The Vice Society ransomware actors have switched to still a further custom ransomware payload in their recent attacks aimed at a wide range of sectors.
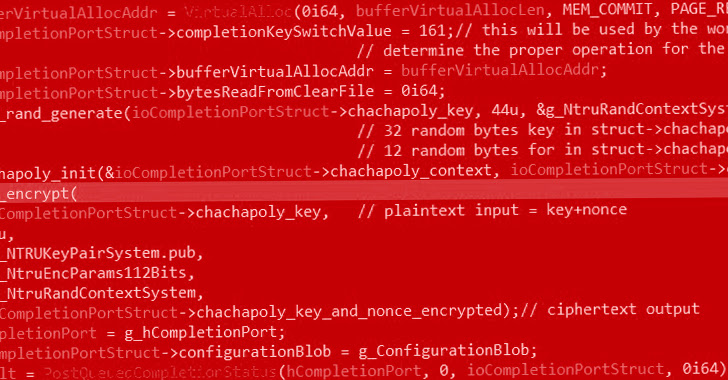
“This ransomware variant, dubbed ‘PolyVice,’ implements a robust encryption plan, working with NTRUEncrypt and ChaCha20-Poly1305 algorithms,” SentinelOne researcher Antonio Cocomazzi mentioned in an examination.
Vice Modern society, which is tracked by Microsoft under the moniker DEV-0832, is an intrusion, exfiltration, and extortion hacking group that 1st appeared on the risk landscape in May well 2021.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Not like other ransomware gangs, the cybercrime actor does not use file-encrypting malware designed in-house. Rather, it’s identified to deploy third-party lockers these kinds of as Howdy Kitty, Zeppelin, and RedAlert ransomware in their attacks.
For every SentinelOne, indications are that the threat actor driving the customized-branded ransomware is also marketing equivalent payloads to other hacking crews dependent on PolyVice’s substantial similarities to ransomware strains Chily and SunnyDay.

This implies a “Locker-as-a-Company” which is supplied by an mysterious menace actor in the variety of a builder that makes it possible for its purchasers to customise their payloads, which includes the encrypted file extension, ransom observe file title, ransom take note content material, and the wallpaper text, amongst many others.
The change from Zeppelin is probably to have been spurred by the discovery of weaknesses in its encryption algorithm that enabled researchers at cybersecurity business Device221b to devise a decryptor in February 2020.
Aside from utilizing a hybrid encryption plan that combines uneven and symmetric encryption to securely encrypt data files, PolyVice also can make use of partial encryption and multi-threading to speed up the method.
It’s really worth pointing out that the not long ago found out Royal ransomware employs very similar strategies in a bid to evade anti-malware defenses, Cybereason disclosed last week.
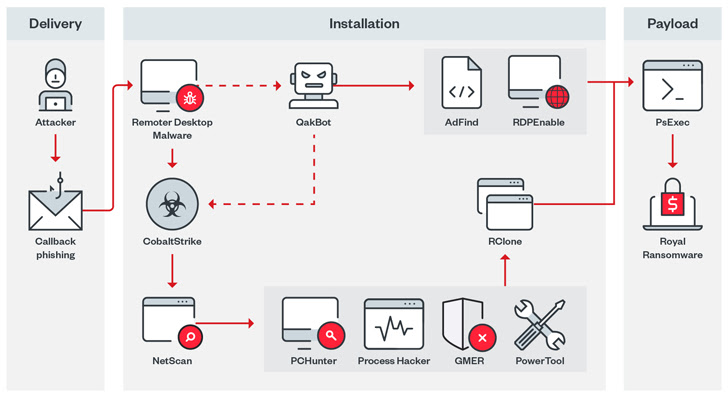
Royal, which has its roots in the now-defunct Conti ransomware operation, has also been noticed to use phone back again phishing (or phone-oriented attack shipping and delivery) to trick victims into setting up distant desktop application for preliminary obtain.
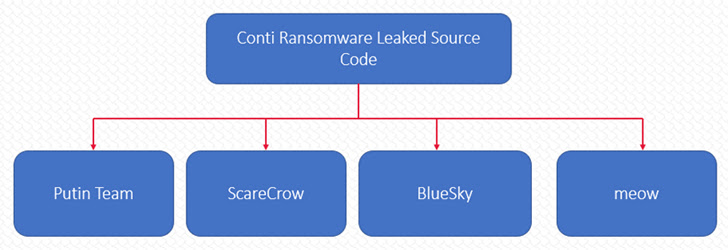
In the in the meantime, the leak of Conti source code previously this yr has spawned a number of new ransomware strains these types of as Putin Staff, ScareCrow, BlueSky, and Meow, Cyble disclosed, highlighting how these kinds of leaks are generating it a lot easier for threat actors to launch distinct offshoots with minimum amount investment.
“The ransomware ecosystem is frequently evolving, with the development of hyperspecialization and outsourcing constantly rising,” Cocomazzi mentioned. “This development in direction of specialization and outsourcing presents a considerable risk to businesses as it permits the proliferation of subtle ransomware attacks.”
Found this post appealing? Adhere to us on Twitter and LinkedIn to study more distinctive information we post.
Some components of this posting are sourced from:
thehackernews.com

 Zerobot Botnet Devs Add New Functionality
Zerobot Botnet Devs Add New Functionality