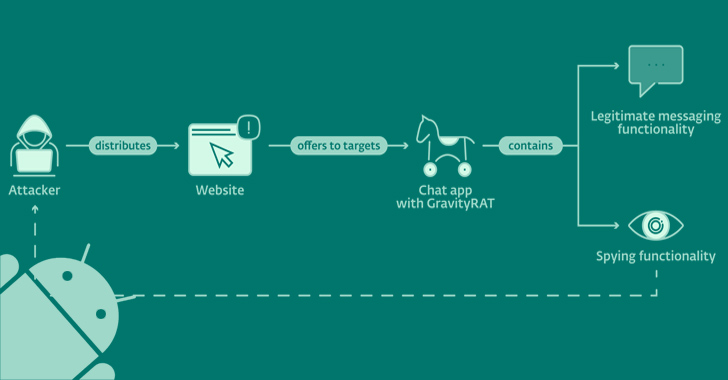
An up-to-date model of an Android remote entry trojan dubbed GravityRAT has been observed masquerading as messaging apps BingeChat and Chatico as element of a narrowly specific campaign because June 2022.
“Notable in the newly uncovered marketing campaign, GravityRAT can exfiltrate WhatsApp backups and obtain instructions to delete documents,” ESET researcher Lukáš Štefanko explained in a new report printed today.
“The malicious applications also provide legitimate chat functionality based mostly on the open-source OMEMO Prompt Messenger app.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
GravityRAT is the identify offered to a cross-platform malware that is capable of focusing on Windows, Android, and macOS devices. The Slovak cybersecurity company is monitoring the activity beneath the title SpaceCobra.

The risk actor is suspected to be centered in Pakistan, with the latest attacks involving GravityRAT targeting military staff in India and among the Pakistan Air Power by camouflaging it as cloud storage and leisure apps, as disclosed by Meta very last month.
The use of chat applications as a entice to distribute the malware was earlier highlighted in November 2021 by Cyble, which analyzed a sample named “SoSafe Chat” that was uploaded to the VirusTotal database from India.
The chat applications, while not accessible on Google Participate in, are distributed through rogue web sites advertising free of charge messaging providers: bingechat[.]net and chatico[.]co[.]uk.
“This group utilized fictitious personas — posing as recruiters for both of those authentic and phony defense providers and governments, army personnel, journalists, and girls seeking to make a passionate relationship — in an attempt to establish believe in with the people today they focused,” Meta reported in its Quarterly Adversarial Danger Report.
The modus operandi suggests that possible targets are contacted on Facebook and Instagram with the goal of tricking them into clicking on the backlinks and downloading the malicious applications.
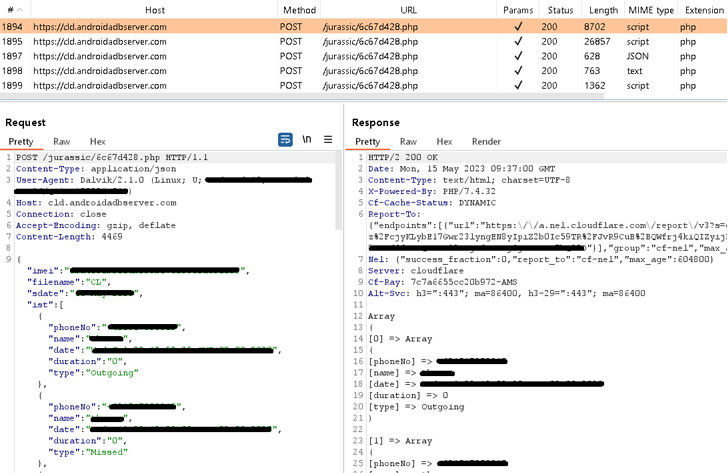
GravityRAT, like most Android backdoors, requests for intrusive permissions beneath the garb of a seemingly legitimate app to harvest delicate data this kind of as contacts, SMSes, phone logs, data files, location info, and audio recordings with out the victim’s awareness.
The captured info is eventually exfiltrated to a remote server under the risk actor’s regulate. It really is really worth noting that employing the app is conditional on acquiring an account.
Future WEBINAR🔐 Mastering API Security: Comprehending Your Accurate Attack Surface area
Discover the untapped vulnerabilities in your API ecosystem and choose proactive measures in direction of ironclad security. Join our insightful webinar!
Be a part of the Session.wn-button,.wn-label,.wn-label:just afterdisplay:inline-block.test_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px good #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-best-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-proper-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimensions:13pxmargin:20px 0font-bodyweight:600letter-spacing:.6pxcolor:#596cec.wn-label:just afterwidth:50pxheight:6pxcontent:”border-major:2px sound #d9deffmargin: 8px.wn-titlefont-measurement:21pxpadding:10px 0font-excess weight:900textual content-align:leftline-height:33px.wn-descriptiontextual content-align:leftfont-dimension:15.6pxline-top:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-size:15pxcolor:#fff!importantborder:0line-peak:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-excess weight:500letter-spacing:.2px
What will make the new model of GravityRAT stand out is its potential to steal WhatsApp backup information and acquire recommendations from the command-and-management (C2) server to delete call logs, get in touch with lists, and files with certain extensions.
“These are really certain instructions that are not typically viewed in Android malware,” Štefanko pointed out.
The progress will come as Android end users in Vietnam have been victimized by a new strain of banking cum stealer malware acknowledged as HelloTeacher that employs authentic messaging applications like Viber or Kik as a include to siphon sensitive facts and have out unauthorized fund transfers by abusing the accessibility services API.
Also learned by Cyble is a cloud mining scam that “prompts people to download a malicious software to get started mining,” only to just take advantage of its permissions to the accessibility companies to get delicate details from cryptocurrency wallets and banking applications.
The financial trojan, codenamed Roamer, exemplifies the craze of using phishing web-sites and Telegram channels as distribution vectors, thus proficiently widening the probable victim pool.
“Consumers should training warning and refrain from pursuing suspicious cryptocurrency mining channels on platforms like Telegram, as these channels can guide to considerable economical losses and compromise sensitive private information,” Cyble stated.
Observed this report fascinating? Stick to us on Twitter and LinkedIn to examine a lot more unique content material we article.
Some elements of this short article are sourced from:
thehackernews.com

 New Research: 6% of Employees Paste Sensitive Data into GenAI tools as ChatGPT
New Research: 6% of Employees Paste Sensitive Data into GenAI tools as ChatGPT