMS messages to 92 men and women whose facts was element of a more substantial cache of 10,200 records that was briefly posted in a legal discussion board in September 2022,
The Australian Federal Law enforcement (AFP), which released Operation Guardian subsequent the breach, claimed there is no proof that any of the influenced consumers transferred the demanded volume.
Following his arrest, the offender pleaded responsible in November 2022 to two counts of using a telecommunications network with intent to commit a serious offense.
“The legal use of stolen facts is a critical offense and has the probable to lead to substantial harm to the local community,” AFP Commander Chris Goldsmid claimed.
The Australian telecom assistance company suffered a significant hack previous calendar year, with passport data and Medicare quantities pertaining to nearly 2.1 million of its latest and former consumers exposed.
Observed this report exciting? Observe us on Twitter and LinkedIn to read a lot more special content we article.
Some sections of this short article are sourced from:
thehackernews.com

 #SOOCon23: UK Government Urges Industry Input on Software Security Policy
#SOOCon23: UK Government Urges Industry Input on Software Security Policy