The U.S. Cybersecurity and Infrastructure Security Company (CISA) is warning of a handful of unpatched security vulnerabilities in MiCODUS MV720 World-wide Positioning Technique (GPS) trackers outfitted in over 1.5 million vehicles that could guide to distant disruption of critical operations.
“Profitable exploitation of these vulnerabilities could let a remote actor to exploit obtain and achieve command of the world wide positioning method tracker,” CISA mentioned. “These vulnerabilities could influence entry to a automobile fuel supply, motor vehicle management, or let locational surveillance of automobiles in which the unit is put in.”
Offered on sale for $20 and produced by the China-centered MiCODUS, the company’s monitoring devices are utilized by significant corporations in 169 countries spanning aerospace, energy, engineering, governing administration, production, nuclear electricity plant, and delivery sectors.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The top rated countries with the most buyers include things like Chile, Australia, Mexico, Ukraine, Russia, Morocco, Venezuela, Brazil, Poland, Italy, Indonesia, Uzbekistan, and South Africa.
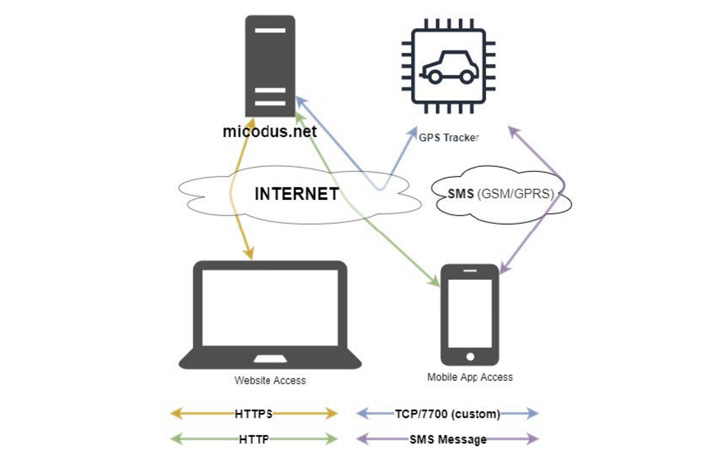
The issues, which had been determined throughout the training course of a security audit by BitSight, could also be possibly abused to monitor individuals devoid of their knowledge, disable motor vehicles, and even pose countrywide security implications in light-weight of the simple fact that militaries and regulation enforcement organizations use the trackers for true-time checking.
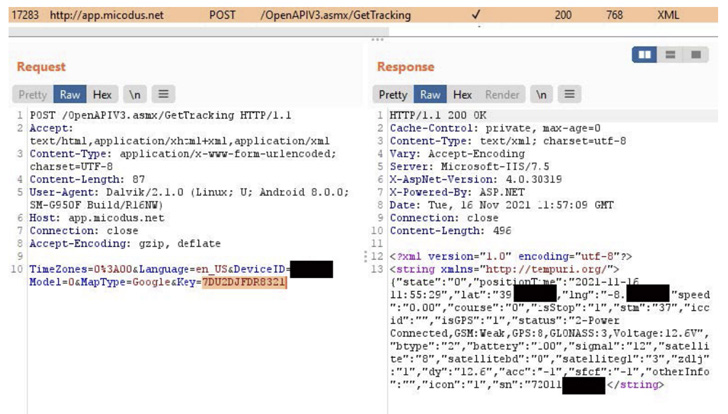
“A nation-state adversary could potentially exploit the tracker’s vulnerabilities to collect intelligence on navy-connected movements such as supply routes, standard troop movements, and recurring patrols,” BitSight scientists pointed out.
The listing of flaws that were disclosed to MiCODUS in September 2021 is below –
- CVE-2022-2107 (CVSS score: 9.8) – Use of a really hard-coded grasp password that could enable an unauthenticated attacker to carry out adversary-in-the-middle (AitM) attacks and seize command of the tracker.
- CVE-2022-2141 (CVSS score: 9.8) – Broken authentication scheme in the API server that enables an attacker to control all site visitors in between the GPS tracker and the first server and obtain regulate.
- No assigned CVE (CVSS rating: 8.1) – Use of a preconfigured default password “123456” that enables attackers to access any GPS tracker at random.
- CVE-2022-2199 (CVSS score: 7.5) – A mirrored cross-site scripting (XSS) vulnerability in the web server that could guide to the execution of arbitrary JavaScript code in the web browser.
- CVE-2022-34150 (CVSS rating: 7.1) – An obtain regulate vulnerability stemming from Insecure Direct Item Reference (IDOR) that could final result in the exposure of sensitive details.
- CVE-2022-33944 (CVSS rating: 6.5) – A case of authenticated IDOR vulnerability that could be leveraged to crank out Excel experiences about unit exercise.

In a nutshell, the flaws could be weaponized to attain accessibility to area, routes, gas cutoff instructions as nicely as the capacity to disarm several functions this sort of as alarms.
But with no workaround in sight, people of the GPS tracker in concern are suggested to acquire steps to limit exposure or alternatively cease making use of the equipment and disable them completely until a repair is manufactured offered by the company.
“Having a centralized dashboard to check GPS trackers with the ability to help or disable a motor vehicle, check speed, routes and leverage other functions is valuable to many men and women and businesses,” the researchers mentioned. “Nonetheless, this kind of performance can introduce severe security challenges.”
Located this report exciting? Abide by THN on Facebook, Twitter and LinkedIn to read a lot more special material we post.
Some components of this article are sourced from:
thehackernews.com


 Dealing With Alert Overload? There’s a Guide For That
Dealing With Alert Overload? There’s a Guide For That